How Businesses with a BYOD Policy Can Secure Employee Devices
More people than ever are using multiple devices, including laptops, tablets, and smartphones, for both work and personal reasons. Bring your own device (BYOD) expands on this trend by allowing remote workers to use their personal devices to connect to company networks. This versatility improves workplace mobility, but it also introduces new security and device policy considerations. How can organizations and remote employees make sure that their devices are secured?
What is a BYOD policy?
A BYOD policy is a “bring your own device” policy, which means allowing workers to use their own personal devices for work. BYOD policies can boost productivity and satisfaction by allowing employees to work on devices they’re already familiar with. To take advantage of this opportunity while managing the potential risks and drawbacks, it’s important to have a written BYOD security policy in place. This policy answers many important BYOD questions for employees and management, including:
- What devices are permitted? Each new device and operating system brings unique interoperability and security challenges. Because IT departments need to provide support for any device used for company business, it’s vital to state in your BYOD policy what devices can (and can’t) be used.
- What apps are allowed? Allowing employees to work from home and use their own devices reduces the direct control employers once had over forbidden apps. This goes beyond banning time-wasting apps like video games, social media, and streaming services. Apps that can potentially expose company data to security risks by accessing address books and cameras without permission should be reviewed frequently and included in the BYOD employee device policy.
- What are the device security requirements? Device security requirements in the BYOD policy should include guidelines for where and when company data can be accessed, which virtual private network (VPN) or mobile device security apps should be used, and if 2-factor authentication (2FA) is applied. There should also be a documented offboarding employee process to define how company data is removed from employees’ devices once they leave the company. Many organizations have implemented Identity and Access Management (IAM) solutions to ensure BYOD users have system access when they need it.
- Who owns the device, data, and phone number? This line can become blurred in BYOD scenarios, especially when company stipends are provided for the device and its ongoing usage. The policy should define who is responsible for the cost of replacing hardware and personal data if a device is lost or stolen and needs to be wiped by the company and who retains ownership of the phone number if an employee separates.
- How can a password manager be used? A business password manager encrypts and stores employees’ passwords for every device and app they use. Employees only need to remember one master password to access the password manager and autofill logins for any account they want to access. The password management software used and guidelines for password storage and sharing should be included in the BYOD policy.

Want to learn more about using a password manager for your business?
Check out Dashlane's password manager for small businesses or get started with a free business trial.
Special security considerations for employee-owned devices
The increased use of employee-owned devices raises additional security concerns that must be addressed:
- Business and personal use: Employees using devices for both work and personal tasks are the crux of most BYOD security issues. Without an employee tracking device, it’s impossible for employers to control all websites visited, applications used, or public WiFi networks joined, even with a detailed employee device policy in place.
- Unsecured networks: The increase in remote and mobile working enabled by employee-owned devices makes it easier for employees to log in to unsecured public WiFi networks in coffee shops, airports, or hotels. A VPN mitigates this risk by encrypting all data going in or out of the device and routing it through a secure portal.
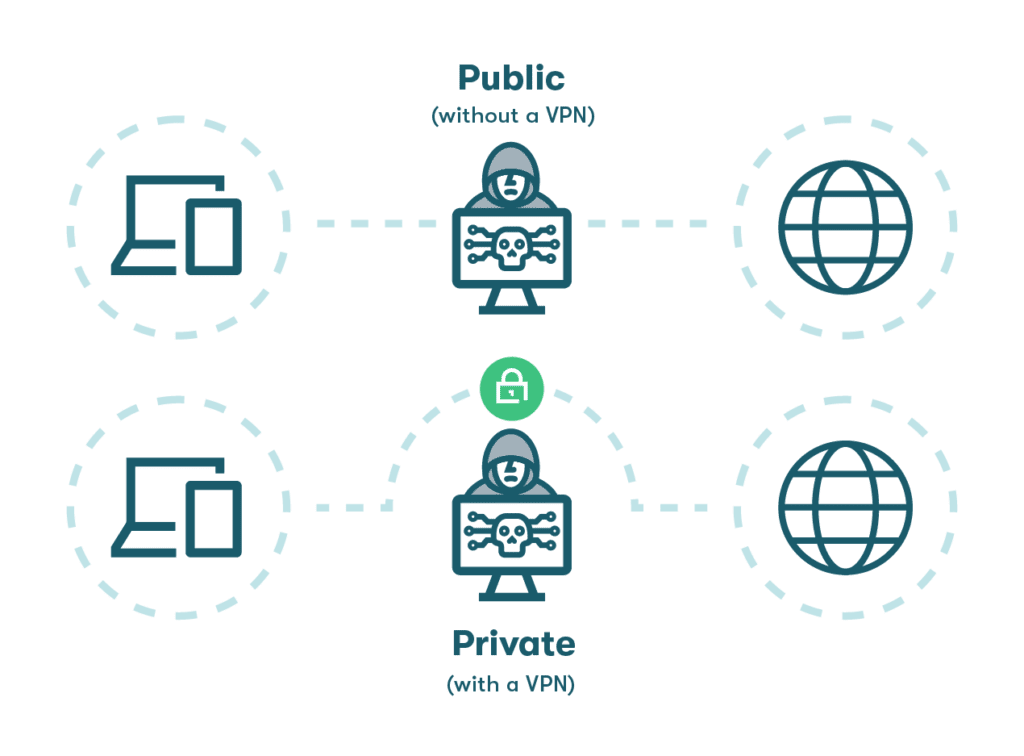
- Lost or stolen devices: A mobile device is also more likely to be lost or stolen. When this happens, personal email addresses and bank accounts can be compromised, along with company systems and data. Although screen locks and authenticator apps can minimize the impact, using a password manager adds an extra layer of security by storing encrypted password data where it can’t be accessed.
- Malicious, outdated, or unsafe apps: BYOD policies must consider the wide variety of apps users are likely to install. A malicious app disguised as a camera or chat app could actually be intercepting messages or installing malware. An unsafe app might not have malicious intent but could still compromise privacy or security. Antivirus software and strict adherence to the mobile employee device responsibility policy help to combat these risks.
- Phishing attacks: Social engineering tactics prey on human nature, using misleading phone calls, text messages, websites, or emails (phishing) to compromise privacy and security. If an employee’s personal device becomes the target of a social engineering attack, company accounts are also put at risk.
- Syncing of passwords: Employees need to make sure their access levels and logins remain consistent as they transition from one device to another. Dashlane’s cloud-based password manager easily syncs across all devices and operating systems so that updates can be made from any computer, smartphone, or tablet.

- Lack of training and enforcement: Remote employees who don’t regularly interface with IT teams are more likely to become complacent about reporting suspected breaches and other security issues quickly. Security tools, policies, and training should be developed with remote workers and BYOD in mind to address these unique risks and challenges.
The rise in remote working and BYOD policies make password protection more important than ever. Learn the essentials in Password Management 101.
8 ways to make sure your employees’ devices are secured with a BYOD policy
While there’s no bullet-proof method to ensure both business and personal information remains secure on employee-owned devices, these common-sense practices establish a foundation for safe BYOD use.
- Define safe app and device usage
BYOD policies that define how, when, and where personal devices can be used for work applications are an important first step. Technology-based solutions like containerization, where personal and company applications are physically isolated from one another using a common operating system (OS), are also available to partition work and personal data and reduce the need to monitor or control the personal applications employees install.
- Keep track of network device endpoints
While employers don’t need to monitor device activities, they do need to manage and track network traffic from trusted devices. Monitoring NetFlow data like IP addresses and other basic information helps identify unsecured devices attempting to access the network and prioritize BYOD traffic for network availability.
- Education on safe usage
Training and education for BYOD users highlight and reinforce safe practices, such as:
- Not using browser password managers: The use of unencrypted, built-in browser password managers should be discouraged because important user credentials are stored in an unprotected format. Here’s a step-by-step guide to erasing passwords from your browser that you can share with employees.
- Completing software updates regularly: Remote workers should respond to requests to update applications, security patches, OS versions, and master passwords quickly.
- Secure password sharing: Business passwords should never be shared with non-employees or emailed to coworkers. Dashlane provides a secure, encrypted portal for password sharing that makes it easier to distribute company passwords safely.

- Encrypted data transmissions
Everyone should be using encryption, including those using their own devices at work. Encryption is important, especially when public or unsecured WiFi networks are used to connect. Dashlane Password Manager utilizes AES-256 encryption to scramble employee passwords before they leave the device. An additional VPN encrypts all messages and data going in and out of the device to prevent them from getting intercepted.
- Lost or stolen devices
Including a reaction plan for lost or stolen devices in the employee mobile device user agreement is highly recommended. Employees and IT teams should be aware of the tools and practices available to minimize the risk of exposed company data. Remote device wipes, data locks, and password resets (using a password manager) are among the immediate preventive actions that can be taken.
- Provide the best tools
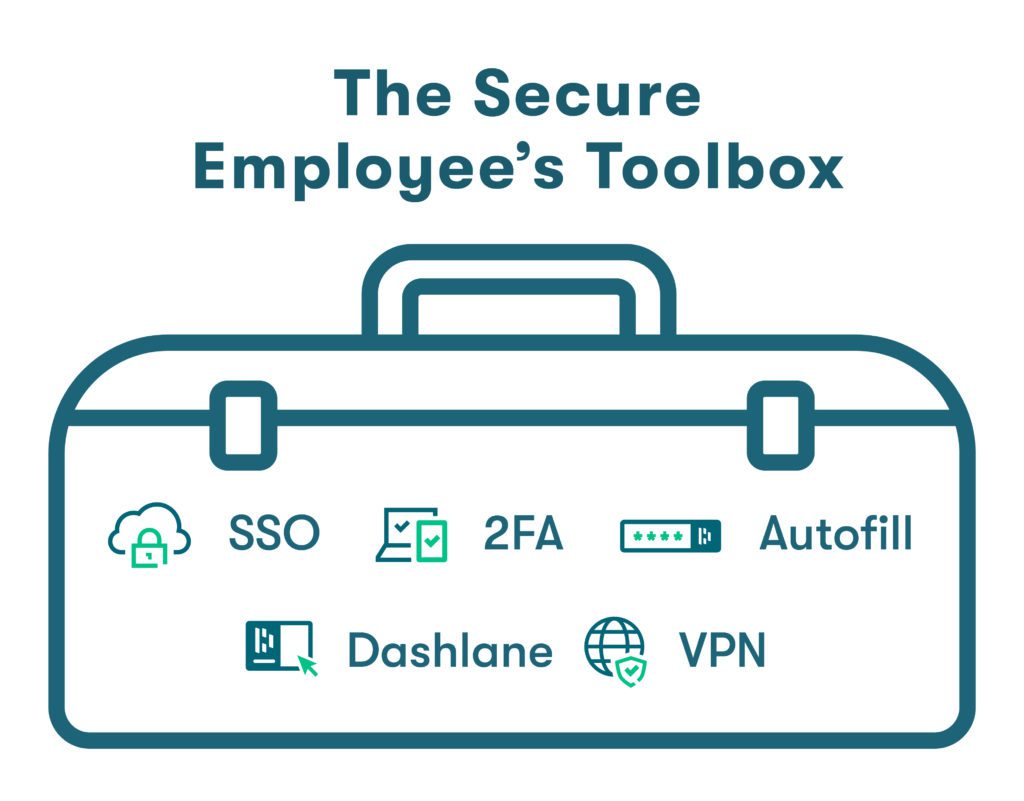
The best security strategies for work-from-home employees and employee-owned devices require tools that work together to strengthen cybersecurity and support the BYOD policy:
- Single sign-on (SSO)
- Autofill of trusted URLs to encourage utilization
- 2-factor authentication to verify employee identity at login
- A VPN to ensure access to secure, encrypted internet service from any location
- A password manager to enable secure password creation, storage, and sharing
- Create a customized BYOD policy
An effective BYOD policy should be an offshoot of a carefully crafted cybersecurity strategy that includes all objectives, steps, and resources used to minimize cyber risk. Some important considerations that feed into the BYOD policy include threat and vulnerability assessments, financial implications of a breach, and an evaluation of existing IT tools.
- Establish a cybersecurity culture
Dispersed employees and devices only increase the need for a unified security culture where each employee takes responsibility for protecting company assets and information while remaining on the lookout for threats like social engineering attacks. Dashlane provides insightful Password Health score tracking to promote password strength and continuous improvement.
How Dashlane secures your employees’ devices
Password management solutions from Dashlane include advanced features like AES-256 encryption, 2FA, and instant password syncing to keep all employee devices secure. User-friendly autofill that only works on trusted URLs boosts adoption and productivity in the workplace, home office, or field, while VPN and Dark Web Monitoring protect workplace boundaries from every angle.
Dashlane allows organizations of all types to protect their financial health and reduce risk.
Find out how Dashlane is helping innovative companies like Solar Quote keep their employees’ devices and credentials secure in a dynamic, hybrid work environment.
References
- Statista, “Mobile internet usage worldwide - Statistics & Facts,“ October 2022.
- TechBeacon, “20 most dangerous mobile apps: How to best mitigate the risk,” 2022.
- Dashlane, “Why Every Employee Device Should Be Secured,” May 2021.
- Dashlane, “A Beginner’s Guide to Two-Factor Authentication,“ August 2022.
- Gartner, “Identity and Access Management (IAM),“ 2022.
- Dashlane, “Best Way to Store Passwords at Home or Work,“ September 2022.
- Exploding topics, “24+ Fascinating BYOD Statistics (2022),” September 2022.
- Dashlane, “Why Do You Need a VPN? Don’t Miss These 3 Key Benefits,“ August 2020.
- ScienceDirect, “Malicious Apps”, 2022.
- Dashlane, “Create a Culture of Cybersecurity: Teach Employees to “Catch a Phish”,“ August 2021.
- Dashlane, “3 Remote Work Security Practices for Your Small Business,” October 2022
- Dashlane, “Why Passwords are the Weak Link in Company Security,” 2022
- ScaleFusion, “Resistance to BYOD: How Containerization Helps,” April 2022.
- Dashlane, “Why Employees Shouldn’t Let Browsers Save Their Passwords,” March 2021.
- Solarwinds, “What is NetFlow?,” 2022.
- Dashlane, “How To Maintain Security When Employees Work Remotely,” October 2022.
- Dashlane, “Cybersecurity Strategy: Best Practices for Small-to Medium-Sized Businesses,“ October 2022.
- Dashlane, “How to Create a Culture of Security,” August 2021.
- Dashlane, “How to Stop Reusing Passwords for Good,“ January 2020.
- Dashlane, “A look at Password Health Scores around the world in 2022,” 2022.
Sign up to receive news and updates about Dashlane
