How We Engineered a Customizable Rules List for Smarter AI Phishing Protection
At Dashlane, our goal is to help organizations strengthen their defenses against phishing while adapting to their unique environments. Every company has its own systems, internal tools, and workflows—and cybersecurity solutions must fit those realities.
That’s why we built the new Custom Rules List for our AI Phishing Alerts.
Our proprietary AI model detects suspicious sites directly within the Dashlane extension, protecting users from phishing attempts without compromising our zero-knowledge principles.
But we know that security isn’t one-size-fits-all. For some companies, legitimate internal portals or partner sites might look unconventional enough to trigger a phishing warning. Instead of forcing every team to conform to a fixed global policy, we wanted to give admins the ability to customize their Dashlane experience to match their corporate context.
The Custom Rules List lets admins decide how Dashlane should behave for specific domains—whether that means silencing alerts for trusted internal sites or finetuning which warnings employees see. This flexibility empowers organizations to balance protection with usability, maintaining strong security coverage without unnecessary friction.
In this article, we’ll dive into how we designed and built this feature: From the security architecture that keeps every company’s rules private to the engineering choices that make it scalable and future-ready.
Architecting the custom rules system
To turn this idea into reality, we needed a mechanism that could distinguish between global domains—safe for all users—and internal domains that are unique to each organization. This led us to design a two-tier system for managing trusted websites. Each tier serves a different purpose but works together to maintain both usability and security across environments.
The solution is not one, but two distinct allowlists:
- A public list, distributed to every Dashlane extension, without distinction. This list contains known, typically high-traffic domains and is maintained by the Dashlane team.
- A private list for each team (on Dashlane OmnixTM), managed by the admins of each team and distributed only to team members’ devices. This list must comply with our zero-knowledge commitment because internal domains are sensitive data.
From allowlist to custom rules
As we scoped the requirements for our allowlists, an idea emerged: What if admins could do more than just skip phishing alerts based on a domain?
And because most allowlist complexity resides not in its format but in its storage and distribution, turning the allowlist into a much more flexible list of custom rules seemed like a low-effort, high-reward opportunity.
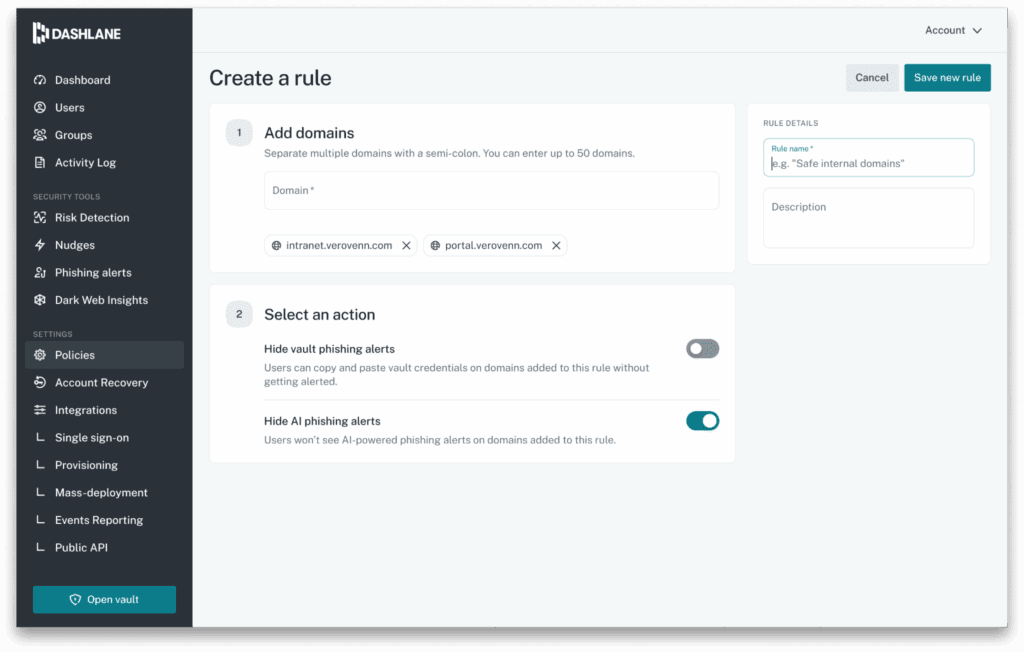
So, what is a custom rule? It’s simple. A custom rule is defined with a list of domains and a list of actions.
- Domains can be thought of as the “enforcement zone” of the rule. If a user visits a domain (or a subdomain of a domain) on the list, the rule is triggered.
- Actions are the outcomes we want to enforce. For now, we only offer two: “Hide AI phishing alerts” and “Hide vault phishing alerts.” However, we built this as a platform, and more actions will be added as more features start using this rules engine.
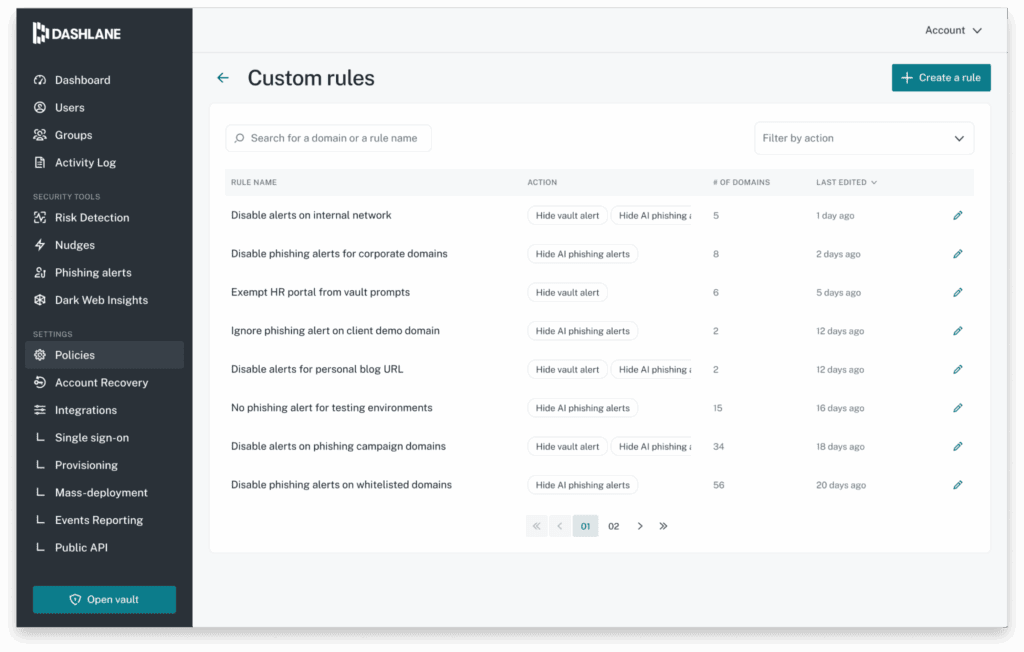
Admins can create new rules and see the list of rules through a dedicated interface in the Admin Console.
Deep dive into the architecture
For a feature like custom rules, the architecture needs to be secure, scalable, and adaptable. Here’s a look at the key decisions we made for our first iteration.
End-to-end encryption
The list of custom rules is encrypted in transit between the extension and the secure enclave through our secure tunnel architecture (an encrypted communication established between a Dashlane extension and a Dashlane secure enclave). Then, the tunnel payload is decrypted by the enclave.
Next, the list of rules is validated, encrypted again, and signed by the enclave using AES-256-CBC-HMAC—this time using a key that’s specific to the team and limited in scope to the encryption/decryption of the rules list. We include a team identifier in the encryption context, which guarantees that, even if a malicious actor gained access to our storage, they couldn't misattribute one team's rules to another.
For an extra layer of protection, when sending the rules to user devices, we don’t send a cleartext list of domains. Instead, we send the hashes of those domains. From there, the extension hashes the current domain and its subdomains and looks for matches. Only the admins will receive the cleartext list of domains when querying the servers for the list.
Optimizing storage
In our system, the ratio of reads to writes is extremely unbalanced because we expect thousands of reads for every single write.
The most frequent operation—getting custom rules for the end users—will happen in the background and, thus, will have no noticeable effect on user experience if it becomes slow. Writes, on the other hand, are triggered by admins from the Admin Console, and slowness there could result in a painful user experience.
So here is our dilemma: Optimize for reads (which, in turn, means optimizing for cost and minimized impact to other services) or optimize for writes (which might have a more noticeable impact on user experience).
Our chosen approach: Optimizing for reads
For this first iteration, we chose a design that optimizes for reads but makes few assumptions besides that: Storing the custom rules in an object storage (AWS S3) with the list of rules encrypted in a single block. This enables us to demonstrate value and put our concept to the test at scale before deciding in what direction to optimize.
We could have used databases like MySQL and DynamoDB (these are commonly used at Dashlane), but their main benefits—like indexing and querying individual fields—are nullified when the data is encrypted as a single, opaque block.
Regarding DynamoDB, something else we had to consider is that DynamoDB items have a size limit of 400KB. This could have become limiting had we decided to store the entire list in a single item. S3 provides a simple, scalable, and cost-effective solution; it’s everything we need until we can test our hypothesis and confirm the value of this feature in the real world.
At this stage, there are still some unknowns about how customers will use this tool in practice. Will they put all the domains in one rule and group by actions? Will they define groups of domains and, for each group, decide what actions should apply to it? How often will they update the rules?
Once we start observing how admins use the tool, we can improve it based on their actual feedback rather than on how we imagine them using it.
Future improvements
This is just the beginning. We already have a few ideas for functional and technical improvements. Which ones get implemented will depend on the feedback we get and the behaviors we observe.
Here are a few examples:
- Smarter polling: We may add a revision number so the enclave can track versions of the rules list. This would allow client apps (extensions and mobile apps) to check for updates more frequently without increasing server load.
- Granular encryption: We may encrypt rules individually. This would reduce the risk of race conditions if two admins edit rules at the same time, though we would need to benchmark the performance impact.
- Database storage: We may move the rules to individual items in DynamoDB. This could make edits even faster, but we need to weigh the latency benefits against the potential overhead of combining items for reads.
- Versioning and history: We may give admins the ability to see and revert to previous versions of their rules.
- More actions: We may expand the platform to support new actions.
- Rule prioritization: We may enable prioritization so admins can manage how rules apply, which will be important as we add more complex and potentially conflicting actions.
The path forward
We began our journey with the critical need to support enterprise customization of our phishing protection features.
This exploration has not only resolved an immediate challenge but has also laid the groundwork for a versatile, general-purpose tool poised to enable a multitude of future capabilities, evolving as we gather real-world insights into its usage.
Our commitment is to continuously enhance and adapt it based on user feedback and observed behaviors, ensuring it remains a robust, effective solution that meets the needs of our customers.
Sign up to receive news and updates about Dashlane