As cybercrime and phishing tactics grow more advanced, there’s always the chance a scammer could get access to your email address and create a dangerous cybersecurity situation that you need to respond to immediately.
If a scammer has access to your email, a few simple steps can minimize the potential loss of privacy and security.
How to tell if your email has been hacked
What can a scammer do with your email? Stolen credentials allow a scammer to send malicious messages or malware links to your contacts, extract personal or financial information from your saved messages, or get your friends and family to send money to them under false pretenses.
Here are some telltale signs that your email account has been hacked:
- You can’t log in. One of the first things a scammer might do if they access your email account is change your password. If you’re certain you’re entering the correct username and password for your account and still can’t log in, this could be a red flag.
- Your account is sending emails you didn’t write. It can be a rude awakening when a friend or family member asks you if you sent them an email that doesn’t sound familiar. Is this email a scammer? If you hear your email account is suddenly delivering mysterious links or spam messages, it could be compromised.
- Your folders have been emptied or modified. Your email provider will not delete, move, or reorganize saved files or messages. If you notice any changes in your file structure and you do not share the email account password with anyone, you may have been visited by a scammer.
- Your device is behaving strangely. A compromised email account alone won’t cause your computer or device to slow down or behave strangely. However, a hacker may have already installed malware on your device to get access to your email account, which could account for the drop-off in performance.
- You receive a security alert. Employers, internet service providers, and cybersecurity apps will often provide you with a security alert if your account information is compromised. These alerts should always be taken seriously, and you should change your password right away if you have been impacted by a data breach.
- Your information appears on the dark web. Despite being vigilant, you may not always realize when your email account has been compromised. Dark web monitoring is a valuable tool that scans the hidden recesses of the internet for your personal information and credentials. For example, Dashlane’s Dark Web Monitoring immediately alerts subscribers if their password(s) or account information are detected and need to be changed.

What to do if a scammer has access to your email
When your email account is compromised, it means a scammer has access to your account. They could already be sending fraudulent messages or malware links to your contacts. Notify as many of your contacts as possible using an alternate email address or by texting or calling. After you’ve contained the immediate threat, follow these tips to thwart the scammer and minimize their impact:
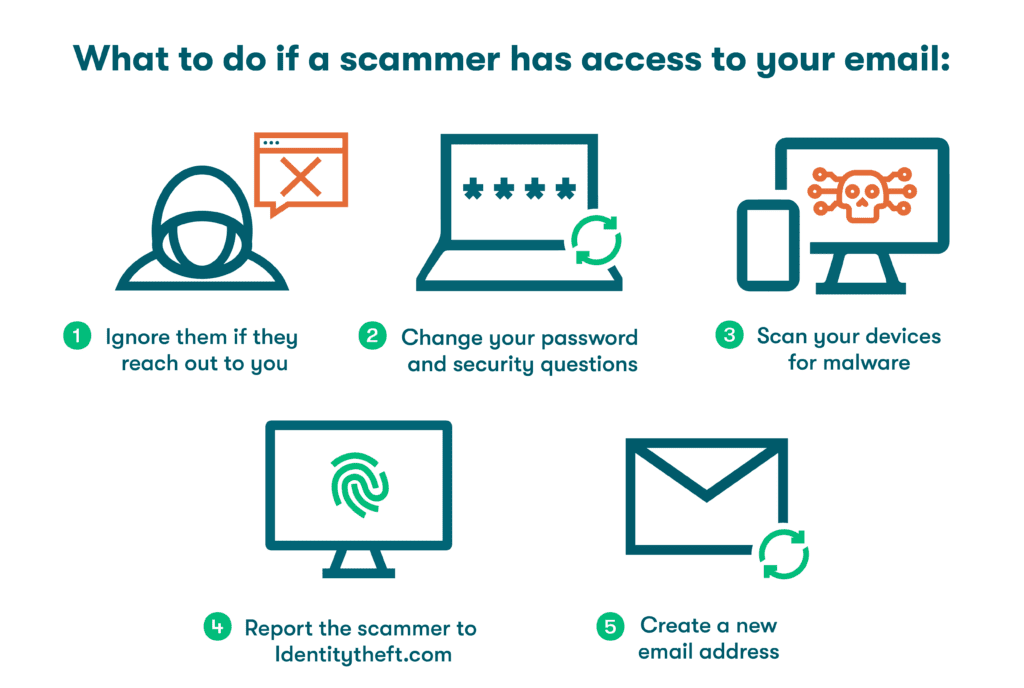
- Ignore them if they reach out to you
One of the worst ways to react to a scammer is by engaging them in their scam. They may try to contact you, even using your own email address, but responding to them will not stop or discourage their behavior. Instead, any response will simply confirm another “live” contact to exploit. Be sure to mark any emails from the scammer as spam. - Change your email password and security questions
Changing passwords at predefined time intervals is no longer considered a best practice. In fact, the NIST discourages these periodic resets, since minor changes to existing passwords have little value and are easily guessed by hackers. However, if your email account has been compromised, you need to change your password and security questions immediately. - Scan your device for malware
Any changes you make to your account are of little value if your device has been infected by malware. If you don’t already have antivirus or anti-malware software installed, now’s the time to download it. Run a complete system scan as soon as possible to isolate and remove any infected files. - Report the scammer to identitytheft.com
Scammers hiding out in cyberspace and changing their location frequently can be difficult to track, but they should be reported anyway. Free services like identitytheft.com help you deactivate affected accounts, sign up for free credit monitoring, and learn how to report a scammer email. - Create a new email address
To be completely safe, you can follow the steps above, then start fresh with a brand new email address. Since the average person in the U.S. has 100-150 accounts linked to their email address, you will also need to locate and update all of these connected accounts.
How to prevent scammers from accessing your email
As the saying goes, an ounce of prevention is worth a pound of cure. The best way to manage a hacked email account is by preventing it from being hacked in the first place. These additional tips and tricks will help keep you safe from future email breaches:
- Use 2-factor or multifactor authentication
2-factor authentication (2FA) makes your email account more secure by requesting a second identifier, such as a unique code sent through an app or text message. This might add a few seconds to your login time, but it will make it nearly impossible for a scammer to access your account without having your device. Multi-factor authentication (MFA) uses two or more identifiers, sometimes including biometric factors like fingerprints or facial recognition.
- Check your backup contact method
Most of us don’t think about or update our recovery email address or backup contact method often—if at all. Make sure the email address and phone number you provide are active and up to date. These backup methods become important when you are locked out of your account and need to reset your password or receive security alerts.
- Be on the alert for phishing attacks
How are emails hacked? A phishing attack, often in the form of an unsolicited email, is a social engineering tactic used to trick recipients into sharing account information or passwords. Some also include links to spyware or keyloggers that intercept private communications. Poor grammar, spelling errors, and URLs that do not match the company website can be signs of a phishing attack, but these signs are not always present—phishing and social engineering tactics are growing ever more advanced.

- Use a password manager
A password manager protects all your important accounts by encrypting passwords and account information and storing your information in a secure vault. This can help thwart hacking tactics—like credential stuffing, brute-force attacks, and phishing—that prey on weak email passwords. A password manager also allows you to store, share, and update all your most important passwords from one secure app.
How Dashlane protects your email from scammers
Dashlane provides seamless password generation that helps keep all your credentials strong, unique, and safe from scammers. A secure vault safely encrypts and protects your passwords, and zero-knowledge architecture ensures no one—not even Dashlane—can access your information. Our Dark Web Monitoring scans the depths of the internet for your credentials, including up to five email addresses, and alerts you if your passwords or account information are detected and need to be changed.
References
- Dashlane, “6 Things a Safe Username Should Always Do,” February 2023.
- Dashlane, “5 Things to Know Before Sharing Passwords With Your Partner,” February 2021.
- Dashlane, “What the Hack Is Malware?” February 2020.
- Dashlane, “What is a Security Alert?” December 2019.
- Dashlane, “Always Change Your Passwords After a Breach,” March 2020.
- Dashlane, “How to Shine a Light on the Dark Web,” June 2022.
- GovTech, “Hacked or Scammed?” July 2022.
- NetSec News, “Summary of the NIST Password Recommendations for 2021,” November 2022.
- Dashlane, “How Strong Is Your Password & Should You Change It?” August 2022.
- Dashlane, “Resist hacks by using Dashlane's password generator tool,” 2023.
- Dashlane, “From Maiden Names to School Mascots—The Best Ways to Use Security Questions,” September 2021.
- Cybernews, “How to find all accounts linked to your email to protect your privacy,” February 2023.
- Dashlane, “A Beginner’s Guide to Two-Factor Authentication,” August, 2022.
- Dashlane, “A Complete Guide to Multifactor Authentication,” November 2022.
- Dashlane, “4 Steps to Secure Your Google and Gmail Accounts,” November 2021.
- Dashlane, “Why Dashlane Will Never Ask You for Credentials in an Email (Because That’s How Phishing Works),” November 2021.
- Norton, “Spyware: What is spyware + how to protect yourself,” December 2021.
- Dashlane, “Password Management 101,” 2023.
- Dashlane, “What Is Credential Stuffing,“ September 2020.
- Dashlane, “Putting Security First: How Dashlane Protects Your Data,” January 2023.
- Dashlane, “Dark Web Monitoring: Your Employees Are Likely Using Compromised Passwords,” July 2022.
- Dashlane, “You Asked, A Hacker Answered: 7 Questions With Rachel Tobac,” October 2021.
- Dashlane, “Top 8 Most Important Passwords to Change,” April 2023.
- CrowdStrike, “Keyloggers: How They Work and How to Detect Them,” February 2023.
- PCMag, “The Best Malware Removal and Protection Software for 2023,” December 2022.
Sign up to receive news and updates about Dashlane
Related articles