Passwords are the keys that protect financial accounts, company secrets, and other valuable data. This has made passwords a prime target for hackers with bad intentions, but how do hackers get passwords?
How do hackers steal passwords?
If there was only one tactic being used, it might be easier to guard against password theft. Unfortunately, cybercriminals have developed a wide variety of methods that include:
- Phishing attacks: Social engineering tactics rely on human nature and psychological tendencies to gain unauthorized system access and steal information. Phishing attacks are a common social engineering approach that use bogus emails, texts, or phone calls—appearing to be from legitimate sources—to trick us into providing confidential information like passwords.

- Password reuse: Globally, it’s estimated over half of passwords are reused. Reusing passwords is a dangerous habit that puts multiple accounts at risk—if one is breached, they could all be breached.
- Malware: How do hackers steal data? Malicious software, or malware, includes variants like adware, worms, and viruses that interfere with the function of your computer. While some malware types are simply annoying, more dangerous varieties can be used to steal money, passwords, and other data:
—Ransomware: Cybercriminals use ransomware to render a computer or its contents inoperable until a ransom is paid using cryptocurrency or a credit card. Paying off ransomware perpetrators can encourage them to attempt more crimes in the future and improve their methods.
—Spyware: This form of malware installs itself on your device and collects information as you work, continually streaming data back to the cybercriminal. Any usernames or account passwords you enter can be stolen by the cybercriminal without your knowledge. - Brute-force attacks: Ever wonder how hackers get your information? Sometimes, the answer is as simple as trial and error. Brute-force attacks use software to guess at user passwords over and over until a match is found. Rather than stealing or purchasing the password, the hacker obtains it through computer-assisted guesswork made more effective by weak or reused passwords.
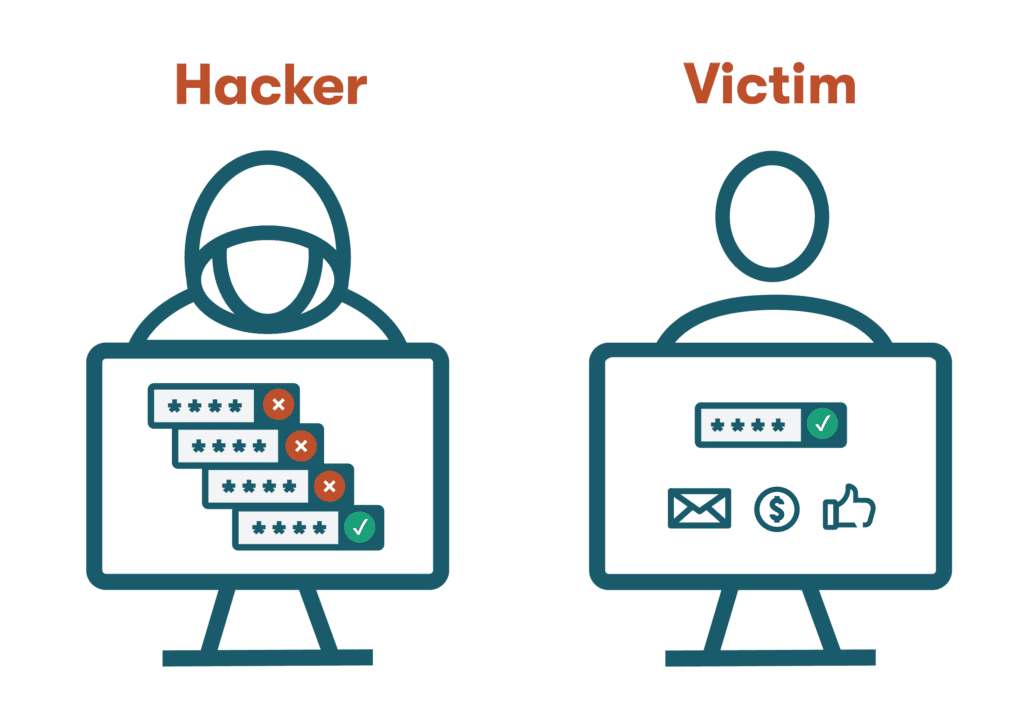
- Dictionary attacks: What do hackers use to hack passwords more efficiently? A subset of brute-force attacks, dictionary attacks cycle through lists of common password phrases and patterns to improve their odds of success. Rather than generating passwords randomly, a dictionary attack leverages available lists of the most commonly used passwords.
- Data intercepts (man-in-the-middle attacks): Using this tactic, a hacker virtually positions themselves between two parties to intercept data traveling between them. MITM attacks can be attempted in areas with unsecured WiFi connections, like airports, cafés, and hotels. Spoofed WiFi hotspots, named similarly to legit networks to deceive users, are another hacking tool used to intercept data in public settings.
- Unsafe password sharing: Sharing passwords with friends, family, and coworkers is almost unavoidable, especially for video streaming and online retail accounts. Password sharing increases vulnerability to password theft in two ways. First, the information can be intercepted while being shared if an unencrypted method like text messages or Slack is used for sharing. Second, sharing passwords exposes everyone in the group if any one of them is impacted by cybercrime.
- Shoulder surfing: How do you get hacked in open settings, even when you’re not connected to the internet? Despite all the high-tech tools developed to steal passwords from parts unknown, old-fashioned physical password theft is still a threat. As the name implies, shoulder surfing involves stealing confidential information by looking over the target’s shoulder. Passwords written on sticky notes or slips of paper are highly vulnerable to this method. Shoulder surfing is also used to steal PINs in places like gas stations, ATMs, and supermarkets.
What do cybercriminals do with stolen passwords?
You might assume cybercriminals steal passwords for their personal use, collecting accounts to invade and plunder at their leisure. While this may be true in some cases, an entire industry has evolved for cybercriminals exchanging stolen passwords for money on the dark web.
This segment of the deep web is where cybercriminals can complete illegal transactions while keeping their identities hidden.
How to know if you’ve been hacked
Some dangerous hacking tactics, including spyware, are designed to go unnoticed, allowing the cybercriminals to steal more passwords and other valuable information for a longer period. Other methods have more visible signs you can look for. These signs include:
- Random pop-ups: Pop-ups from sites that don’t typically generate them are a definite warning sign, especially if they include messages from fake antivirus software companies. When you experience excessive or unusual pop-ups, install an antivirus or anti-malware software package if you don’t already have one, and scan your system right away to detect and quarantine any malicious files.
- Emails or direct messages sent from your account (that you didn’t write): Have friends or family members ever asked you about mysterious links or messages from your email or social media account that you never sent? A cybercriminal may have cracked your account password, then stolen personal and financial information from your archives or sent phishing messages to your contacts.
- Your passwords stop working: A cybercriminal who has stolen your password might change the password to lock you out and grant themselves private access. A mistyped password may get you locked out temporarily after several attempts, but if your password and recovery methods continue to fail, someone else may have seized control.
- Fraudulent transactions: You should always pay close attention to bank statements and other financial records to ensure there have been no unusual or unexplained transactions. Cybercriminals might make small purchases initially to test the waters, so don’t overlook low-dollar transactions if you don’t recall making them. Notify your bank or credit card company and change your password immediately if you notice any suspicious transactions.
- You receive a notification: Financial organizations, employers, and cybersecurity apps will often provide security alerts if your account password has been compromised in a data breach. Even if you experienced no visible signs of hacking, you should always take these alerts seriously by changing impacted passwords and following any other recommendations included with the alert.
- Your information is detected on the dark web: Stolen passwords are often traded for financial gain, so scanning the dark web provides an added layer of protection in cases where the cybercrime went undetected. Dashlane’s Dark Web Monitoring continually scans the dark web for your passwords and personal information and notifies you if they’re detected.
How to prevent bad actors from getting your passwords
Cybercriminals have expanded and improved their password theft techniques, but that doesn’t mean you can’t protect yourself. Apply these basic tools and best practices to minimize the risk of stolen passwords:
- Create strong passwords
A strong password is one that is at least 12 characters long and includes a random mix of uppercase letters, lowercase letters, numbers, and special characters. You should avoid using personal information (like your name) in your passwords since this makes them more vulnerable to brute-force or dictionary attacks. You should also avoid reusing passwords since multiple accounts can be compromised if a reused password is stolen.
- Use encryption
Encryption, or hiding information in an unrecognizable format, originated in ancient times and is now an invaluable tool for website and password security. Encryption provides strong protection from password theft since hackers are unable to see the unencrypted version of the password without the encryption key. Dashlane password manager utilizes AES-256 encryption, widely accepted as the strongest encryption type available, to protect passwords.
- Don’t share passwords insecurely
When you use unencrypted password-sharing methods like email, text messages, or Slack to share passwords, you increase your vulnerability to hacking and password theft. Luckily, there are safer sharing methods available. Dashlane’s encrypted sharing portal can be used to send passwords, files, or Secure Notes to other Dashlane users easily and securely.
- Learn how to spot social engineering tactics and unsafe websites
Social engineering tactics can extend well beyond phishing emails to include phone calls, in-person scams, and even deepfake impersonations. Imposing a zero-trust policy helps to compensate for the dangerous combination of technology and our tendency to trust others by ensuring everyone is authenticated, no matter who they are (or claim to be). Security training and a discerning eye are also essential for identifying unsafe websites that increase vulnerability to malware and data intercepts.
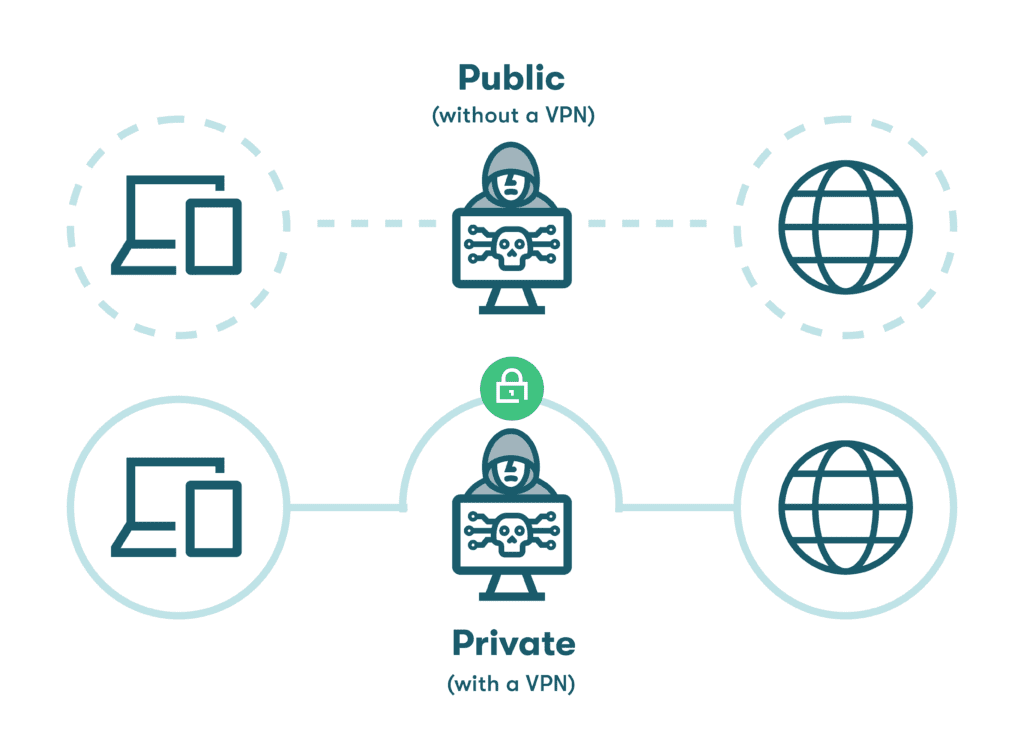
- Use a VPN on public Wi-Fi networks
Public WiFi networks can be susceptible to data intercepts and spoofing, but there is a reliable way to ensure your safety. Using a virtual private network (VPN) protects your privacy, passwords, and account information by encrypting the data going into or out of your device and routing it through a secure portal. A VPN also masks your IP address so you can browse the internet privately.
- Turn on 2FA
2-factor authentication (2FA) uses a second login credential in addition to a password. This is typically a code sent through an app or text message. Enabling 2FA when it’s available negates the impact of many common hacking tactics, since the hacker is unlikely to have both stolen credentials and the user’s device to gain unauthorized access.
- Use a password manager
A password manager improves your security posture by encrypting passwords and account details, storing your information in a secure vault, and enabling 2FA for an additional layer of security. Dashlane includes automatic password generation and customizable autofill to improve both security and convenience, eliminating the need to create and remember strong passwords for each account.
How Dashlane protects you from data theft
Standard Dashlane features, including a secure password-sharing portal, a Password Health score, and Dark Web Monitoring, help protect you from cybercriminals and password theft. Dashlane keeps your information private while making you aware of any data breaches or compromised passwords in real time. And Dashlane’s zero-knowledge architecture ensures that no one, including Dashlane, can ever access your unencrypted passwords and personal information.
References
- Dashlane, “Why Dashlane Will Never Ask You for Credentials in an Email (Because That’s How Phishing Works),” November 2021.
- Dashlane, “What the Hack Is Malware?” February 2020.
- Dashlane, “How to Prevent Ransomware Attacks on Your Devices,” March 2023.
- Dashlane, “What the Hack is a Brute Force Attack?” February, 2020.
- Dashlane, “10 Bad Password Examples: Avoid These Common Mistakes,” March 2023.
- NIST, “Man-in-the middle attack (MITM),” 2023.
- Dashlane, “What Is Password Sharing & When Should I Use It,” February 2023.
- Dashlane, “Sharing Passwords Through Slack Is Risky,” November 2019.
- Experian, “What is Shoulder Surfing?” October 2020.
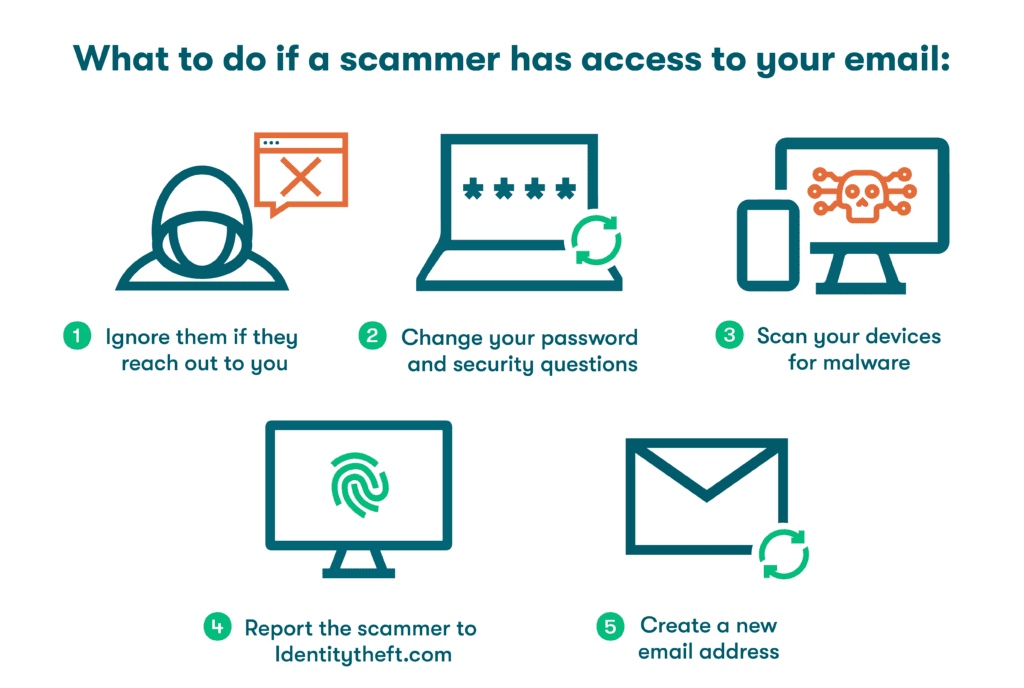
- Dashlane, “What To Do If a Scammer Has Access To Your Email Address,” April 2023.
- Dashlane, “Always Change Your Passwords After a Breach,” March 2020.
- Naked Security, “Why people ignore security alerts up to 87% of the time,” August 2016.
- Dashlane, “Do You Have These 6 Cybersecurity Basics Down?” June 2022.
- Dashlane, “How Strong Is Your Password & Should You Change It?” August 2022.
- Dashlane, “How Password Reuse Leads to Cybersecurity Vulnerabilities,” May 2023.
- Thales, “A Brief History of Encryption and Cryptography,” May 2023.
- Dashlane, “Best Way to Store Passwords at Home or Work,” September 2022.
- Forbes, “A Voice Deepfake Was Used To Scam A CEO Out Of $243,000,” September 2019.
- Dashlane, “Why Do You Need a VPN? Don’t Miss These 3 Key Benefits,” August 2020.
- Dashlane, “2-factor authentication (2FA) in Dashlane,” 2023.
- Dashlane, “Build the Case for a Password Manager in 8 Steps,” 2023.
- Dashlane, “11 Cyber Threats To Be Aware of & Defend Against,” April 2023.
Sign up to receive news and updates about Dashlane
Related articles