Businesses today don’t have a lot of control over their employees' passkey usage. There are many solutions their employees could use, depending on the operating system and browser, but they’re geared toward consumers rather than businesses.
For example, consider a business that wants to manage its social media credentials. Where should these credentials be stored? How can they be safely shared with other employees? How can access be rescinded when an employee leaves the company? These questions got us thinking about creating a passkey solution suited to business needs.
Improving passkey security with confidential computing
Dashlane is addressing these challenges by adding an extra layer of security to passkeys with confidential computing. With this update, instead of storing a passkey’s private key in the client software memory, Dashlane now stores it in a secure cloud environment, powered by AWS Nitro Enclaves—offering businesses greater control and peace of mind.

Passkeys now join SSO and SIEM on our growing list of capabilities that employ confidential computing.
This passkey implementation enables us to create better sharing features for passkeys in the future by leveraging more robust access control measures. We can also build confidential audit logs by capturing the information at the server rather than at the client, all the while maintaining zero knowledge by encrypting the logs with the necessary keys of the organization.
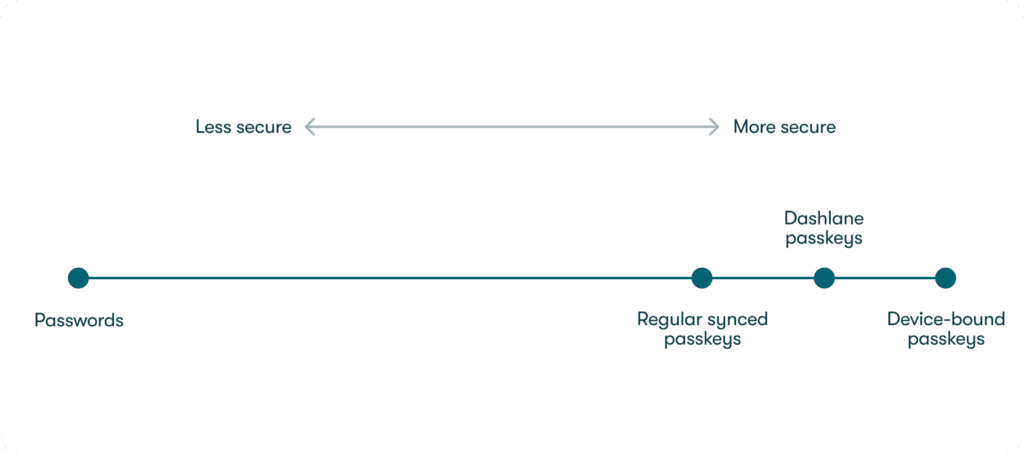
Businesses have two options regarding how their employees should manage passkeys. One option is to use FIDO2 security keys, which offer a high level of security but come with usability problems. Namely, security keys can only store a limited number of passkeys, and managing them is cumbersome.
Another option is to opt for a credential manager that manages passkeys, which tends to favor user adoption at the expense of some security properties provided by security keys. Dashlane, like many other credential managers, manages synced passkeys. They’re more convenient because they’re available across a user’s devices.
"There's a lot I could say about passkeys as a technology, but I fundamentally believe that they will create a world where account takeovers are almost eliminated."
—John Bennett, Chief Executive Officer, Dashlane
Combining security and usability
So, what sets Dashlane apart? By integrating AWS Nitro Enclaves, we’re increasing the security of synced passkeys, closing the gap to security keys without introducing the associated usability problems.
Businesses will gain more control over how employees use their passkeys and can enforce stricter policies about actions like credential sharing and credential export. If a business decides that passkey sharing should be confined within their organization, or a specific group of people, our confidential computing-based solution makes that possible.
And rest assured that this update doesn’t give Dashlane access to passkeys. As with all Dashlane vault data, we operate under a principle of zero knowledge, meaning only the end user has the ability to decrypt and use their vault items, including passkeys.
An encryption key is required to decrypt the passkey’s private key, and it remains solely in the hands of the end user. Each time a passkey is used, the user’s device authenticates with the cloud-based secure enclave. The associated encryption key is delivered using a secure tunnel, ensuring the private key never leaves its protected environment. The safeguard is based on two factors: a trusted device and the encryption key associated with the passkey.
This is just the beginning of a more secure passkey experience with Dashlane. We’re committed to evolving our solution to meet the ever-growing security demands of the businesses we serve.
Sign up to receive news and updates about Dashlane