What Many Recent Data Breaches Have in Common
If an ounce of prevention is worth a pound of cure, the best way to avoid data breaches is by understanding and avoiding the weaknesses targeted by hackers. So, what are the common causes of data breaches?
How common are data breaches, and why are they an issue?
No matter how you slice it, data breach statistics are staggering. Over 41 million accounts were leaked worldwide in the first quarter of 2023 alone, and the average cost of a breach is approaching the $4 million mark. With small businesses targeted 43% of the time, no one is immune.
Some patterns have emerged: We now know that at least 50% of confirmed data breaches involve user credentials. Cybercriminals exploit the vulnerabilities caused by weak and reused credentials with tactics such as:
- Brute-force attacks. This tactic uses software to guess credentials over thousands of iterations until an account is accessed. The impact of a brute-force attack is also heightened by reused passwords, since one success might unlock many accounts. Strong, complex passwords reduce the impact of this tactic since they’re harder for hackers (or their algorithms) to guess.
- Credential stuffing. If you’ve ever forgotten your password and then tried plugging in other credentials hoping to guess correctly, then you understand the basic principle behind credential stuffing. As a subset of brute-force attacks, hackers improve their odds by purchasing stolen logins and entering them across various websites. Reused passwords multiply the impact of these tactics by exposing multiple accounts when a match is made.
Want to learn more about using Dashlane Password Manager at home or at work?
Check out our personal password manager plans or get started with a free business trial.
Recent data breach attack examples
The news is full of data breaches, including some involving well-known companies experiencing huge losses, both in data and dollars. Some of the more notable data breaches in recent news include:
- T-Mobile: In April 2023, T-Mobile announced its second data breach of the calendar year. Although the most recent breach was dealt with relatively quickly, the January incident exposed the personal information of 37 million T-Mobile customers.
- U.S. House of Representatives: As proof that no one is immune to data breaches, the U.S. government reported a hacking incident in March 2023 that involved the personal information of 17 current and former members of Congress. Despite ongoing investigations by the FBI and Capitol Police, the culprits and their methods have not yet been identified.
- Pizza Hut: In January 2023, Yum Brands, the parent company of Pizza Hut, KFC, and Taco Bell, experienced a data breach that led to the temporary closure of 300 restaurants. A reported ransomware attack exposed customer information, including names and driver’s license numbers.
- MailChimp: In January 2023, email marketing giant MailChimp reported its second data breach in a six-month period. The intruder used social engineering tactics to convince employees to share their credentials, eventually gaining access to 133 MailChimp customer accounts in the process.
- Norton LifeLock: Over six thousand LifeLock cybersecurity customers had their accounts compromised in the opening weeks of 2023. The unauthorized access is believed to be the result of credential-stuffing tactics. After the cybercriminals infiltrated LifeLock accounts using stolen credentials, they were able to view customer names, phone numbers, and mailing addresses.
- LastPass: In December of 2022, password manager LastPass announced a data breach that exposed the email addresses, phone numbers, IP addresses, billing information, and password manager master passwords of approximately 3% of their business customers. The cybercriminals managed to steal encrypted customer data, along with encryption keys, from the company’s third-party cloud storage provider. If you were impacted by the Lastpass breach, here’s the easiest way to switch to a safer password manager.
- Uber: In September 2022, an 18-year-old hacker gained full access to the internal systems and Slack communication channel of ride-sharing giant Uber. Apparently, the hacker used social engineering tactics, one of the most common causes of data breaches, to trick an Uber IT employee into sharing his credentials.
- Twitter: In June 2021, an update to Twitter’s code made it possible to obtain the username of a Twitter user simply by providing their phone number or email address. Although this bug was fixed six months later, over 200 million Twitter usernames and emails were found to be for sale on the black market in January 2023.
7 common causes of data breaches
Studying recent incidents sheds light on the common causes of data breaches, but diagnosing their origins is often challenging. Many data breaches result from a combination of two or more hacking tactics, while the root cause of others remains a mystery. The following are among the most widely documented causes of recent data breaches:
- Reused passwords: Repeating old credentials is common because we all want to make our passwords easier for us to remember. Unfortunately, reusing passwords also diminishes password security, since multiple accounts can be breached if a reused password is compromised, making it a leading cause of data breaches. Password reuse decreases our password health and makes us much more vulnerable to credential stuffing and brute-force attacks since the impact of one successful match is multiplied.
- Weak passwords: Passwords that are too short, lack complexity, or are too predictable are also one of the most common causes of data breaches, since they can be guessed easily by hackers using automated software to support their attacks. Increasing the number of password characters from 8 to 12 raises the number of possible combinations from 200 billion to 95 quadrillion, making it much more difficult for hackers to decode. A strong password should also omit phrases like family names or addresses that are associated with your identity.
The best way to create strong, unpredictable passwords consistently is by using the password generator feature of a password manager. - Unpatched apps: Updates to apps and operating systems also include patches to correct known security issues. Hackers take advantage of unpatched software and out-of-date operating systems to gain unauthorized access. They might even scour the internet to find unpatched systems to target. Applying recommended patches and completing system maintenance on time helps to strengthen your overall security posture and prevent data breaches.
- Malware: Short for malicious software, malware includes many types of software that can interfere with a computer’s function. Malware variants include adware, worms, and viruses. A malware attack becomes more dangerous when the hacker’s intent is to steal data or render a device unusable until a ransom is paid.
—Spyware: The form of malware commonly known as spyware installs itself on a device and collects information like credit card numbers and passwords while sending it back to the hacker. Since the device may appear to be functioning normally, spyware attacks can be hard to detect.
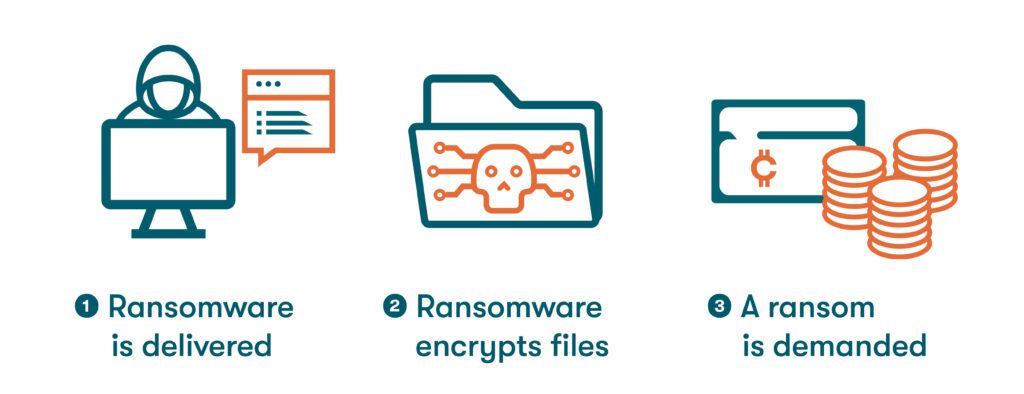
—Ransomware: The malware variant known as ransomware is used to deny an individual or company access to their own files until a ransom is paid, typically using cryptocurrency because it’s anonymous, fast, and sometimes hard to trace. Backing up and encrypting important files regularly lessens the impact of ransomware attacks.
- Social engineering. Recent data breaches including Uber and MailChimp involved social engineering tactics, which use a combination of basic psychology and readily available company and personal information. Targets are tricked into divulging confidential information like usernames, passwords, and account numbers. Phishing emails disguised as messages from reputable sources are a notorious example, but social engineering methods also include phone calls, text messages, and even in-person contact.
- Insider threats: These threats originate within the workplace, including:
—Human error that occurs when employees lose or misplace files, data, and company devices or fall for malicious phishing attacks that originate from outside company walls.
—Ex-employees who retain their credentials and use them to inflict damage on company assets. Sharing passwords in the workplace unsecurely can lead to inadequate password visibility when employees leave the organization.
—Disgruntled employees who tamper with, destroy, or steal company data.
—Bring your own device (BYOD) programs that allow employees to transfer malware and other cybersecurity threats to the company network from their personal devices. - Physical attacks: As the name implies, physical security breaches involve direct, unauthorized contact with servers, devices, and other individuals. Multi-layered security systems, including fencing, security cameras, and badges are used to protect data centers from physical attacks. Social engineering and physical attacks converge when cybercriminals use methods like tailgating to slip in undetected behind authorized users and shoulder surfing to steal information over the victim’s shoulder.
How can I protect my company?
Reviewing and responding to common data breach causes can help keep your company safe. While preventative security measures like antivirus software, firewalls, and intrusion detection systems are valuable, recent events point to the human element as a leading cause of data breaches. Your cybersecurity plan should focus on eliminating bad habits like password reuse while educating employees, family members, and friends on social engineering tactics that rely on our tendency to trust others when they appear credible.
How Dashlane protects you from data breaches
Dashlane is a password manager that helps to protect passwords and other personal information from data breaches. Standard features include 2-factor authentication (2FA), a Password Health Score, 256-bit AES encryption, and Dark Web Monitoring to continually scan the dark recesses of the internet and ensure your credentials have not been compromised. Our patented zero-knowledge architecture ensures that no one, including Dashlane, can access your private information. If Dashlane were to be breached , the cybercriminals would not see your unencrypted data.
Good password hygiene and strong cybersecurity habits help you avoid a data breach. To find out how computer users in different regions stack up when it comes to compromised, weak, and reused passwords, take a look at Password Health Scores around the world.
References
- DataProt, “Data Breach Statistics That Will Make You Think Twice Before Filling Out an Online Form,” March 2023.
- Surfshark, “Data breach statistics 2023’Q1 vs. 2022’Q4,'' May 2023.
- Dashlane, “One of the Most Common Data Breaches Your Organization Can Prevent with One Step,” November 2021.
- Dashlane, “What is Credential Stuffing?” September 2020.
- Dashlane, “What the Hack is a Brute Force Attack?” February 2020.
- Security, “T-Mobile confirms second data breach in 2023,” September 2022.
- CBS News, “At least 17 members of Congress had sensitive information exposed in data breach,” March 2023.
- TechCrunch, “Norton LifeLock says thousands of customer accounts breached,” January 2023.
- Security Week, “Yum Brands Discloses Data Breach Following Ransomware Attack,” April 2023.
- TechCrunch, “Mailchimp says it was hacked — again,” January 2023.
- Dashlane, “The Most Notable Breaches That Kicked Off 2023,” February 2023.
- Dashlane, “Everything You Should Know About the Social Engineering Attack at Uber,” September 2022.
- Dashlane, “Twitter’s 200 Million-User Email Leak: What to Know and How to Protect Your Info,” January 2023.
- Dashlane, “How Password Reuse Leads to Cybersecurity Vulnerabilities,” May 2023.
- Dashlane, “6 Tips to Create Strong, Secure Passwords in a Digital World,” March 2023.
- Dashlane, “Resist hacks by using Dashlane's password generator tool,” 2023.
- Dashlane, “Why You Should Keep Your Apps Updated,” March 2022.
- Dashlane, “What the Hack Is Malware?” February 2020.
- Dashlane, “How to Prevent Ransomware Attacks on Your Devices,” March 2023.
- Dashlane, “5 Reasons Why You Should Back Up Your Computer Often,” May 2023.
- Dashlane, “Interview With a Hacker: Rachel Tobac Tells You How to Defend Yourself From…Well, Her!” March 2021.
- Information Week, “75% of Insider Cyber Attacks are the Work of Disgruntled Ex-Employees: Report,” July 2022.
- Dashlane, “Don’t Take the Bait — Password Managers Can Help Shield You From Phishing Attacks,” November 2020.
- Dashlane, “9 BYOD Security Best Practices for Small and Medium-sized Businesses,” May 2023.
- Maryville University, “Types of Security Breaches: Physical and Digital,” 2023.
- Dashlane, “How To Create a Small Business Cybersecurity Plan That Works,” February 2023.
- Dashlane, “Trusted Personal Password Manager,” 2023.
- Dashlane, “Putting Security First: How Dashlane Protects Your Data,” January 2023.
- Dashlane, “2-factor authentication (2FA) in Dashlane,” 2023.
- Simplilearn, “What Is AES Encryption and How Does It Work?” February 2023.
- Dashlane, “A Deep Dive into Dashlane's Zero-Knowledge Security,” 2023.
- Dashlane, “A look at Password Health Scores around the world in 2022,” 2022.
Sign up to receive news and updates about Dashlane
