What Is a Good Password? 5 Tips for Increasing Password Strength
Ever wondered how to make a good password? A strong, secure password can outsmart even the most determined cybercriminal, but it’s important to follow these cybersecurity tips to ensure you know how to create a good password.
What is a good password?
A strong password has several characteristics that contribute to overall security:
- Unique
The more complex your password is, the harder it will be for cybercriminals to guess it. Good passwords include a variety of characters, numbers, symbols, and capitalization. Stay away from including identifying information or an easily guessable series of numbers or letters.
While you may be tempted to reuse a password across multiple accounts, this habit creates more opportunities for cybercriminals to access your data. Using one unique password per account ensures that any potential data breaches remain contained to one account.
- Not shared with anyone
Sharing account access with multiple users means that more devices are being used to access the account, which creates more entry points for cybercriminals.
Not only that, but sharing passwords often occurs across unsafe channels. This includes writing them down on a piece of paper or sending them across unencrypted channels like chat apps, email, or text. Sending password information this way gives an easy access point to cybercriminals, who don’t have to do any decrypting to steal this sensitive information.
- Stored securely
To be effective, passwords must be stored in a secure manner. Secure methods such as password managers, for example, can do double duty by remembering all of your passwords while storing those passwords as encrypted codes that are extremely difficult to decipher.
“We had untold numbers of people accessing passwords, pasting them into forms within a browser and, by default, having the browser indefinitely save our passwords alongside all of their personal ones."
Technical Manager, VillageReach
Want to make life harder for scammers?
Check out our free username generator and random password generator tools.
Think you have a strong password? Use our password strength tester tool to put it to the test!
How to create a strong password
If you’re worried about the strength of your password, here are some tips for how to make a secure one:
- Create something unique and memorable to you
If you don't use a password manager and instead have to memorize all your passwords yourself, creating a password that's memorable to you can help you keep track of your password without having to write it down or store it unsafely.
However, there are some caveats to this tip. You need to avoid identifying information such as your birthday, current or previous addresses, social security number or other personal identification numbers, and your name. While intentionally misspelling words can be a good start, cybercriminals are aware of this tip and often try misspellings of identifying information as potential passwords.
The best passwords are long, unique, and random, but those can be difficult to memorize. Fortunately, there are ways to remember your hard-to-remember passwords.
- Change passwords when necessary
If there’s no reason to suspect that you’ve been hacked, there’s no need to change your password. Frequent password changes often result in several variations of the same original password being used, such as Password123! And Password123*. Cybercriminals are aware of this behavior and exploit it.
However, if a company you have an account with gets hacked or you notice suspicious activity on one of your accounts, you should change your password right away and set up multifactor or 2-factor authentication if possible. Be sure to maintain your password’s strength every time you update it by keeping it long, unique, and random.
- Never store passwords in unsafe places
Writing passwords down on paper or storing them in an Excel sheet, Word document, or browser makes them easy to steal because they are unencrypted. If someone gains access to your device or even just looks over your shoulder, they can get all your passwords instantly.
- Use multifactor authentication
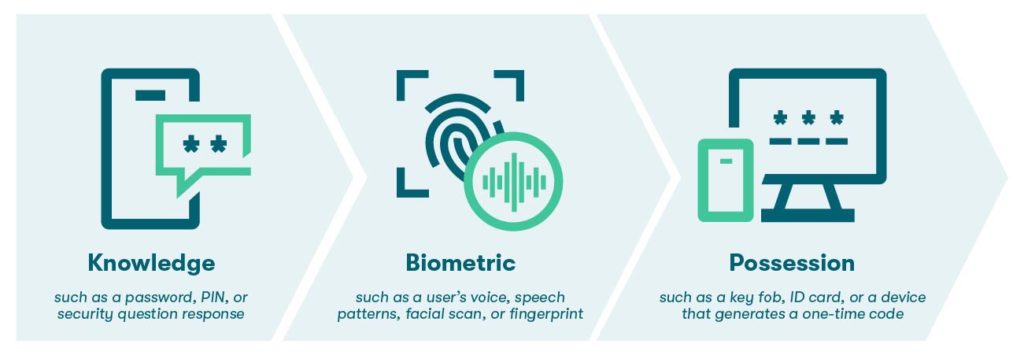
Multifactor authentication (MFA), or 2-factor authentication (2FA), is an effective safety net against cybercriminals and attempted account theft. By requiring you to confirm your identity through additional layers of authentication, such as a security question, fingerprint, or one-time code sent to your email, MFA prevents anyone who isn’t you from accessing your account. Even if a cybercriminal knows your password, they won’t be able to log in without access to those additional layers of authentication as well.
- Download a password manager
Password managers are an easy strategy to improve your password strength. Of all the password storage methods, a password manager is one of the few tools that encrypts a password before storing it. Encryption is the process of scrambling a password into different letters, numbers, and symbols, and it’s often used for sensitive data storage. This is what makes password managers so secure. Dashlane also integrates with 2-factor authentication and single sign-on technology for an extra layer of security.
How do passwords get hacked?
Cybercriminals attempt to steal passwords in a number of ways and are constantly updating their strategies to take advantage of weak spots in cybersecurity software. Here are some common strategies that cybercriminals use to gain access to login credentials:
- Malware
Malware is malicious software that can be downloaded onto a user’s computer when they click on a link, which can appear as an advertisement, a compromised website, or even a mobile app that looks legitimate. After a user clicks on the link and unknowingly downloads the malware, it can perform functions like logging a user’s keystrokes without them knowing or taking screenshots of a user’s desktop and sending them to attackers.
- Brute forcing
Brute forcing is when cybercriminals use the sheer volume of data they have to their advantage. Cybercriminals feed large volumes of previously stolen passwords—often bought on the dark web—into automated software. This is known as credential stuffing. Because of the sheer amount of passwords they try, they can often eventually find the one that works and gain access through brute force. In 2020, one study found that there were approximately 193 billion such attacks globally.
- Phishing and social engineering
Phishing and social engineering lead many internet users to accidentally download malware. This can occur in professional environments when a fake email from the company CEO asks the recipient to click on a link, which is known as “spear-phishing.” It can also occur when a cybercriminal targets the CEO themselves, which is known as “whale-phishing.” Cybercriminals try to convince a user that they’re actually someone else and need information from them, appealing to the user’s sense of empathy and social responsibility.
While we all want to be helpful, it’s important to be skeptical of any email, text, or phone communication that asks you to divulge personal or sensitive information. Learn more about how to avoid becoming the victim of a phishing attempt.
- Shoulder surfing
Shoulder surfing is when a cybercriminal gains access to a user’s login credentials or other sensitive information simply by peering over their shoulder or eavesdropping. While this usually happens in public places like libraries or cafes, it’s possible for shoulder surfing to occur in a professional environment as well. Public WiFi also makes you susceptible to this technique because cybercriminals can use it to access your information while you’re connected.
- Guessing
Unfortunately, many users have passwords that are very easy to guess. As a result, some cybercriminals can simply guess a password by trying a series of commonly used passwords. But remember, a cybercriminal’s ability to guess your password depends on how long, unique, and random you make it. Avoid common passwords having your logins guessed by always creating passwords that are long, unique, and random.
Wonder if you have a secure password? Use our password strength tester tool to make sure your password can't be easily guessed.
What to do if your password gets hacked
As soon as you suspect your account has been hacked or are notified of a data breach by your employer or an account you use, take these steps right away to ensure the damage remains contained to as few accounts as possible:
- Change your password immediately
Remember to maintain password strength by making your new password long, unique, and random. Additionally, any other account that uses that same password should be updated to something different, and you should also avoid reusing passwords in the future.
Adding one or more authentication options to your accounts beyond password authentication makes it much harder for cybercriminals to gain access. Authentication suggestions include knowledge factors such as a PIN or security question, biometric factors such as a facial scan or fingerprint, and possession factors such as a one-time code sent to a mobile device or a physical ID card.
- Notify the company if they aren’t aware
If you receive a phishing attempt on a professional account, notify the company you work for immediately by contacting IT and detailing the time, place, and nature of the phishing attempt. Even if IT is already aware of the problem, your report will help them understand the scope of the issue. You should also inform IT of any action you took related to the attempt. It is never a good idea to respond to a phishing attempt or click on any of the links, but if you did by accident, it will be important for IT to know that, too.
Additionally, if you notice suspicious activity on one of your personal accounts, such as an online shopping account or your banking platform, you should report it to the company as soon as possible.
- Watch your other accounts closely
Until the scope of the data breach is known, you need to make sure that your other accounts are safe. Monitor for evidence of cybercriminal activity on your email and banking platforms and freeze any accounts you feel might be at risk. Don’t forget to update those accounts’ passwords as well.
How Dashlane bolsters your password security
The Dashlane password manager securely remembers and autofills all of your passwords so you don’t have to remember each one yourself. Dashlane’s 256-bit encryption method—the same type used by some government agencies—employs zero-knowledge architecture, which means not even Dashlane employees can access or decrypt your password.
Even better, Dashlane works seamlessly with other security measures, such as 2-factor authentication and single sign-on (SSO) technology, which increases security while saving time. Not only do users have their passwords stored for them in the password manager, but SSO integration allows them to sign in once and access several applications through that single login attempt.
A strong and securely stored password can mitigate some of the effects of a password leak. Read more about some of the worst password leaks of 2021 for details and practical advice.
A strong and securely stored password can mitigate some of the effects of a password leak. Read more about some of the worst password leaks of 2021 for details and practical advice.
References
- HelpNet Security, “3.4 billion credential stuffing attacks hit financial services organizations,” 2021
- WeLiveSecurity, “5 ways hackers steal passwords (and how to stop them),” 2022
Sign up to receive news and updates about Dashlane
