What Is Ethical Hacking & Why Is It So Important for Cybersecurity?
Can hacking ever be ethical? When done for the right reason and with the right controls in place, hacking is both ethical and necessary. Computer experts are putting their knowledge to work to help companies protect customers, data, and assets. Let’s take a closer look at ethical hacking and the reasons it’s so important in the digital age.
What is ethical hacking?
A hacker is a computer expert who uses their skills to access private data or interfere with computer systems, but not all hackers are cybercriminals. In many cases, hackers are hired or encouraged by an organization to seek out system vulnerabilities and potential sources of data breaches in a controlled fashion. Ethical hacking is performed by people known as authorized hackers or white hat hackers. As malicious hacking tactics continue to expand, the demand for ethical hacking has followed suit.
Want to learn more about using a password manager for your business?
Check out Dashlane's business plans or get started with a free business trial.
How ethical hacking differs from malicious hacking
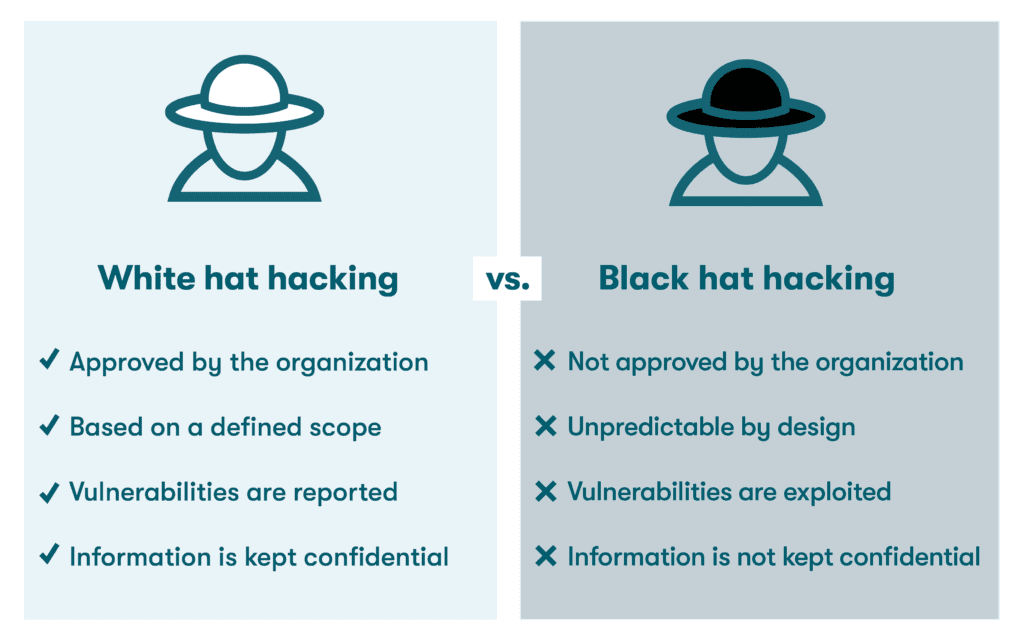
While the methods of ethical hacking share some common traits with malicious hacking, there are also some important differences. Malicious (black hat) hackers launch their cyberattacks for their own personal gain, with little regard for laws, penalties, or negative consequences for the hacked organization. In contrast, the characteristics of ethical hacking include:
- Approval by the organization: This is perhaps the most important distinction, because ethical hacking is approved or requested by the organization being hacked while malicious hacking is not. Ethical hackers can be independent consultants, in-house employees, or third-party consulting firms. Bug bounties with competitive payouts are often provided to independent ethical hackers in exchange for the vulnerabilities they discover.
- Defined scope: Malicious hacking is unpredictable by design to keep IT and security teams guessing. Ethical hacking is based on a defined scope that is agreed upon before any work takes place. This ensures the organization is aware of the hacking activities and won’t raise security alarms if unusual activities are detected on the network.
- Reported vulnerabilities: Ethical hacking follows a strict code of conduct that requires all discovered vulnerabilities to be reported back to the organization being hacked, even if they were discovered inadvertently or were outside the original scope. This principle of responsible disclosure gives the organization a chance to correct or patch the vulnerability before it’s exploited by malicious hackers.
- Confidential information: It’s equally important to ensure no one outside of the targeted organization learns about the vulnerabilities and security risks that are discovered. Confidentiality agreements help detail how ethical hackers should handle and protect private information.
Examples of ethical hacking
There are many types of ethical hacking tools and practices available to make reconnaissance, scanning, and evidence removal easier. Tactics commonly employed by these white hat hackers include:
- Penetration testing. Ethical hacking often includes penetration testing to intentionally breach company apps, devices, servers, and firewalls. Penetration testing or pen testing simulates a cyberattack to check for vulnerabilities using a systematic approach in a controlled environment. The amount of system information shared with the hacker in advance varies depending on the system and testing goals. The elements of penetration testing include:
—Internal testing. Ethical hacking tactics can also be launched from within the firewall to assess the impact of internal security threats. These internal threats can stem from disgruntled or unethical employees, ex-employees who retain company credentials without authorization, or bring your own device (BYOD) policies that allow employees to transfer malware and other cybersecurity threats from their private files.
—Social engineering. Phishing scams, poor password hygiene, and lax authentication can also introduce security risks and vulnerabilities. Social engineering uses psychological principles, deception, and impersonation to gain unauthorized access to systems and data. Ethical hacking pen testing can incorporate these social engineering tactics to test the resilience of human defenses and cybersecurity training.
—Web application testing. Web applications can be tested through ethical hacking to determine if authentication practices and encryption protocols are secure and the user experience is protected. The ethical hacking methodology also includes a review of web applications for susceptibility to vulnerabilities like SQL injections and cross-site scripting (XSS). - Infrastructure scanning. Hackers can locate weaknesses in a network through a process known as port scanning. Messages are sent to network ports by the hacker to determine which ports are open and which services may be vulnerable based on the responses. A port scan helps an ethical hacker map the network topology and gain insight into potential entry points and security system effectiveness. Infrastructure scanning takes this process a step further by identifying other vulnerable elements, including network systems and applications after the port status has been assessed.
Why is ethical hacking so important for cybersecurity?
The importance of ethical hacking cybersecurity practices becomes obvious when potentially serious and expensive security failures are prevented. Notably, ethical hacking can:
- Find vulnerabilities before they’re exploited. Zero-day vulnerabilities are defects or weaknesses that are discovered before the vendor has a chance to correct them. These vulnerabilities can lead to zero-day attacks when malicious hackers discover and exploit vulnerabilities before an update or patch is in place. One of the most important ethical hacking benefits is the ability to find and correct vulnerabilities before the bad guys are aware of them.

- Provide an independent assessment. An ethical hacker can provide a fresh set of eyes to identify vulnerabilities the internal team might have missed while bringing different skills and experience to the table. For this reason, many companies consult with external ethical hackers even when they have their own internal team established.
- Verify strength of security infrastructure. A well-rounded ethical hacker will have in-depth knowledge of software programming and scripting, as well as an understanding of computer network architecture, database construction, WiFi security, and cloud computing principles. This holistic knowledge allows an ethical hacker to connect the dots between isolated vulnerabilities and broader security infrastructure weaknesses.
- Test incident response. In the absence of a real cybersecurity incident, how will you know if your team is prepared? Simulated attacks give cybersecurity teams a chance to test incident response plans, cybersecurity training effectiveness, and existing security policies. The team develops their incident handling skills without the business and regulatory pressures of an actual cyberattack.
Benefits of ethical hacking
Organizations of all sizes and types are realizing the positive value of hacking and using it to strengthen their security posture. Ethical hacking benefits include:
- Reduced chances of data breaches: The primary benefit of ethical hacking is a reduction in the frequency and severity of data breaches. When vulnerabilities are found by ethical hackers first, the organization can take appropriate steps to patch or fix them before they can be exploited by malicious hackers. Ethical hacking also provides an ongoing assessment of security policies to ensure they encompass the latest threats.
- Improved test tools and practices: Cybersecurity tools like endpoint protection software, password managers, and encryption can be fully evaluated in the face of real-world cyberattacks. By simulating new attack vectors, ethical hacking exposes weaknesses and gaps in existing security systems. This ongoing cycle also allows white hat hackers to sharpen their own toolkits and develop new test practices as their understanding of the security infrastructure grows.
- Stronger security culture: A culture of security is one where all employees understand and encourage positive cybersecurity practices, remain vigilant against phishing and other forms of social engineering, and understand how their actions impact the security of the organization. Ethical hacking improves the security culture by demonstrating the real-world impact of cybersecurity threats to employees without the inherent threat to company assets.
- Better regulatory compliance: Ethical hacking helps companies stay in compliance with continually evolving cybersecurity requirements, including ISO 27001 and the General Data Protection Regulation (GDPR), by demonstrating a commitment to protecting customer data and eliminating security threats. Controlled tests and simulations can verify security mechanisms are adequate based on regulatory requirements.
How ethical hacking helps Dashlane be more secure
Dashlane maintains the highest level of security to protect the passwords, digital identities, and personal information of our customers. Ethical hacking plays a big role in maintaining this high standard. The Dashlane bug bounty program, launched privately in 2015 and publicly in 2017, leverages the skills and expertise of thousands of security experts and white hat hackers to improve our security profile, with impressive results.

In addition, the patented Dashlane zero-knowledge architecture ensures that no one, including Dashlane, can access your private information. Even if Dashlane were to be hacked, the cybercriminals wouldn’t see your unencrypted data.
The methods cybercriminals use to compromise businesses are changing fast. You don’t have to be a white hat hacker to understand the basics of cybersecurity when you read our business guide to data breaches and hacks.
References
- Dashlane, “8 Hacker Protection Tips To Keep Your Online Accounts Safe,” May 2023.
- Dashlane, “Interview With a Hacker: Rachel Tobac Tells You How to Defend Yourself From…Well, Her!” March 2021.
- HackerOne, “What Are Bug Bounties? How Do They Work? [With Examples],” July 2021.
- Indeed, “What Is Ethical Hacking? (With Examples and Types of Hacker),” December 2022.
- Bugcrowd, “What is Responsible Disclosure?” 2023.
- Imperva, “Penetration Testing,” 2023.
- Dashlane, “BYOD Policies for Organizations (4 Examples),” June 2023.
- Dashlane, “You Asked, A Hacker Answered: 7 Questions With Rachel Tobac,” October 2021.
- Dashlane, “What is Encryption?” March 2019.
- TechTarget, “SQL injection (SQLi).”
- TechTarget, “Cross-site scripting (XSS).”
- Fortinet, “What Is a Port Scan? How to Prevent Port Scan Attacks?” 2023.
- Cybersecurity Guide, “A complete guide to becoming an ethical hacker,” June 2023.
- Dashlane, “7 Business WiFi Security Best Practices To Protect Your Company,” June 2023.
- Dashlane, “Creating a Password Policy Your Employees Will Actually Follow,” July 2022.
- Dashlane, “3 Strategies to Prevent Breaches and Hacks at Work,” September 2021.
- Dashlane, “Build the Case for a Password Manager in 8 Steps.”
- Dashlane, “No Shortcuts: Why a Culture of Security is So Important,” January 2023.
- IT Governance, “ISO 27001 vs SOC 2 Certification: What’s the Difference?” January 2023.
- Investopedia, “General Data Protection Regulation (GDPR) Definition and Meaning,” November 2020.
- Dashlane, “How Dashlane’s Bug Bounty Program Helps Us Be More Secure,” May 2023.
- Dashlane, “A Deep Dive into Dashlane's Zero-Knowledge Security,” 2023.
- Dashlane, “A Business Guide to Data Breaches and Hacks,” 2023.
- Dashlane, “A Guide To External Security Threats in 2023,” May 2023.
Sign up to receive news and updates about Dashlane
