Balancing Usability & Security in a Remote Office
Cyber threats continue to escalate as remote working, bring your own device (BYOD) policies, and our growing lists of devices and accounts present new opportunities for hackers. While many of the security tools and practices we need to counteract these trends already exist, additional security steps can create frustration or add time to our already overcrowded schedules. Is balancing usability and security possible in a remote office environment?
What is cybersecurity?
Cybersecurity is the practice of protecting devices, files, and users from unauthorized access and data corruption. Cybersecurity measures protect computer systems and networks from both internal (in-office) and external threats.
Security challenges in a remote environment
With remote working, bring your own device (BYOD) policies, and increasing amounts of devices and accounts comes additional security challenges in the workplace. With less oversight and control over device use, password hygiene, and mobility, IT teams can lose visibility into cybersecurity risk factors, especially as remote workers leave or join organizations and password access settings are updated.
The link between user experience and security
Researchers in the field of human-computer interaction (HCI) study relationships between humans and computers. These interactions continue to evolve as computers take on more complex tasks and begin to communicate with humans using plain speech. Human-computer interaction for security (HCISec) is concerned with these interactions as they relate to online security and how the security user experience (security UX) can help to predict security feature acceptance levels. Security feature usability is an especially important consideration for remote workers since complacency and a lack of direct IT team oversight can cause employees to forgo security methods they find inconvenient.
Want to learn more about using a password manager for your business?
Check out Dashlane's business plans or get started with a free business trial.
The issues with a traditional cybersecurity policy
Much has changed in the workplace in recent years, and traditional cybersecurity policies don’t always keep pace with the latest guidance, trends, and best practices. Slowly adapting policies like the ones below can allow new threats and vulnerabilities to go unchecked.
- Policies based on in-house employee models: Security policies based on the traditional model of employees using company-owned computers only in the office and leaving their devices, files, and worries behind each afternoon were upended by the explosion in remote working during the pandemic. Even before the pandemic, many employees worked on a hybrid schedule or brought their office devices home. Today, many businesses are adjusting their cybersecurity policies to balance the needs of both remote and in-house workers in the new hybrid work landscape.
- Taking a reactive rather than proactive approach: Many weaknesses found in traditional cybersecurity policies can be summarized by the tendency to be reactive rather than proactive. Reactive approaches add layers of cumbersome security measures after each incident, while proactive practices identify weaknesses before they occur. The proactive mindset is more effective when dealing with the security variables of a remote workforce.
- Forced password resets: One traditional example of security vs. usability is forced password updates, following policies like 30/60/90-day reset intervals. When we rush to change passwords to comply with predetermined deadlines, we’re likely to only make minor changes based on human nature and optimized usability. The NIST digital identity guidelines explain that these minor changes have little security value since hackers can easily anticipate them.
"We're incentivizing people by offering to waive 30/60/90 password change mandates if they utilize Dashlane."
CIO at Buena Vista University
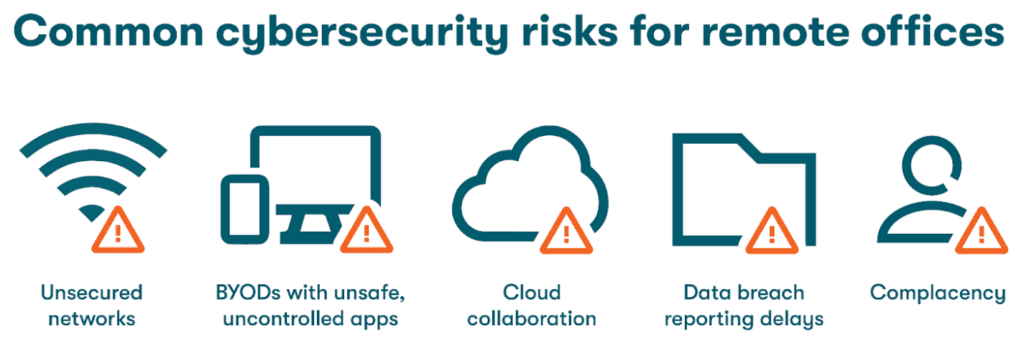
Common cybersecurity risks for remote offices
Not all remote or hybrid workers are exposed to the same security threats, but a few common factors increase security risks for most remote and hybrid offices:
- Unsecured networks: Mobile devices allow us to work from the road more easily, especially with WiFi now available at almost any public or private venue. Home and public WiFi networks are typically not as secure as wired or wireless networks in an office environment since they lack the direct IT support needed to maintain security features like encryption and firewalls. A VPN addresses this risk without compromising usability by encrypting all data going in to or out of a device and routing it through a secure portal.
- BYODs with unsafe or uncontrolled apps: When employees use the same device for personal and work apps, it can become more difficult for IT teams to track how and where the device is used and whether potentially dangerous apps have been installed. Shadow IT involves cases where employees install and use business apps without informing their company’s IT department. This increases risk since the organization’s security tools and protocols don’t protect these apps and their use. Mobile devices taken outside the home or workplace are also more prone to loss or theft, which can involuntarily expose sensitive company data.
- Cloud collaboration: Cloud-based file sharing and collaboration tools have been important enablers of remote working, but they also bring new cybersecurity challenges. Each of these new platforms requires new passwords, and information shared over tools like Slack can be vulnerable to cyberattacks since the unencrypted messages are stored indefinitely. The best cloud collaboration solutions place a premium on database security vs. maximizing database usability.
- Data breach reporting delays: When a data breach impacts a remote worker, it’s more likely to go unreported or unnoticed for a longer period of time. Remote workers can be less connected to IT departments and security policies, which can cause warning signs to be missed. Antivirus security vs. usability factors might cause these workers to bypass important scans and updates. Remote workers might also be fearful of consequences if installing an unsafe app, opening a phishing email, or using an unsecured WiFi network contributed to the breach.
- Complacency: Converting spaces once reserved for personal activities into home offices blurs the separation between home and work, which can lead to security complacency. Remote workers need to be vigilant to avoid lax security habits like reusing passwords and storing them in open, unsecured locations.
How to combat IT risks in a remote office setting
Isaac Newton’s 300-year-old theory states that every action must have an equal and opposite reaction. In recent decades, this has proven this theory to be true about the traditional cybersecurity approach, with a growing number of hacking tactics and threats leading to an equally burdensome list of threat detection and monitoring tools for IT teams. Security vs. usability doesn’t have to be a zero-sum game when you follow some common sense practices and deploy the latest cybersecurity tools:
- Educate employees: Keeping all employees engaged in a culture of security improves cyber threat awareness and reinforces the importance of security tools and practices. Live training forums also allow remote employees to give feedback on the usability of existing security systems and suggest improvements.
- Create a sensible security policy: Putting best practices in a well-designed security policy is an important step towards standardizing the security experience for remote workers. The policy should include rules and expectations for WiFi use, BYOD, and password management. The policy should also be flexible enough to prevent complacency and the security UX from undermining policy adherence.

- Use technology that encrypts passwords and other data: Encryption, or hiding data in an unrecognized format, is a valuable security practice that doesn’t detrimentally impact the security experience since the complex data scrambling and decoding processes happen completely in the background. Encryption is essential for website authentication and password management for remote workers. Dashlane Password Manager uses AES-256 encryption, widely accepted as the strongest encryption type available, to protect passwords and other subscriber data.
- Use 2-factor authentication (2FA): The process known as 2-factor authentication (2FA) uses a second login factor, like a unique code sent through an app or text message, to verify identity. Although this practice can add a few extra steps during login, newer authentication methods use biometric factors like fingerprints or facial recognition. These security UX improvements will help to prevent this valuable practice from being avoided by remote workers due to usability alone.
- Use secured internet connections: A virtual private network (VPN) set to automatically connect and protect remote workers when they use unsecured WiFi networks is another great example of security vs. usability with no potential for inefficiency or UX concerns that prevent adoption. A VPN also provides additional benefits by masking IP addresses to make browsing sessions more private and bypass geographic restrictions.
- Use a password manager: A password manager optimizes the security experience by simplifying steps 1 through 5 with one comprehensive solution while adding the convenience of automatic password generation and autofill. By encrypting all your private data (not just passwords), including 2FA for an added layer of security, and keeping track of your weak, reused, and compromised passwords with a user-friendly Password Health score, Dashlane is changing security UX for the better.
How to balance usability and security in remote office settings
Balancing usability and security can be difficult in remote office settings. Complacency, BYOD devices, and limited IT contact make it easy for workers to err on the side of convenience. Fortunately, new cybersecurity tools like encryption, a VPN, biometric authentication, and password managers are redefining the security experience. When backed by sound security policies and inclusive training for remote workers, the tradeoff between usability and security becomes a relic of the past.
With hybrid work becoming our new reality, what’s the best way for employers, workers, and IT teams to adapt? Learn how to build a more productive, collaborative, and secure workforce by reviewing The Dashlane Guide to Hybrid Work.
References
- Dashlane, “How Businesses with a BYOD Policy Can Secure Employee Devices,” January 2023.
- Dashlane, “A look at Password Health Scores around the world in 2022,” 2022.
- Dashlane, “New Research Uncovers the State of Security in the Workplace,” December 2020.
- Artera, “What is HCI?” February 2022.
- Tresorit, “A great user experience is the best way to keep security levels high,” October 2022.
- Resolver, “How to Adapt Your Remote Work Security Policy for Flexible Teams,” October 2022.
- Dashlane, “How Often Should You Change Your Password for Online Accounts?” January 2023.
- NIST, “Digital Identity Guidelines,” 2022.
- Dashlane, “How To Maintain Security When Employees Work Remotely,” October 2022.
- Dashlane, “Why Do You Need a VPN? Don’t Miss These 3 Key Benefits,” August 2020.
- Cisco, “What is Shadow IT?” 2023.
- Dashlane, “Sharing Passwords Through Slack Is Risky,” November 2019.
- Cloudwards, “Best Cloud Storage for Collaboration in 2023,” January 2023.
- Dashlane, “The Top 3 Reasons Businesses Get Hacked—and How to Avoid Them,” January 2021.
- Dashlane, “Why Dashlane Will Never Ask You for Credentials in an Email (Because That’s How Phishing Works),” November 2021.
- Dashlane, “How to Stop Reusing Passwords for Good,” January 2020.
- Dashlane, “How to Create a Culture of Security,” March 2022.
- Dashlane, “Creating a Password Policy Your Employees Will Actually Follow,” July 2022.
- Dashlane, “What Is Encryption?” March 2019.
- Dashlane, “2-factor authentication (2FA) in Dashlane,” 2023.
- Dashlane, “The Dashlane Guide to Hybrid Work,” 2023.
- Dashlane, “7 Password Hygiene Best Practices to Follow,” February 2023.
- Dashlane, “Case Study: The Cybersecurity Strategy Buena Vista University Used to Secure 29+ Departments,” May 2022.
Sign up to receive news and updates about Dashlane
