What’s a digital footprint? Everything you do online leaves behind a trail. Each email you send, website you visit, and transaction you complete is part of a growing database of information linked to your identity.
This can impact your life and livelihood in various ways, so it’s important to learn how to manage and protect your digital footprint.
What is a digital footprint?
A digital footprint is the data trail created by your online activities and the traces you intentionally or unintentionally leave behind. Over time, these digital footprints form a detailed impression of your identity that is more accessible and permanent than many people realize. Understanding the scope and impact of this long-lasting record helps you make informed decisions about your online behavior and security practices.
Want to learn more about using Dashlane Password Manager at home or at work?
Types of digital footprints
How does a digital footprint work? Whether intentionally or unintentionally, you’re adding to your digital footprint every time you use the internet. Some digital footprints are left behind through anonymous site visits and searches, while others are directly traceable to your name, address, email address, and other personal information. The digital footprint definition can be broken into two general categories:
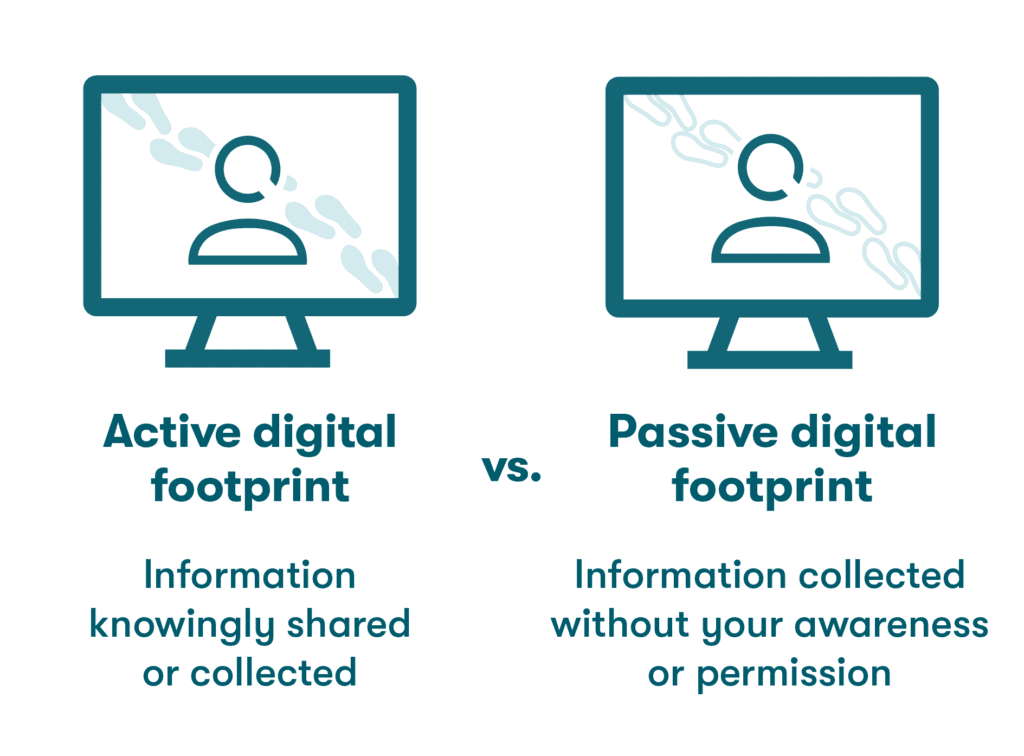
- Active digital footprints: A digital footprint is considered active when you’re aware of the information being shared or collected. This type of footprint is created by activities such as social media posts, filling out forms, or publishing an article. When you log in to an account or website under a registered username, any feedback you share becomes part of your active digital footprint.
- Passive digital footprints: Unlike active footprints, passive digital footprints are left behind without your awareness or participation. Much of this information is gathered based on the associated Internet Protocol (IP) address. Your internet browser and any websites you visit continually collect background data based on your activity.
Why are digital footprints important?
Digital footprints are living records that follow us throughout our lives, so it’s important to be aware of their contents and what others see. Things like social media posts, online comments, and uploaded images and files paint a picture that shapes our reputations. Anything we post on social media can also be misjudged or misunderstood, no matter how innocent it seems.
Colleges and employers are among the institutions that review digital footprints regularly as part of their decision-making processes. At the same time, your digital footprint can become a trail of information for hackers to customize phishing attacks or commit identity theft. Leaving too much of a digital footprint makes you more vulnerable to cybercriminals.
Digital footprint examples
The digital footprint meaning is best described through some common examples. These everyday activities create active and passive footprints that we can examine to understand their importance:
- Web browsing: Each time you connect to the internet, the websites you visit log the IP address associated with your connection, while search engines like Google or Yahoo store your history. Web browsing in private or Incognito mode offers a bit more privacy since your browsing history and cookies are deleted after each session, although your internet service provider (ISP) will still record the sites you visited. Deleting your browsing history only removes information from your local browser and device. Records of the sites you visit are still maintained by the website owners.
- Cookies: What does it mean when you accept cookies? Despite the innocent name, this digital footprint example is actually a small text file stored on your browser by the site you visited. Cookies add convenience by remembering login information and shopping preferences, but they also grant companies permission to use your information as they see fit. Although they are usually harmless, you should always decline cookies from suspicious or unsecured websites.
- Online shopping: Your online shopping history, including any items you have purchased or clicked on, is stored by the vendor. This aspect of your digital footprint is useful for marketers creating targeted ads that cater to your history and preferences. In some cases, the vendor will also store your credit card number and other personal information, which can leave you vulnerable if they’re subject to a data breach.
- Mobile banking: The shift to digital, online methods for nearly all banking transactions makes financial history another important element of your digital footprint. Payment and account information on the cloud produces a centralized record of financial activity. Many financial institutions also track location information along with transaction history. This helps them detect and prevent fraudulent transactions while creating a more thorough digital footprint.
- Downloads: Each time you download a file, the file type, origin, and metadata associated with the file contribute to a profile that becomes more detailed with each subsequent download. Your browsing history includes past downloads that define your interests and activities. The insight that can be gained from this portion of your digital footprint makes it a popular target for cybercriminals. In the event of a data breach.
- Social media: Your social media activity establishes much of your active digital footprint. What sets social media apart from other sources is the depth and breadth of information shared. This includes photos, comments, commentary on sensitive topics, and the names of friends, relatives, and colleagues. These details can become a gold mine for hackers attempting to guess user credentials or steal identities.
- Sending emails: The emails we send and receive are a digital footprint example that combines high volume with detailed information on habits, history, location, and finances. They also reveal personal and professional contacts and relationships. Email addresses are central to digital footprint security since they double as usernames for many account types and provide a convenient access point for marketers, scammers, and hackers attempting to establish contact.
How is your digital footprint used?
If you’ve ever searched for a familiar name and found volumes of information (or nothing), you have explored digital footprint use. Whether a search is based on innocent curiosity, professional interest, or malicious intent, the availability and content of a digital footprint should not be left to chance.
Common uses for digital footprints include:
- Employment screening: 92% of recruiters say they use internet searches to gather information on candidates. They might look for positive signs like involvement in professional networks and volunteer organizations, as well as inappropriate or inflammatory information that could be lurking in social media accounts. This underscores the importance of digital footprint maintenance to weed out anything that might be viewed as a negative.
- Targeted advertising: The practice of targeted advertising utilizes personalized communication tailored to customer demographics, behaviors, and preferences. Businesses and advertisers assemble customer profiles based on their digital footprints. Cookies, location data, and other data sources are fed into algorithms to determine what ads or campaigns are most likely to be successful.
- Cybercrimes: The goal of most cybercrimes is to steal or compromise sensitive information like passwords, account numbers, social security numbers, or trade secrets for financial gain. Much of the information cybercriminals seek can be traced to our digital footprints. Safeguarding their contents provides protection from:
—Hacking: Common hacking tactics, such as brute-force attacks and credential stuffing, rely on weak, reused, or unsecurely shared passwords to gain unauthorized account access. Many weak passwords include information like names, addresses, and other personal information that can be found on social media and other readily available digital footprint sources.
—Phishing: The social engineering tactic known as phishing uses personalized emails to trick recipients into providing information or clicking on malicious links. The believability of phishing emails can be enhanced using details from the recipient’s digital footprint, including contact names and interests shared in social media profiles. - Legal issues: As detailed records of online activity, digital footprints formed by emails, geolocation data, and social media posts are converted into evidence (or alibis) related to whereabouts, criminal intent, fraud, and other activities during criminal investigations and trials. Concerns over privacy, data authenticity, and chain of custody issues have led to more discussions and pushback over what digital evidence should be admissible in criminal proceedings.
- Personal searches: Digital footprints are an important source of information for anyone with concerns or questions about their children’s activities, new friends, or potential love interests. Online dating apps have soared in popularity as more people utilize these convenient platforms to meet new partners. These apps contribute to their members’ digital footprints while highlighting the need for users to complete their own digital footprint investigations to weed out dating scams carried out by cybercriminals and imposters.
How to minimize your digital footprint
Is there a way to erase your digital footprint entirely? Data retention policies for ISPs, browsers, and retailers make it nearly impossible to delete your digital footprint, but there are some proactive steps you can take to scale it back:
- Delete cookies regularly to prevent online businesses from tracking your activities.
- Deactivate old social media accounts to remove readily available personal information.
- Delete any other accounts, memberships, or services that you’re no longer using.
- Don’t provide your name or email address when you complete online surveys or reviews.
- Delete email accounts you’re no longer actively using and unsubscribe from any newsletters associated with the email address.
- Delete passwords stored on web browsers where they’re vulnerable to hacking and data breaches. Then, migrate them to a stand-alone password manager protected by encryption.
How to protect your digital footprint
While eliminating all accounts might not be practical, there are some additional steps you can take to increase your digital footprint awareness, control the viewable data, and prevent information from falling into the wrong hands.
Digital footprint maintenance improves when you:
- Use search engines to review your online presence. If others are searching your name to verify your credibility, it’s a good idea for you to do the same. Searching for your own name can reveal how your profile appears to outsiders and whether there is incorrect or unflattering information posted that you need to resolve. Most importantly, searching for your own name might reveal warning signs of identity theft.
- Limit your data sharing. You’re in control of your active digital profile. Anything you post might eventually be seen by friends, colleagues, or a prospective employer, so err on the side of caution when it comes to sharing personal details online. This approach also helps to elevate your security profile if an organization you’ve shared data with is impacted by a data breach.
- Check your privacy settings. Laws and regulations for online data privacy include rules for collecting, storing, and sharing customer information. These laws help you manage your digital footprint by limiting the ways information can be distributed without your consent. Each social media platform also includes customizable privacy settings that let you decide who can view images and posts. Setting your profiles to private gives you more control over who can access the personal information and photos you share.
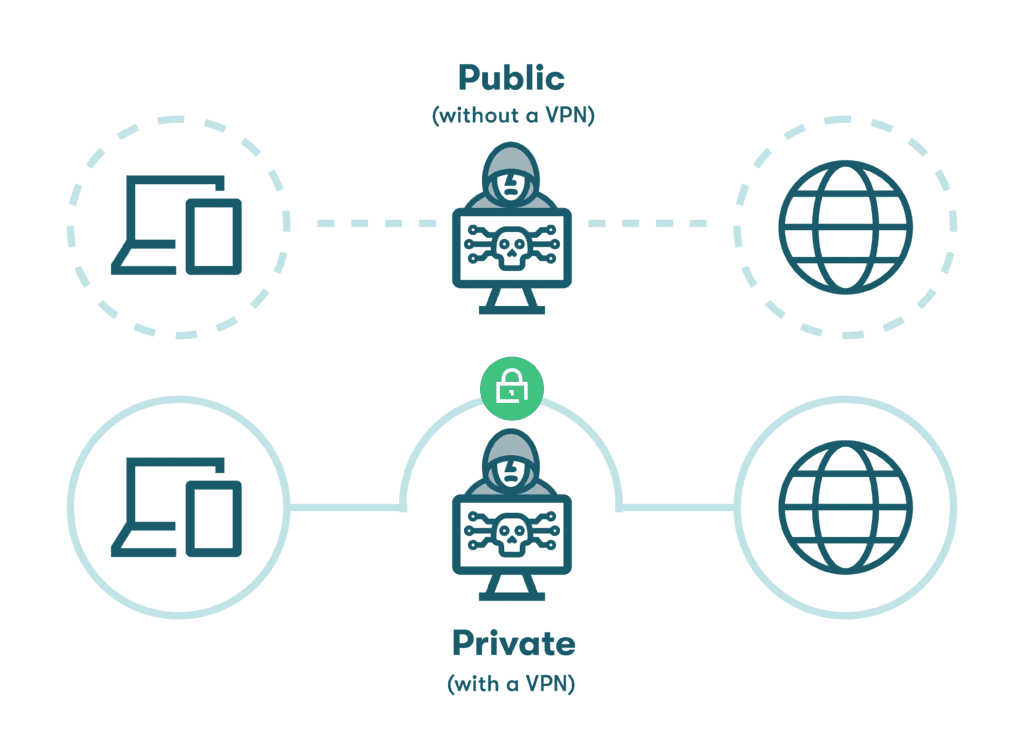
- Use a VPN on public WiFi. Malls, airports, cafés, and other public settings can be subject to hacking tactics like man-in-the-middle attacks designed to intercept your personal information. A virtual private network (VPN) should always be used on public networks to protect your privacy and accounts. The VPN encrypts all data going into or out of your device and routes it through a secure portal while masking your IP address so you can browse the internet privately.
- Use 2-factor authentication (2FA). The security practice known as 2-factor authentication (2FA) typically uses a second identifier, such as a code sent through an app or text, to provide an added layer of security during the login process. Since a hacker is unlikely to have both your credentials and device available, the additional time required to log in is balanced by enhanced account and privacy protection.
- Use a password manager. The automatic generation and autofill of strong, encrypted passwords improves security and convenience by eliminating the need to manually create and store passwords. A password manager safeguards important aspects of your digital footprint by storing your information in a secure vault and enabling 2FA for an additional layer of security.
Dashlane also provides Dark Web Monitoring, a secure password-sharing portal, and a Password Health score to continually track your weak, reused, and compromised passwords.
References
- Dataprot, “What is a Digital Footprint: Everything You Need To Know,” May 2023.
- Reputation X, “What is a digital footprint?” March 2023.
- Network World, “What is an IP address? And what is your IP address?” May 2022.
- DMN, “Social Media Footprint Facts: What You Should Know,” December 2021.
- Dashlane, “Are Private Browsers Really Private + Tips for Secure Browsing,” March 2023.
- Reader’s Digest, “3 Times You Shouldn’t “Accept Cookies” on a Site,” November 2021.
- Dashlane, “One of the Most Common Data Breaches Your Organization Can Prevent with One Step,” November 2021.
- Dashlane, “Are Digital Wallets Safe?” June 2023.
- Backblaze, “Metadata: Your File’s Hidden DNA and You,” February 2020.
- Bitdefender, “What goes online, stays online: How a negative digital footprint can affect your life,” March 2022.
- Dashlane, “How to Erase Saved Browser Passwords: Step-by-Step Guide,” November 2022.
- Dashlane, “What To Do If a Scammer Has Access To Your Email Address,” March 2023.
- Dashlane, “6 Things a Safe Username Should Always Do,” February 2023.
- Zippia, “What Percentage of Employers Check Social Media?” December 2022.
- Forbes, “The Truth In User Privacy And Targeted Ads,“ February 2022.
- Dashlane, “11 Cyber Threats To Be Aware of & Defend Against,” April 2023.
- Dashlane, “Data Breach or Hack? Know the Difference,” June 2021.
- Dashlane, “What the Hack Is Phishing?” March 2020.
- Bipartisan Policy Center, “What Your Digital Footprint Reveals and Who is Watching,” December 2022.
- Digitalfootprintcheck, “Protecting Yourself from Online Dating Scams with Digital Footprint Check,” 2023.
- Dashlane, “What Is Data Privacy & Why Is It Important?” April 2023.
- Dashlane, “A Beginner’s Guide to Two-Factor Authentication,” August 2022.
- Dashlane, “Our Guide to Data Privacy,” 2023.
Sign up to receive news and updates about Dashlane
Related articles