A Beginner’s Guide to Two-Factor Authentication
Last updated Mar. 27, 2024
What is 2-factor authentication (2FA)?
2FA is an extra layer of security for your account beyond just a username and password. It requires a second credential, in addition to your password, for you to gain access to your account. Any time you log in to an account with a password, and the application texts a code to your phone so you can confirm your identity, you've used 2FA. Other real-world examples of 2FA include:
- ATM transactions–which require both card and PIN
- Gas pumps–where you use a credit card and enter your ZIP code to pay
Embracing 2-factor authentication can help prevent data breaches that require costly mitigation and potentially damage an organization’s reputation. Instead of relying on passwords alone, 2FA increases protection for both the user's identity and private information such as credit card numbers and medical details. Adding a second authentication factor creates a safety net for stolen password databases and phishing scams.
“2FA, MFA, it’s ridiculous how many of these attacks come in because someone didn’t turn on MFA…time and time again if they would have just switched on 2FA, some of these attacks wouldn’t have been possible…the other thing is stop reusing passwords, but if I only get one, 2FA.”
—Nicole Perlroth, Author & Cybersecurity Reporter, Lex Friedman Podcast, Feb 20, 2022
Want to learn more about using a password manager on your own or with friends and family?
Check out our Friends and Family plan or try the Dashlane Password Manager for free.
What are the different types of authentication factors?
An authentication factor is a unique credential that a user inputs to access an online account, such as a password. In general, authentication factors include something the user either knows, is, or has. An effective dual-factor authentication system uses evidence that comes from two of these categories:
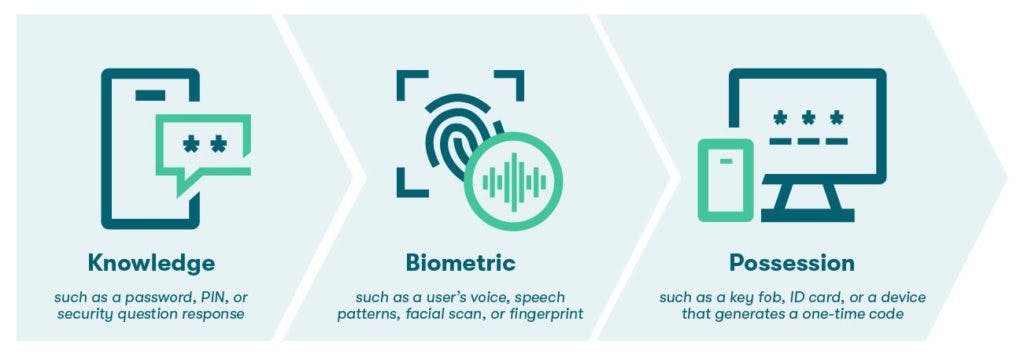
- Knowledge factors such as the person's password, PIN, or security question response
- Inherence or biometric factors, meaning personal attributes such as the user's voice, speech patterns, facial scan, or fingerprint
- Possession factors like a phone or electronic device software that generates a one-time authentication code or a physical token such as a key fob or ID card
A few other authentication factors exist, but they usually don't play a role in two-part authentication. Multifactor authentication may also include a time factor, which means the user has to respond within a certain number of minutes to gain access, or a location factor, which grants or denies access depending on the user's GPS location.
How does 2FA actually work?
The authentication process typically starts with the name and password entry when a site requests a user's credentials (a knowledge factor). If the person successfully enters this information, the system will provide a prompt for the next step in the process. Often, the 2FA software generates a one-time authentication code and sends it to the person's designated device, an example of a possession factor.
The second factor always comes from a different category than the first factor. For example, the system won't ask for two separate passwords or ask for both a fingerprint scan and a face scan.
What are the benefits of implementing 2-factor authentication?
Improving an organization's security from single-factor to dual-factor authentication is associated with four valuable advantages.
Access control for individual files, folders, and drives
When an organization implements 2FA, they can partition their servers and cloud storage spaces to create granular access control for specific folders, files, and drives. This level of security is especially important if they need to maintain collaboration with other departments, vendors, or external stakeholders without compromising data privacy.
Customizable authentication options to suit each user’s preferences
Most dual-factor systems let users select between several different ways of authenticating when they log in to the program. For example, they can choose to approve access on a smartphone authenticator app or enter a one-time authentication code they receive by email. This level of convenience offers a fast, seamless connection, critical in the current landscape with its expanding remote workforce. Meeting employees' expectations for an engaging, secure, and private user experience also helps establish a human-first security culture at the organization.
Compliance with data security and privacy regulations
If an organization must adhere to data security and privacy regulations such as HIPAA for personal health care data or Criminal Justice Information Services (CJIS) compliance for government agencies, 2-factor authentication systems meet the necessary compliance standards. Organizations can also use 2FA if they receive federal grant funding, which requires compliance with the Federal Information Security Management Act (FISMA), or collect consumer credit card information, which falls under the Payment Card Industry Data Security Standard (PCI DSS).
Simple, affordable integration into existing IT systems
In most cases, companies can easily implement 2-factor authentication without adversely affecting their existing IT systems. Dual-factor software is also compatible with single sign-on (SSO) solutions, which keep accounts secure throughout an entire session without requiring repeated log-ins.
How secure is 2-factor authentication?

Nearly all major websites and service providers offered 2FA by 2017, a testament to its efficacy. That year, just 28% of respondents to the Duo Labs State of the Auth survey reported that they'd used 2-factor authentication, which has since increased to 79% of survey participants in 2021.
When properly administered, dual-factor authentication can block these types of attacks:
- Brute force attacks, in which hackers figure out user credentials or break encryption through trial and error
- Dictionary attacks, which attempt to breach systems with combinations of commonly used password phrases
- Phishing, when hackers represent legitimate organizations to try to get users to enter their credentials, and spear phishing, which targets specific victims instead of a massive email database
Organizations may also benefit from the additional layer of protection offered by 2FA if they often have third parties such as vendors and contractors access their digital services and systems. Companies can improve the security of a 2FA system with a physical hardware token, often a USB drive that serves as a "key" and costs around $20.
However, these devices represent a significant investment for large employers, especially since they can also be lost or stolen. Authenticator apps are often a better solution since they generate a code directly on the user's device, so the access key can't be intercepted like it can if sent by text message.
Although 2-factor authentication is better than single-factor security systems, it's not a perfect solution.
Problems with passwords

A security system is as vulnerable as its weakest access point, such as a password that an employee also uses on unsecured sites. The first layer of 2-factor authentication often relies on the imperfect password system, which is vulnerable to:
- Improperly stored login credentials, such as passwords that are written down or kept on old hard drives
- Weak, reused, or forgotten user passwords
- Internal failure to use security best practices
- Rainbow table hacks, using a table of hash values to crack an encoded database
Another common issue? Some 2FA systems don't ask for the second authentication factor when the user requests password recovery and creates new credentials.
According to survey data reported by NIST, 54% of users stick to fewer than five passwords for all the sites and apps they frequent online. The bottom line? With sufficient time and the right tools, hackers can figure out average user-created credentials.
“All it would have taken was one email to be intercepted or for someone to get into our building and find sticky notes with passwords, and our entire network and data would have been compromised.”
—Steven Stanley, Senior VP of Technology, ePromos
SMS vulnerabilities
The most frequently used 2FA method involves receiving a one-time authentication code by text message. However, the system can't verify that you're actually the person who gets the SMS since phone numbers can also be hacked and spoofed. If hackers gain access to your wireless service provider account, they can intercept any message sent your way, including 2FA access codes.
In fact, NIST no longer recommends dual-factor authentication systems that rely on SMS along with a password. However, the Duo report cited above found that text messages remained the most commonly used second 2FA factor in 2021, familiar to more than 85% of survey respondents.
It was also regarded as the most user-friendly second factor and the favorite choice of users, with more than half (53.4%) selecting it as their preference. Only 20.2% opted for the second choice, email, and fewer than 10% of respondents said they would prefer either a mobile passcode, phone callback, security key, push notification, or hardware token when setting up a new account.
What is the future of 2-factor authentication?
Looking ahead, 2-factor authentication will likely grow to meet the security demands of organizations and users alike. These are some of the most notable innovations in 2FA and beyond.
Multifactor authentication
Organizations requiring enhanced information security may want to upgrade from 2FA to multifactor authentication (MFA), which uses three or more authentication methods for each access session. According to Alex Weinert, Group Program Manager for Identity Security and Protection at Microsoft, MFA blocks 99.9% of hacking attempts on the organization's cloud services.
In the most common example of MFA, secure 3-factor authentication systems typically combine a password and physical token with either a fingerprint scan, voice authentication, or another form of biometric security.
According to data from Markets and Markets, multifactor authentication will more than double its current estimated value of $12.9 billion to $26.7 billion by 2027. Driving factors for this growth include:
- A global landscape marked by increasingly strict government regulations
- The exponential increase in online service and retail transactions
- The tidal shift to cloud-based servers and platforms
- The evolving expansion of the Internet of Things (IoT) and bring your own device landscape
- The statistical rise in online identity theft and fraud and the substantial personal and commercial cost of these incidents
Password-free privacy measures
More organizations are pursuing password-free authentication measures. New factors to explore include access based on time of day, type of device, and geographic location. Many companies are also experimenting with behavioral biometrics, such as how users move the mouse, how fast they type, and even the length of each keystroke. With tech innovations like these, organizations may eventually move from 2FA or MFA to continuous authentication.
Despite the imperfections of 2-factor authentication, upgrading from a single-password system to a 2FA model dramatically decreases the likelihood of a costly data breach. Reducing the risk associated with working for, partnering with, or shopping online through an organization, serves as a testament to how well a brand treats their clients and stakeholders.
What’s the best software for 2-factor authentication?
Over 20,000 companies choose Dashlane to protect against data breaches. Dashlane uses 2FA, zero-knowledge architecture, and the strongest 256-bit encryption to offer teams a streamlined user experience without sacrificing critical data security. Reach out today to request a live demo with a Dashlane cybersecurity expert.
Discover how best-in-class password management solutions and SSO can help secure every access point of your organization. Read now: Why You Should Integrate Password Management and SSO.
References
- Individuals use two-factor authentication, biometrics to protect information. Security Magazine.
- Back to basics: What’s multi-factor authentication - and why should I care? NIST.
- Microsoft: Using multi-factor authentication blocks 99.9% of account hacks. ZDNet.
- Facebook's password breach suggests the public sees cybersecurity as obsolete. Forbes.
- 2022 data breach investigations report. Verizon.
- What the hack is 2FA? Dashlane.
- State of the Auth 2021. Duo Labs.
- NIST Special Publications 800-63B. National Institute of Standards and Technology.
- Two-factor authentication. Educause.
Sign up to receive news and updates about Dashlane
Thanks! You're subscribed. Be on the lookout for updates straight to your inbox.
