What Is a Zero-Day Vulnerability?
When hackers know something security teams don’t, time is the enemy of those security teams. This is evident when spyware slowly and secretly gathers information or ransomware holds valuable files and devices hostage until a solution is found. Zero-day vulnerabilities are another cybersecurity issue that calls for a fast and accurate response. But what is a zero-day exploit, and why are they dangerous?
Zero-day definitions and terms
The term zero-day refers to a software developer having zero days (no time) to fix a defect after it’s brought to their attention. With no defense in place, zero-day conditions create severe security threats—and valuable opportunities for malicious hackers. White hat hackers are sometimes paid a bounty to discover zero-day vulnerabilities before bad actors can exploit them.
Here are the zero-day terms it’s important to understand:
- Zero-day vulnerability refers to a defect or weakness the developer isn’t aware of and therefore hasn’t corrected. Zero-day vulnerabilities can be found in software applications, operating systems, or devices.
- Zero-day exploits are hacking tactics carried out to benefit from the zero-day vulnerability. Some common strategies include phishing, brute force attacks, and drive-by downloads.
- Zero-day attacks occur when cybercriminals exploit the vulnerability to cause damage. For example, the attacker may disrupt service or steal credentials before the organization has a chance to update the software or release a patch.
Want to learn more about using a password manager for your business?
Check out Dashlane's business plans or get started with a free business trial.
What makes a vulnerability a zero-day?
What does zero-day vulnerability mean? There’s no perfect software or best method to find every exploitable flaw. With cyberattacks increasing in frequency and severity, let’s expand upon the zero-day vulnerability definition:
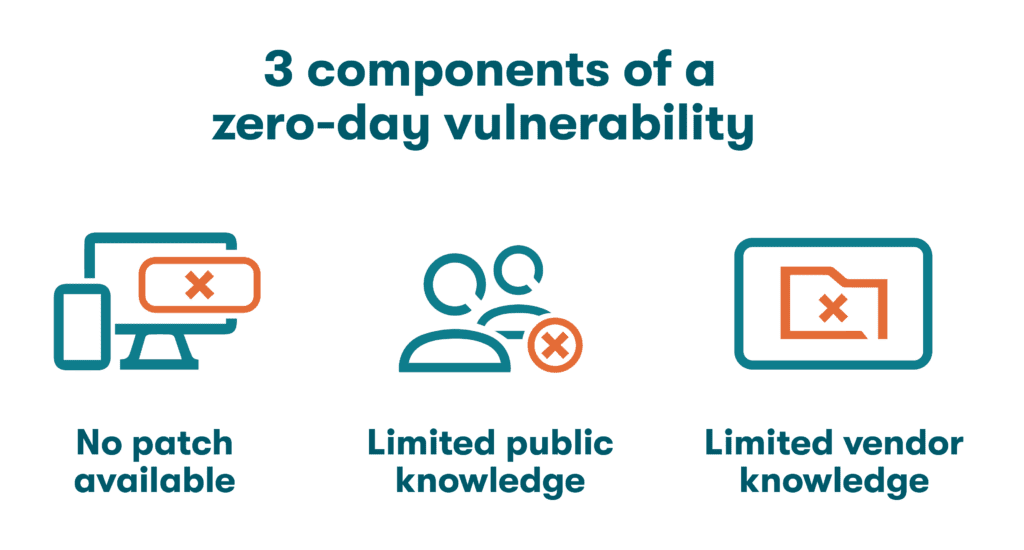
- No patch available: One of the most important distinguishing characteristics of a zero-day is the fact that no patch has been created. Rather than issuing an all-new software release, a patch can be released quickly to address a specific vulnerability. Although patches are often distributed to customers quickly, zero-day attacks take advantage of the brief window before this is completed.
- Limited public knowledge: Zero-day vulnerabilities are typically unknown to the public since they are newly discovered and undocumented. This also plays into the hands of hackers since businesses and individuals using the vulnerable software won’t be warned about or protected from the zero-day attack.
- Limited vendor knowledge: Even the software vendor who developed and sold the product is often completely unaware of the defect until after the first attack has been carried out. This leaves vendors in the unenviable position of needing to resolve the problem after the hackers have a substantial head start.
Examples of zero-day vulnerabilities
Computer industry leaders must contend with zero-day threats on a daily basis. Many common traits and patterns are found in recent zero-day attack examples:
- Google (2023): In April of 2023, Google announced a zero-day vulnerability impacting the Chrome Desktop browser that was discovered in the wild, meaning outside of their controlled testing environments. This vulnerability impacted the JavaScript engine in combination with the unpatched Chrome browser. A zero-day exploit based on this vulnerability would have allowed cybercriminals to corrupt systems remotely using a spoofed HTML page. Since the defect was found in the wild, the NIST classified the severity as high, and a patch was urgently rushed out to customers.
- Microsoft (2023): An unpatched vulnerability in Microsoft Office and Windows products was discovered in the wild and exploited by a hacker in attacks against government agencies in Europe and the United States. The hacker also targeted several scheduled guests of an upcoming NATO summit. This zero-day vulnerability, disclosed by Microsoft in June of 2023, enabled remote code execution on the target’s computer. At the time of disclosure, Microsoft hadn’t yet patched this vulnerability, so they advised all organizations to take strong mitigation and prevention measures.
- Apple (2021): Zero-day vulnerability news isn’t always bad. In 2021, cybersecurity Ph.D. student Ryan Pickren detected a zero-day vulnerability on the Apple Mac operating system that might have allowed hackers to take control of a computer’s camera remotely. Apple rewarded Pickren with a $105,000 bounty for discovering and reporting this flaw. This wasn’t the first time this scholar-turned-white-hat hacker had prevented a zero-day exploit for Apple. In 2019, he was awarded a $75,000 bounty after discovering serious vulnerabilities in the iPhone camera and microphone components.
- Sophos (2020): Firewall maker Sophos experienced a zero-day attack that exploited an unpatched SQL injection flaw in one of their products. The hackers also used this firewall interface vulnerability to infiltrate company networks and distribute evasive malware capable of hiding in system memory. The hackers then stole Sophos subscribers’ usernames, passwords, and other sensitive data. The damage done by this sophisticated attack was minimized by a speedy root cause investigation and a hotfix issued within days.
- Internet Explorer (2019): As a frequent target, Microsoft has developed streamlined vulnerability testing and patch management systems that are designed to squash as many defects as possible before cybercriminals can raise an attack. One such vulnerability found on the Internet Explorer web browser, dubbed CVE-2019-1367, was detected in 2019. Had the vulnerability been discovered by hackers first, it would have allowed them to take full control of someone’s system to steal data, install malware, or set up bogus accounts.
How to reduce the likelihood of zero-day vulnerabilities
Luckily, many proactive cybersecurity tools and practices are available to help lessen the impact of zero-day attacks. A complete zero-day mitigation strategy should include:
- Vulnerability scanning. This tactic uses software tools to simulate attacks so vulnerabilities can be located and fixed before hackers identify them. These software tools continue to improve but still can’t find every vulnerability. However, when severe issues are detected, they should immediately signal an all-hands-on-deck effort to review the code and fix the vulnerability before it’s exploited.
- A patch management strategy. Applying patches might sound more like a reactive solution, but an effective patch management strategy can lessen the impact of zero-day vulnerabilities. This includes streamlining or automating the process so that patches are distributed to users faster, and the most serious defects are prioritized. Virtual patching is an effective interim strategy to block behaviors that can exploit the vulnerability before the patch has been implemented.
- Antivirus software. Hackers often use malware as a convenient method to exploit a vulnerability from the inside. The threat of zero-day attacks makes it important to delete and report phishing emails, especially those that include suspicious links or attachments that might harbor malware. The best anti-malware or antivirus software packages provide an added layer of protection by continually scanning, quarantining, and removing infected files and using cloud-based updates to adapt to new threats and vulnerabilities.
- Firewalls. Network security devices, known as firewalls, are a traditional prevention method that filters all incoming and outgoing traffic and blocks suspicious data based on predefined rules. Firewalls can be hardware, software, or cloud-based and are an effective tool to prevent zero-day attacks, using file inspection capabilities to block zero-day malware. They can also be adapted quickly based on the latest threats to prevent zero-day attacks before a software fix has been implemented.
- Endpoint protection: In addition to traditional firewalls, a focus on securing network endpoints or entry points, including mobile devices and laptops, to protect them from threats like zero-day exploits is becoming a valuable and popular security strategy. Endpoint protection systems have evolved from traditional antivirus software and firewalls into more comprehensive tools that also include intrusion detection systems and other advanced security features.
- Intrusion detection systems (IDS). Specialized software applications can effectively detect suspicious network activity. An intrusion detection system (IDS) monitors for unusual traffic patterns and protocol violations associated with zero-day attacks and other types of cyberattacks. The IDS can also be provided with threat intelligence data based on recently discovered vulnerabilities to help the system identify potential warning signs and issue alerts.
- Bug bounties. There’s no shortage of computer experts looking for new ways to monetize their skills. Offering bug bounties to white hat hackers and security researchers who discover zero-day vulnerabilities before hackers can exploit them solves an important problem while putting their expertise to use. Using platforms like HackerOne, vulnerabilities are reported to the software vendor discreetly so they can be fixed before they’re exploited. The bounty amount is typically based on the severity of the defect.
- Training and awareness. Along with cybersecurity training related to phishing, malware, and social engineering, it’s important to train all employees on the dangers and warning signs of zero-day vulnerabilities. Organizations should train employees to identify and report any suspicious activities they observe. Security training should stress the importance of keeping patches updated and the potential consequences of lax security practices and poor password hygiene.
- Password management. Effective password management is an important tool for minimizing the impact of zero-day vulnerabilities and exploits. The best password managers raise your security profile by creating strong and unique passwords for each account, then storing them in a secure, encrypted vault. This helps to protect organizations from hackers who steal or guess passwords to gain system access. Features like a password health score increase each employee’s awareness of their weak, reused, and compromised passwords.
- AI in cybersecurity. Artificial intelligence and generative AI have become hot-button topics based on the utility of interactive tools like ChatGPT, and AI is also becoming an invaluable cybersecurity asset. Security experts already use AI to monitor traffic and search for unusual patterns or malicious behavior. Real-time threat detection and response systems and automated patch management processes also benefit from the use of AI-driven security tools.
Passwords exist to keep your data safe, but they also represent one of the biggest vulnerabilities in your cybersecurity. Learn more about the latest industry trends and discover why password managers are so valuable in Password Management 101.
How Dashlane helps mitigate zero-day attacks
Tools and practices that minimize the impact of zero-day attacks combine prevention, detection, and quick response times to keep risks in check. A password manager supports this strategy by minimizing weak and reused passwords and encrypting passwords to prevent unauthorized access. Additional features like a VPN, 2-factor authentication, a secure sharing portal, and Dark Web Monitoring round out a comprehensive cybersecurity solution.
Dashlane’s patented zero-knowledge architecture ensures that no one, including Dashlane, can access your private information. If Dashlane were to be breached, the cybercriminals wouldn’t see your unencrypted data.
Dashlane maintains the highest level of internal security while delivering the same level of data protection and peace of mind to customers. Finding vulnerabilities before they’re exploited is part of that strategy. Find out how Dashlane’s bug bounty program helps us be more secure.
References
- Dashlane, “Interview With a Hacker: Rachel Tobac Tells You How to Defend Yourself From…Well, Her!” March 2021.
- Dashlane, “How Dashlane’s Bug Bounty Program Helps Us Be More Secure,” May 2023.
- Trend Micro, “Drive-by Download,” 2023.
- Embroker, “2023 Must-Know Cyber Attack Statistics and Trends,” June 2023.
- Heimdal, “What Is a Software Patch?” 2023.
- Nordic Defender, “How to Handle Zero-day Vulnerability? Methods and Strategies,” October 2022.
- Security Week, “Google Warns of New Chrome Zero-Day Attack,” April 2023.
- Symantec, “Attackers Exploit Unpatched Windows Zero-Day Vulnerability,” July 2023.
- Digital Trends, “Apple paid a student $100,000 for successfully hacking a Mac,” January 2022.
- Ars Technica, “Attackers exploit 0-day code-execution flaw in the Sophos firewall,” April 2020.
- Dashlane, “6 Things a Safe Username Should Always Do,” February 2023.
- TechTarget, “hotfix,” 2023.
- We Live Security, “Microsoft rushes out patch for Internet Explorer zero‑day,” September 2019.
- Dashlane, “Data Breach or Hack? Know the Difference,” June 2021.
- Trend Micro, “Security 101: Zero-Day Vulnerabilities and Exploits,” October 2019.
- Dashlane, “Why Dashlane Will Never Ask You for Credentials in an Email (Because That’s How Phishing Works),” November 2021.
- Trellix, “What is Endpoint Security?” 2023.
- AT&T Business, “Intrusion Detection Systems (IDS) explained,” 2023.
- Dashlane, “7 Password Hygiene Best Practices to Follow,” February 2023.
- Dashlane, “How Password Managers Work: A Beginner’s Guide,” December 2022.
- Dashlane, “A look at Password Health Scores around the world in 2022,” 2022.
- Dashlane, “Strange Security: What to Know About Generative AI and Cybersecurity,” June 2023.
- Dashlane, “Build the Case for a Password Manager in 8 Steps,” 2023.
- Dashlane, “2-factor authentication (2FA) in Dashlane,” 2023.
- Dashlane, “Dark Web Monitoring,” 2023.
- Dashlane, “A Deep Dive into Dashlane's Zero-Knowledge Security,” 2023.
- The Hacker News, “Beware of an Unpatched Microsoft Word 0-Day Flaw being Exploited in the Wild,” April 2017.
- Investopedia, “Zero-Day Attack,” September 2022.
Sign up to receive news and updates about Dashlane
