How to Mitigate BYOD Risks with a Password Manager
Bringing your own device (BYOD) has taken the workplace by storm, with over 80% of organizations enabling it. BYOD programs have boosted productivity and convenience, but they have also increased security risks. With threats ranging from data leakage to privacy concerns, it’s crucial to mitigate BYOD risks and secure employee devices.
Want to learn more about using a password manager for your business?
Check out Dashlane's business plans or get started with a free business trial.
The risks of BYOD
What is BYOD security? BYOD security refers to the tools and practices used to prevent data breaches caused by employees using personal devices and working remotely. Here are the main risks BYOD security is intended to mitigate:
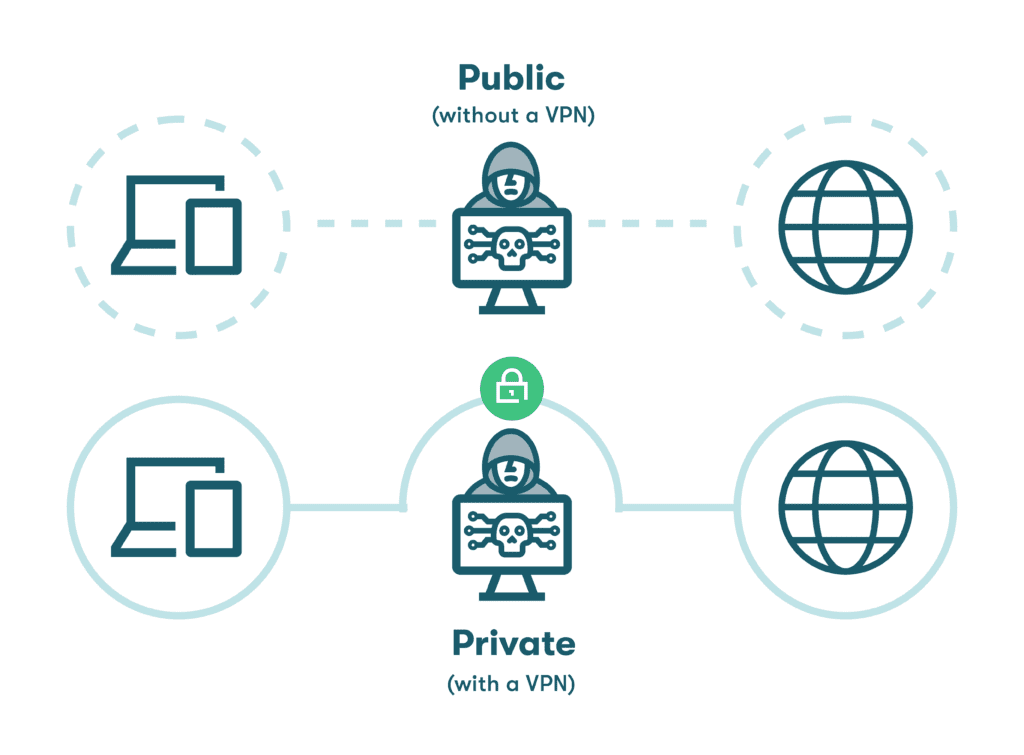
- Unsecured WiFi: Connecting personal devices to unsecured WiFi networks, especially in public places like coffee shops, airports, and hotels, can leave company data vulnerable to cyberattacks and data breaches. Employees should use a virtual private network (VPN) to secure their connection and protect company data when accessing the internet via public WiFi.
- Fake, malicious, or outdated apps: Fake and malicious apps can take control of users' mobile devices, leading to unexpected charges, loss of personal or work information, or even surveillance. Employees may unknowingly visit compromised websites and download malware such as computer viruses and spyware. With malware attacks, particularly ransomware attacks, increasing, such threats can easily infiltrate employee devices and remain undetected, ultimately infecting company files or accessing client data.
- Lost or stolen devices: When personal devices are lost or stolen, there is a risk that sensitive corporate information could be compromised, especially if the devices lack basic security measures. This kind of information in the wrong hands could be devastating.
- Unprotected credential sharing with colleagues: Sharing credentials with your coworkers using unencrypted tools such as Slack or email may unknowingly lead to password interception or data leakage.
- Cross-usage: Many employees use their personal devices for both business and personal activities. Despite providing security training, it can be challenging to ensure employees follow best practices and avoid behaviors such as shopping on compromised websites or lending their devices to others.
- Password syncing: Practices like syncing passwords across multiple devices without a password manager and storing passwords on internet browsers are not secure. If the passwords are weak and outdated, an attacker can easily crack them and gain access to sensitive data or confidential company information.
- Shared devices with friends/family: Sharing passwords and devices with unauthorized users, such as friends or family members, can compromise the company's network, confidential data, and regulatory compliance.
- Lack of training and enforcement: It can be challenging for IT administrators to maintain security when employees work remotely as these employees interact less with IT and can be more lax about reporting suspected security breaches or issues.
To understand how employee internet behavior can impact your company’s security, read Dashlane's Future of Secure Work for People + Organizations Report.
How to mitigate BYOD risks using a password manager
Password managers securely generate strong and unique passwords for each user account and store them in an encrypted database. They can autofill these passwords across various devices, eliminating the need to remember multiple complex passwords.
Some password managers also provide features like secure credential sharing, isolated business accounts, and dark web monitoring to help mitigate BYOD security issues.
Here are some of the best ways to use a password manager to combat BYOD security risks:
Develop a BYOD security policy
A BYOD security policy outlines the security requirements and expectations for employees who use their personal devices to access company data, networks, and systems. It generally includes:
- Defining permitted devices, apps, tools, and security requirements: For example, the BYOD policy may only allow employees to use devices that meet specific security standards, use a reliable password manager to manage login credentials, and access the company network only via a VPN.
- Training and enforcement for all employees: All employees must be educated about the security risks associated with BYOD and instructed on best practices for using their devices safely. This includes guidance on avoiding risky websites and public WiFi, regularly backing up data, and immediately reporting any lost or stolen devices. Enforcement measures such as regular security audits and disciplinary action for policy violations should also be implemented to ensure compliance. A comprehensive password manager can help enforce these policies by making it easier for employees and IT to follow best practices.
Use a reliable password manager

A reliable password manager single-handedly improves password hygiene and minimizes the risk of password-related security breaches. It stores all the user's passwords in a secure, encrypted database that can only be accessed with a master password.
Password managers like Dashlane can generate strong and unique passwords for every account, enforce password policies, comfortably run across various devices and platforms, and provide an extra layer of security through features like data backup and secure sharing. In addition, Dashlane is easy to use and affordable.
Provide user-friendly tools for employees
Some standalone password managers are equipped with user-friendly tools that can add an extra layer of security against possible threats associated with BYOD.
- Password generator: All password managers come with a password generator. It creates strong, unique passwords, reducing the risk of password reuse and making it harder for hackers to crack passwords using brute force.
- Autofill: Most password managers can automatically fill in login credentials and other personal information for websites and apps, saving time and reducing the risk of phishing and errors.
- Single sign-on: Single sign-on (SSO) allows users to access multiple apps and services with just one set of login credentials, simplifying the login process and reducing the need for users to recall multiple passwords.
- Separate personal and business spaces: This feature compartmentalizes a user’s personal and business data within the password manager, which comes in handy when employees leave the company or share their devices with family members.
- Credential sharing portal: A secure sharing portal allows users to safely share passwords and other login information with team members, reducing the need to send passwords through an unencrypted email or text, which hackers could intercept.
- Virtual private network (VPN): A VPN encrypts internet traffic and routes it through a secure server, protecting user data and masking online activity from hackers.
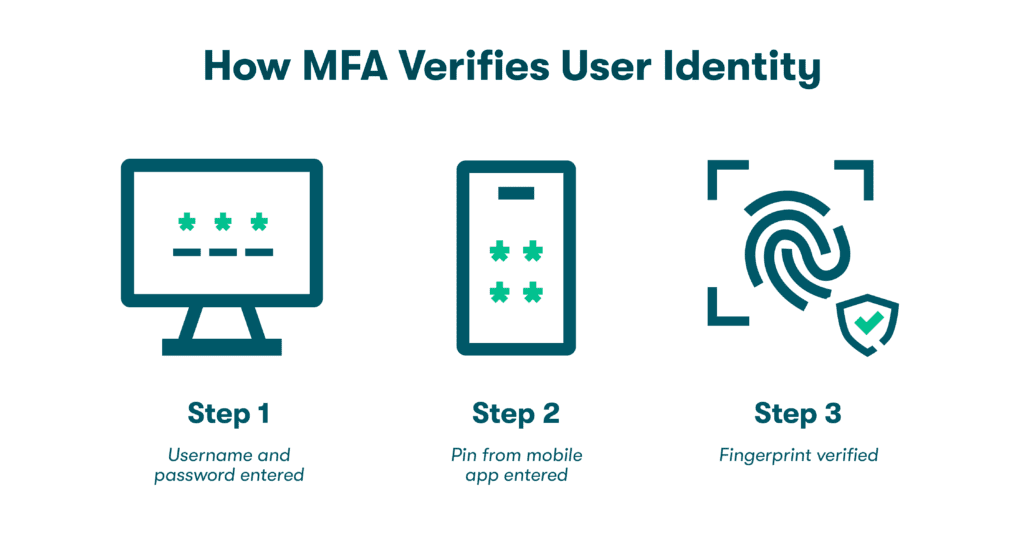
- Two-factor authentication (2FA): 2FA adds an extra layer of security to logins by requiring users to enter a code or use a biometric authentication method in addition to a password.
- Dark web monitoring: Password managers with this feature scan the dark web for stolen or leaked personal information, such as login credentials, and alert users if their data is found, allowing them to take immediate action to protect their accounts.
"Dashlane’s Dark Web Monitoring has been invaluable in helping us uncover security risks. We’re more aware with Dashlane and thus more proactive.”
Technical Manager, VillageReach
Provide functional tools for IT
Some business password managers also come with functional tools that the IT department can use to protect company data and enforce BYOD policies.
- Track group activity and manage users: Some password managers allow administrators to track group activity and manage users, giving them insight into how employees use, share, and store passwords. This helps organizations identify potential security risks and take action to prevent them.
- Password health score: Password health scores are determined by the strength and uniqueness of passwords used by employees. This can help businesses identify weak or reused passwords and prompt employees to update them to stronger and more secure ones.
- Dark web insights: Beyond Dark Web Monitoring, Dashlane provides Dark Web Insights. This feature alerts administrators if any passwords associated with their organization have been compromised and are being sold on the dark web. Based on this, proactive measures can be taken to protect company systems and data before more damage is done.
With Dark Web Monitoring, a separate Business space, secure credential sharing, and more, Dashlane is equipped with all the security tools you need to safeguard your business. Get started with Dashlane and secure your remote workplace today.
How a password manager helps secure networks
Password managers are among the best ways to secure a network. They help enforce password policies, improve password hygiene, manage authorized access, secure company data and credentials, and provide security alerts.
Here's how a password manager can cyber-fortify your business network:
Visibility and enforcement of password policies
Password managers help companies monitor employee password practices through a centralized console, allowing for standardized and enforced BYOD security policies. This ensures that all employees adhere to organizational password policies, such as required password length and mandatory multifactor authentication (MFA) on all sites that support it, whether they are working remotely or onsite.
Easy to implement role-based access
It’s best practice to limit employee access to just the systems necessary for their job responsibilities. Doing so helps prevent insider attacks and minimizes potential risks if an employee's account is breached. Role-based access also helps with:
- Simplified employee onboarding/off-boarding: A password manager can support the seamless onboarding of new hires, even in remote work scenarios, and allow IT administrators to provision new users quickly. During off-boarding, it can immediately terminate access for former employees and provide a secure transfer of accounts to other team members.
- Separate business and personal credentials: Business and personal accounts can be kept separate in most password managers. This prevents the mixing of credentials and secures the business accounts from being compromised when employees leave the company or share their devices with friends or family.
Improved password hygiene
Password managers specialize in improving password hygiene using features like:
- Password generator
- Secure password storage
- Safe credential sharing
- Autofill and SSO
- 2FA
Protects WiFi access with a built-in VPN
Password managers with built-in VPNs help protect WiFi access by encrypting internet traffic between the device and the internet, preventing hackers from intercepting and accessing sensitive data. This additional layer of security also helps users browse the internet anonymously.
Delivers security alerts
Robust and reliable password managers deliver security alerts, like password health scores and dark web insights, to keep users updated. Password health scores represent the strength of passwords, while dark web monitoring constantly scans the dark web for stolen or lost credentials. If anything seems out of the ordinary, alerts are sent immediately so that proactive action can be taken.
Fosters a culture of security
With multiple security measures and user-friendly tools, password managers foster a robust security culture, reducing the learning curve and anxiety associated with organizational security risks.
Secures credentials via encryption and zero-knowledge technology
Quality password managers follow a zero-knowledge architecture, which prevents them from accessing a user's account and maintains privacy. Additionally, these password managers use data encryption to protect all your data at all times. For example, Dashlane uses AES-256 encryption, one of the strongest forms of encryption available.
How Dashlane mitigates BYOD security risks
There’s more to Dashlane than powerful encryption. Dashlane also helps protect employee devices with 2-factor authentication, a VPN, Dark Web Insights, and more.
Dashlane’s user-friendly features, such as autofill, single sign-on, and secure password sharing encourage employee adoption without compromising productivity. Plus, an intuitive dashboard, separate Personal and Business spaces, and a Password Health score provide the tools IT needs to enforce BYOD policies and foster a culture of security.
With the widespread adoption of hybrid and remote workplaces, securing employee devices is more crucial than ever. Check out our latest blog post on why securing remote devices is absolutely critical for your business.
References
- Cybersecurity Insiders, “BYOD Security Report 2021,” 2021.
- CIMCOR, “The 8 Top BYOD Security Risks (and How to Mitigate Them),” January 2023.
- CEI - The Digital Office, “BYOD Security Risks And How To Protect Your Business.”
- Eclipse Consulting, “BYOD Risks: How To Overcome The Risks Of Employee-Owned Devices.”
- Quest, “Mitigating BYOD security risks, challenges and implementing best practices,” December 2022.
- Dashlane, “How Businesses with a BYOD Policy Can Secure Employee Devices,” January 2023.
- TechTarget, “Ransomware trends, statistics and facts in 2023,” January 2023.
- Dashlane, “Why Employees Shouldn’t Let Browsers Save Their Passwords,” March 2021.
- Dashlane, “How To Maintain Security When Employees Work Remotely,” October 2022.
- Dashlane, “2022 The Future of Secure Work for People + Organizations,” 2022.
- Dashlane, “Why Every Employee Device Should Be Secured,” May 2021.
- Dashlane, “Create a Culture of Cybersecurity: Teach Employees to Catch a Phish,” August 2021.
- Dashlane, “How to Stop Reusing Passwords for Good,” January 2020.
- Dashlane, “A Beginner’s Guide to Two-Factor Authentication,” August 2022.
- Dashlane, “Best Way to Store Passwords at Home or Work,” September 2022.
- Dashlane, “Understanding Your Dashlane Password Health Score,” October 2020.
- Dashlane, “How to Shine a Light on the Dark Web,” June 2022.
- Dashlane, “Why Do You Need a VPN? Don’t Miss These 3 Key Benefits,” December 2022.
- Dashlane, “How to Create a Culture of Security,” March 2022.
- Dashlane, “5 Flawless Ways to Launch a Password Manager at Your Company,” February 2023.
- Dashlane, “How Often Should You Change Your Password for Online Accounts?” January 2023.
- Dashlane, “Sharing Passwords Through Slack Is Risky,” November 2019.
- Dashlane, “7 Dangers of Sharing Passwords Without a Password Manager,” March 2023.
- Dashlane, “Top 10 Password Tips & Tricks to Protect Yourself,” February 2023.
- Dashlane, “7 Password Hygiene Best Practices to Follow,” February 2023.
- Dashlane, “5 Ways Dashlane Just Improved Its Autofill,” February 2023.
- Dashlane, “What Is SSO? Work Simpler With This One Tool,” September 2021.
- Dashlane, “A Complete Guide to Multifactor Authentication,” November 2022.
- Dashlane, “A Deep Dive into Dashlane's Zero-Knowledge Security.”
- Dashlane, “Putting Security First: How Dashlane Protects Your Data,” January 2023.
- Dashlane, “How to Conduct a Security Audit in Five Steps.”
- Dashlane, “How Businesses with a BYOD Policy Can Secure Employee Devices,” January 2023.
- Dashlane, “Creating a Password Policy Your Employees Will Actually Follow,” July 2022.
- Dashlane, “What Is Encryption?” March 2019.
Sign up to receive news and updates about Dashlane
