How We Eliminated Virtually All Risky Credentials at Dashlane
At Dashlane, we’re our own first users. Every feature we build goes through rigorous internal testing phases, including broad employee testing known as “dogfooding.” This approach not only ensures quality but also gives us real-world insight into how our product works.
Over the past year, we’ve been actively testing the new credential protection features that comprise the Dashlane Omnix™ platform on ourselves before releasing them to customers.
You might assume that a security company building a password manager would already have a perfect setup—100 percent password hygiene across the board. But the reality is more nuanced.
While our average Password Health score, which factors in weak, reused, and compromised credentials stored in employee vaults, consistently stays above 95 percent, there’s always room for improvement.
Shining a light on shadow credentials
Last year, we launched Credential Risk Detection, which continuously monitors and detects at-risk credential activity in real-time across the entire workforce. When we began rolling out the first versions of the solution internally in the summer of 2024, our security team uncovered some surprising behavior.
Despite every employee actively using Dashlane internally (we deploy it on Day 1 during employee onboarding), we found a significant number of compromised "shadow" credentials—logins used by employees to access various apps, some corporate and others personal.
These weren’t stored in Dashlane vaults, which meant they weren’t being monitored or protected properly. This is where the traditional approaches to password management fall short: they can’t account for credentials not saved in the vault, leaving businesses blind to the shadow IT across their environment.
At the same time, we launched Nudges: Contextual, real-time reminders delivered through platforms such as Slack to alert employees about weak, reused, or compromised passwords. For example, if an employee attempts to sign in to a service with a compromised credential, they’ll be alerted immediately, making them more likely to take action.
We also manually followed up with individuals, not only encouraging them to update their credentials but also promoting better security habits overall.
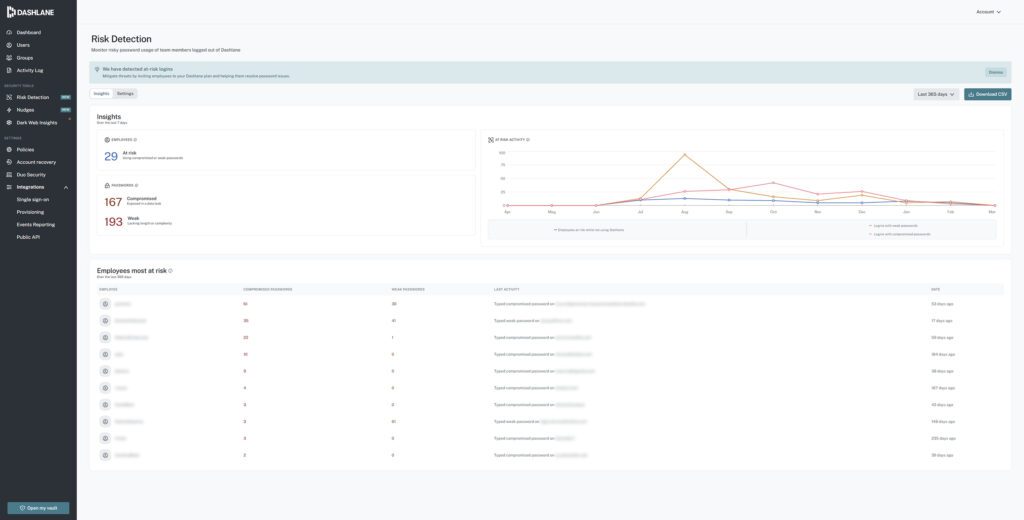
The results were striking. As shown in the redacted screenshot below, our internal use of Dashlane Omnix led to a 75 percent reduction in compromised credentials in use across the organization in the first month of deployment.
Within seven months, we had virtually eliminated all compromised, weak, and reused credentials from our corporate environment.
Improving credential risk security with constant learning
This initiative didn’t just improve Dashlane’s own security posture; it also helped us better understand how to make Omnix even more valuable for IT and security teams.
Since Dashlane is zero knowledge, we don't have access to customer dashboards such as the one above, which makes our internal usage a valuable testing ground to shape the product.
We’ve also heard similar stories from customers. One enterprise customer discovered that their CEO was unknowingly using compromised credentials on personal sites—an eye-opening moment that prompted their leadership to take swift action. A large healthcare organization discovered that a quarter of their users were using compromised and weak passwords to access corporate apps after deploying Dashlane for thousands of employees.
These are just a few examples of how organizations have reduced credential risk with Dashlane, but there are many more. And we’re just getting started.
We're actively expanding the scope of Omnix: Increasing the types of risks we detect, enhancing self-remediation options for employees, and enabling IT and security teams to orchestrate automated responses. We're also investing heavily in AI to accelerate and scale these capabilities.
If you haven’t explored Dashlane Omnix yet, now is the time. Try it for yourself—and stay tuned. We have an exciting roadmap ahead.
Sign up to receive news and updates about Dashlane