Security Terms 101: What Zero-Knowledge Architecture, Encryption, and More Really Mean

In the world of cybersecurity and digital identity, we use a lot of jargon, but hopefully this post can provide some clarity amidst the common confusion. Here, I break down what important industry terms mean, so you can more easily understand what they are and how they relate to the Dashlane experience.
Zero Knowledge
What zero knowledge means: Dashlane is built on the principle of zero knowledge to ensure only you have access to your Dashlane vault. Take the example of a bank heist in classic movies: The thieves want to access a vault. They first need to break into the bank and beat the bank security, such as the door that gives access to all the individual vaults. Then, say they need 2 keys: One key they must steal from the bank director, and one key they must steal from the owner of the vault.
Those 2 keys ensure that:
- The bank director alone cannot access the contents of the vault, even though they are storing precious content on your behalf.
- You, as the owner of the vault, control a critical piece of its protection—something that the vault can never be opened without.
How we use zero knowledge at Dashlane: Dashlane never wants access to the credentials and other sensitive data in your vault. Thus, we use zero-knowledge architecture to ensure only you own the key—which, in this case, is the Master Password.
Dashlane does not technically own another key, but we’ve built the encryption mechanism that ensures your vault is secured with your key and the vault data can only be accessed by you, the owner. That’s why all the sensitive processing for Dashlane happens locally on your device, such as the encryption and decryption of your vault. It ensures we don’t see it on our servers.
Encryption
What encryption means: So, let’s talk about encryption. Continuing with my movie references, encryption is like those secret codes used in adventure movies. It’s a way to scramble data so that it can only be decrypted and read if you know the code. Encryption relies on complex mathematical formulas and usually uses a key, called a cryptographic key, to make the encryption unique to a specific piece of data.
There are two main types of encryption.
Symmetric Encryption
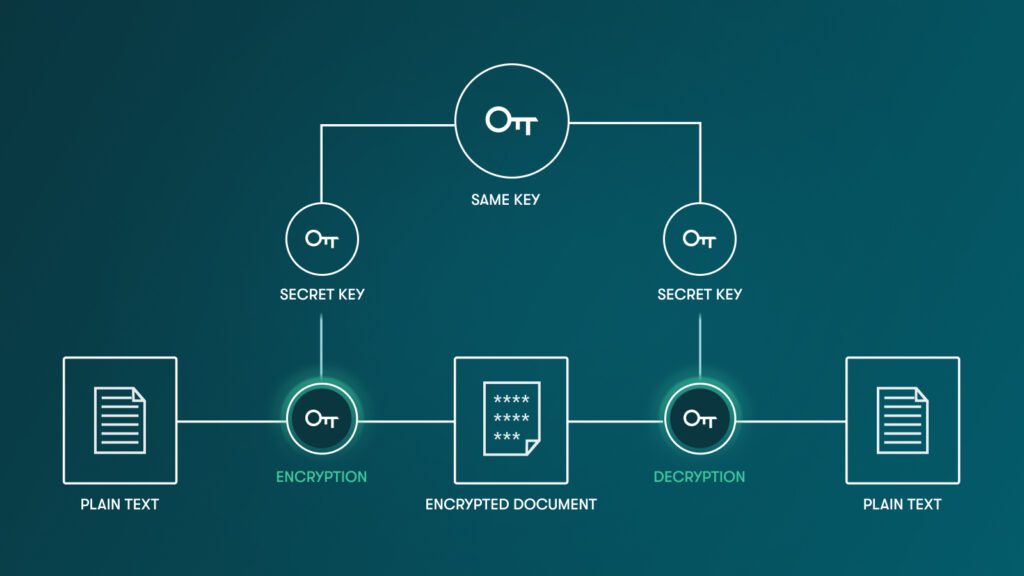
What symmetric encryption means: There is a single key that allows you to encrypt and decrypt data.
How we use symmetric encryption at Dashlane: Symmetric encryption is what Dashlane uses to encrypt your vault. A common symmetric encryption algorithm is AES.
Asymmetric encryption
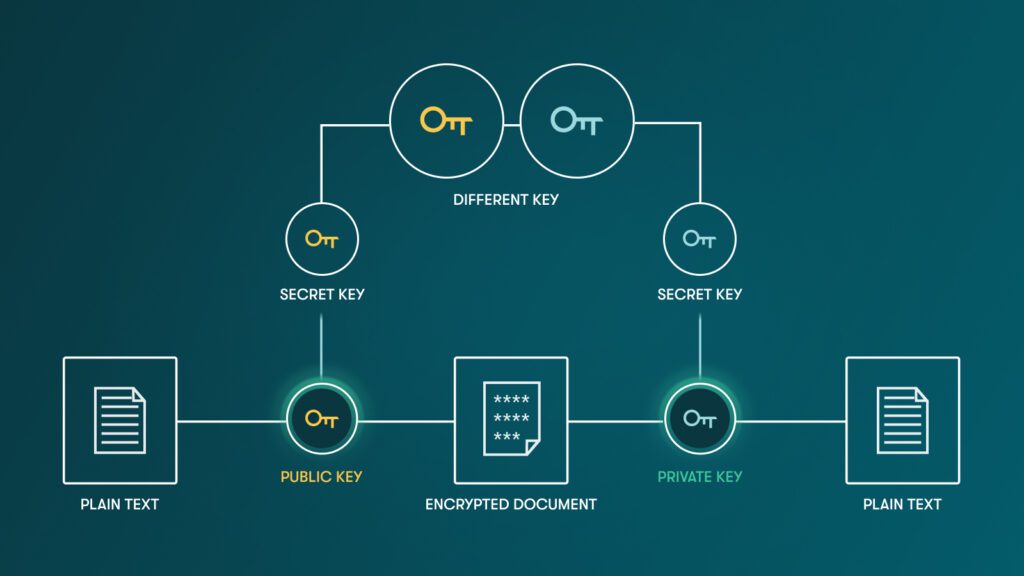
What asymmetric encryption means: Also called private-public key encryption, asymmetric encryption involves 2 different keys. One is used to encrypt, and the other one is used to decrypt. You have one public key used to encrypt, and it can be shared with anybody since it is only used to encrypt. On the flip side, the private key, which is then used to decrypt the data, should be kept secure.
How we use asymmetric encryption at Dashlane: Asymmetric encryption is used by Dashlane to share credentials between users, thanks to an algorithm called RSA.
Key Derivation Function
What key derivation function means: Secrets chosen by humans are usually not strong enough to be used as encryption keys. They are not long enough and random enough to ensure the right level of security. That’s why we need a key derivation function. This is an algorithm that will take your Master Password and add a bit of magic mathematics to generate a long, random cryptographic key.
Think about it like this: The cryptographic key is what allows you to open the door, while your Master Password is the secret word you tell the locksmith (the key derivation function) so that they can create the key for you. If you give the same input (the same password), you will always generate the same cryptographic key.
In addition, key derivation functions are purposefully slow to compute, which helps prevent brute-force attacks.
How we use key derivation functions at Dashlane: Dashlane uses Argon2 as a key derivation function to generate the encryption key for your vault from your Master Password.
Make sense of jargon related to IT, cybersecurity, cyber threats, Identity and Access Management, and password management in our popular e-book.
Post-Quantum Cryptography
What post-quantum cryptography means: The world of cryptography is facing an existential crisis with the birth of quantum computing. I won’t go into details about the physics and science behind quantum computing, but this is a revolution in how computers are designed and built. Once post-quantum cryptography matures, the new generation of computers will make current asymmetric cryptography obsolete and breakable.
How we use post-quantum cryptography at Dashlane: It’s time for software companies like Dashlane to prepare for an evolution of the cryptography ecosystem to ensure we keep your data secure in the future. If you’re curious about more details, check out our current work and how we’re getting ready.
Confidential Computing
What confidential computing means: This is another innovation in the world of computer sciences. Confidential computing processes data in a protected zone of a computer. Today, this usually happens in the hardware of the device in what is called a hardware secure enclave. You use it every day on your phone without knowing because Android and iOS manage sensitive data such as biometrics inside the secure enclave of the device.
The recent innovation is cloud-based secure enclaves: These offer a similar capability as hardware secure enclaves, but existing in the cloud and making it accessible to software products that can’t directly access hardware enclaves.
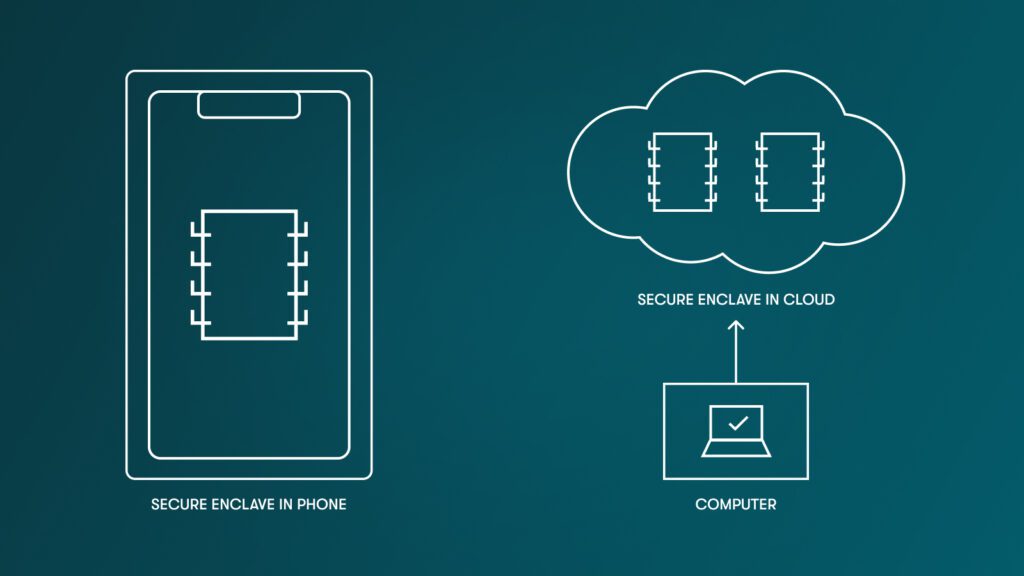
How we use confidential computing at Dashlane: Confidential computing unlocks very interesting opportunities for products like Dashlane. It allows us to think about zero knowledge in a different way. Instead of having all sensitive data managed on the device of the user, we can consider having some processing happen in a cloud-based secure enclave. This is the innovation on top of which Dashlane Confidential SSO is built: We are leveraging cloud-based secure enclaves offered by our cloud provider AWS (their feature is called Nitro) to process cryptographic keys required to connect a company SSO with Dashlane.
Zero Trust
What zero trust means: The security industry coined the marketing term “zero trust” to refer to a security model based on the philosophy that no one inside or outside an organization’s network should be trusted and granted access unless it’s explicitly approved. In short, it means zero implicit trust.
Instead of trusting the walls of the castle and the guards at the gate to ensure you’re safe, you assume you could already have spies inside the city, so you need to be paranoid and control every inhabitant without trusting them implicitly.
How we use zero trust at Dashlane: Zero trust doesn’t really apply to Dashlane. It’s really more of a network concept associated with the evolution of firewalls and VPN security. But since it’s often confused with zero knowledge, it felt important to define it here. The shared philosophy is that we trust no one, not even ourselves as Dashlane employees. Thus, we build Dashlane based on zero knowledge to ensure our customers are safe and our company is protected.
I hope the way I’ve explained these complex terms has helped you better understand their meaning. Dashlane aims to make security simple for everyone.
Learn more about Dashlane's technical security nuances in our Security Principles & Architecture white paper.
Sign up to receive news and updates about Dashlane