Beyond Convenience: How Autofill Protects You from Online Threats

Autofill is one of the invisible superpowers of a password manager. You barely notice it. It simply gets you into your accounts instantly and securely.
At Dashlane, our ML‑powered autofill engine analyzes millions of websites and countless form permutations to ensure your credentials, payment cards, and personal data are available exactly when you need them. It’s a cornerstone of our product because it combines seamless convenience with stronger security practices, like encouraging unique, complex passwords.
But as with any security feature, while it brings enormous benefits, it must be designed to mitigate risks attackers might try to exploit.
The tradeoffs of autofill
Rather than thinking of autofill in terms of pros and cons, it’s more useful to look at the experience holistically.
Autofill saves you from the constant burden of typing or remembering passwords. This makes it possible to use strong, unique passwords everywhere—a foundation of good digital hygiene. Without autofill, the average Dashlane user would struggle to keep track of their roughly 227 credentials without resorting to weak or reused passwords.
Copy‑paste might be an alternative, but in practice it introduces friction and risk.
The real trade‑off lies between usability and security. Our philosophy is clear: It’s better to provide a secure, simple experience that millions can follow consistently than to design for theoretical perfection that users abandon in practice.
At the same time, any feature that interacts with the open web attracts the attention of attackers. Autofill engines must therefore not only provide convenience but also constantly adapt, staying one step ahead of evolving browser behaviors and manipulation techniques that adversaries try to exploit.
Our mission is to ensure the security benefits far outweigh the risks—and to evolve our defenses continuously.
Clickjacking: A known threat
One technique attackers sometimes use is clickjacking. It works by tricking a user into clicking or typing into an element that looks harmless but is actually hiding a different field or action underneath. For example, you might think you’re clicking a button, but you’re unknowingly clicking submit on a form.
For clickjacking to succeed, an attacker must be able to execute malicious JavaScript on a page you visit. This requires creating a malicious website and luring you to it or exploiting vulnerabilities such as Cross‑Site Scripting (XSS) on a legitimate site. To capture credentials or a session tied to a passkey, the attacker would also need the registered domain to be vulnerable to their exploit.
The risks are real, but they’re limited. In general, clickjacking may at most expose a single matching item in a given interaction—it cannot compromise your entire vault. The vault itself remains encrypted and fully protected at all times.
Oftentimes, exploiting clickjacking also requires a complex chain of conditions to align, which makes it difficult to execute successfully.
How Dashlane defends against clickjacking
We’ve built multiple safeguards to minimize risk:
- Anti‑clickjacking checks: They prevent malicious overlays from triggering autofill.
- Same‑origin policy: By default, Dashlane autofill matches the saved domain, and users can toggle whether to exclude subdomains or not.
- Continuous updates: As browsers and frameworks evolve, we have to review how we adapt our protections to keep pace with new attack variations.
No defense is “set and forget.” Attackers evolve, so our autofill engine evolves too.
Clickjacking attack and defense techniques are rooted in the infrastructure of webpages—browsers and web framework standards. As these systems change and grow, new variations of clickjacking emerge. Their complexity means there is no silver bullet. It’s a game of cat and mouse. Defense techniques must be maintained and refined to stay ahead of this shifting threat landscape. When we discover new clickjacking techniques, we aim to fix those quickly.
Autofill as an anti‑phishing tool
At Dashlane, we’ve taken protection a step further.
Our autofill acts as a silent anti‑phishing check: Credentials won’t fill on a site that doesn’t match your saved domain. Without this safeguard, users often resort to copy‑paste, which shifts the responsibility entirely to them.
Even experts can be tricked—as security researcher Troy Hunt shared from personal experience. That’s why Dashlane went beyond domain matching by introducing phishing alerts.
We issue in the range of 200,000 phishing alerts per month, warning users when credentials don’t align with the site they’re trying to log into. Instead of autofilling or pasting blindly, users must explicitly decide whether to trust the site.
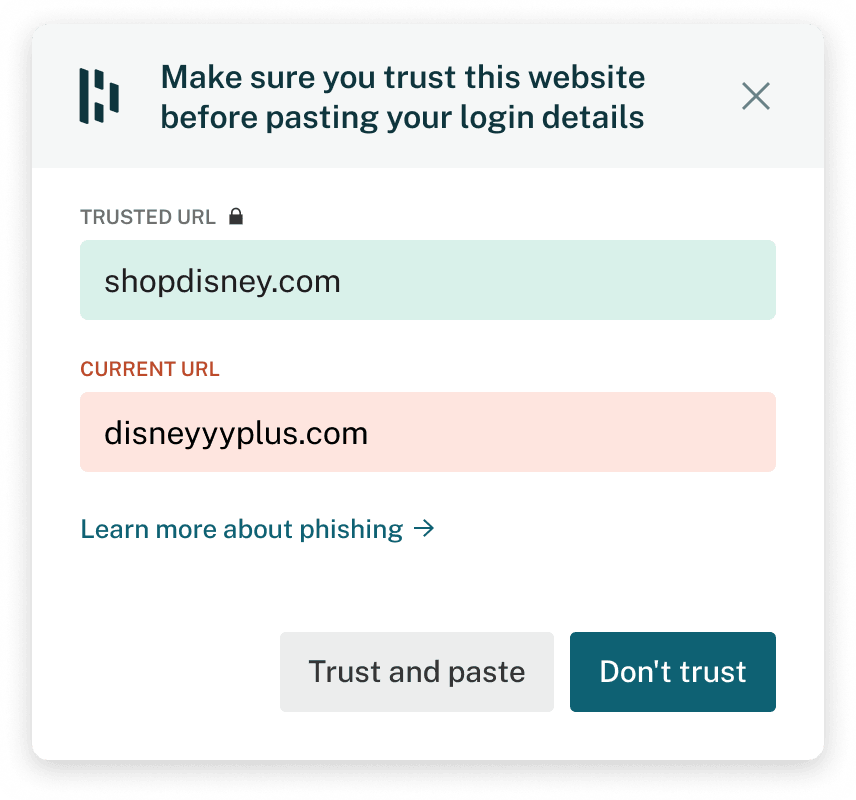
More than autofill: A journey to phishing resistance
For security to be effective, it has to be simple. Autofill makes secure logins effortless, steering people away from unsecure habits like reusing passwords.
But our vision doesn’t stop there. Autofill is part of a broader journey:
- Passwordless future: We’re advancing passkeys, security keys, and a Master Password-free experience—all designed to make phishing obsolete.
- Credential Risk Detection & Nudges: For businesses, we’re helping admins get insights on every at-risk employee credential and prompting employees through in-context alerts to fix these passwords.
- AI-powered phishing alerts: For businesses, we’re automatically notifying employees of potential phishing attempts in real time—before they enter any data.
Every step pushes toward a world where users don’t simply manage passwords more easily—they move beyond passwords altogether.
Practical takeaways for users
- Use autofill to log in effortlessly and anywhere with strong, unique passwords, rather than relying on the less safe option: Copy and paste.
- Enable 2FA on your most important accounts.
- Accept software updates to keep your apps, browsers, and devices protected.
- Adopt passkeys when offered because they’re phishing resistant by design.
The safer choice: Keep autofill enabled
Autofill is more than a convenience feature—it’s a defense against phishing and poor password habits. At Dashlane, we continually strengthen our autofill engine with anti-clickjacking measures, phishing alerts, and smarter protections, all while preparing for a passwordless future.
Keeping autofill enabled is an important step you can take to stay safe online. Turning it off may feel like a cautious move, but in practice it raises your risk.
Without autofill, people fall back on weaker habits—like reusing simple passwords or copy-pasting credentials into sites that could be malicious. Autofill not only eliminates those risky behaviors, it actively protects you from phishing by filling credentials only on the exact domains you’ve saved.
Autofill’s security benefits far outweigh the risk of clickjacking. By leaving autofill on, you’re choosing the path that is both easier and more secure.
We make credential security seamless to help you stay one step ahead of attackers—and one step closer to a safer digital life.
Sign up to receive news and updates about Dashlane