7 Reasons Why 2-Step Verification Is Always Worth the Extra Effort
Last updated Mar. 27, 2024
We log in to dozens of online accounts each day and unlock everything from offices to bank accounts through a combination of physical and digital authentication. Like a locked box inside a safe, many of these authentication processes ask us to identify ourselves more than once. Our overcrowded schedules make us wonder if the time spent on extra security is really necessary—is 2-step verification worth it?
What is 2SV?
2-step verification (2SV) is a security process that requires people to successfully identify themselves in two different ways before they can gain access to a secure system. 2SV enhances security by asking people to provide something beyond just their password—something that hackers or password thieves are unlikely to have. Sensitive processes like ATM transactions have been using 2SV for decades to protect consumers.
In the physical world, this double-lock concept has been practiced for centuries, as visitors often identified themselves twice when entering secure buildings or forts and presented guards with identifying documents or secret codes along the way. This idea is now commonly seen in the digital world: Codes are sent to devices to supplement password security, or a combination of facial recognition and a PIN code is required to unlock a smartphone.
How does 2SV work?
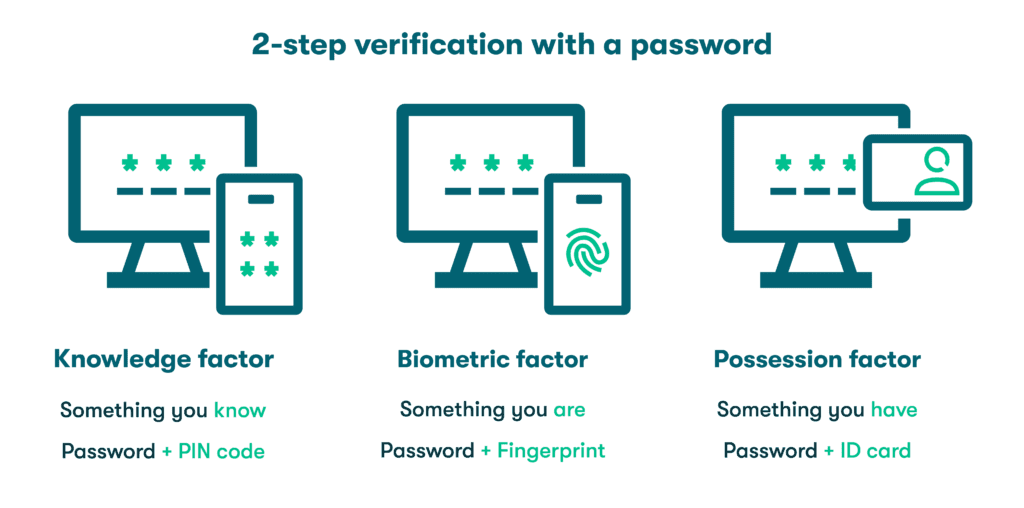
2-step verification is more effective than traditional single-factor verification that only considers a username and password combination. To make the verification steps more challenging for outsiders or hackers to replicate, 2SV draws on authentication factors from three different categories:
- Knowledge factors: The most commonly used authentication factors today are knowledge factors, or something you know. Passwords are the most familiar knowledge factors, but this category also includes PIN codes or answers to security questions, such as your mother’s maiden name or the make of your first car. Ideally, a knowledge factor is something only you know.
- Biometric factors: Inheritance or biometric factors are based on the unique genetic characteristics of each individual. This includes fingerprints, facial recognition, and even vocal characteristics that no two people on earth share. Artificial intelligence and computing capacity continue to bring new biometric factors like retinal scanning into the fold while improving our ability to discern minor differences between individuals and weed out fraud.
- Possession factors: Possession factors refer to physical items you have that no one else would possess under ordinary circumstances. Obvious examples are smartphones and thumb drives, but possession factors also include objects like security keys and ID cards that we tend to keep close to protect them from loss or theft.
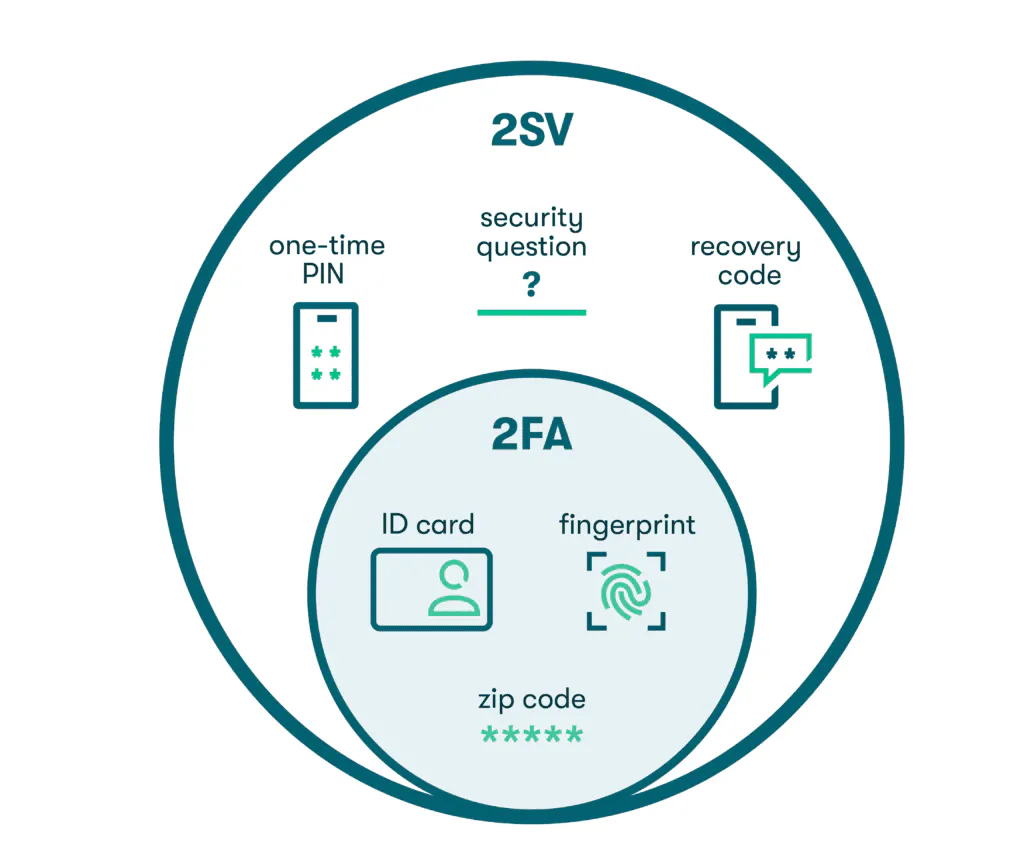
Difference between 2SV and 2FA
2-step verification (2SV) and 2-factor authentication (2FA) are often used interchangeably, but there are some subtle differences between the two practices. 2-step verification (2SV) requires two sequential verification steps, such as a username/password combination followed by a code. Note that the password and code are both considered knowledge factors.
On the other hand, 2-factor authentication (2FA) utilizes two distinct authentication factors that must be from two different categories, such as knowledge and inheritance. An example would be a password followed by a fingerprint scan on your phone.
Since 2FA uses two authentication factors, it also meets the definition of 2SV. However, the opposite is not always true since 2SV doesn’t necessarily use two different categories of identifiers.
7 reasons why 2SV is worth it
Adding an additional layer of verification provides reinforcement to a standalone password. 2SV makes it more difficult for malicious actors to access private accounts because they must obtain not one, but two forms of authentication. Using authentication factors from multiple categories (such as knowledge + possession or knowledge + biometric) further enhances security by requiring unrelated information that’s not easy to guess or replicate.
Furthermore, 2SV has become so commonplace that we don’t often realize we’re using it. Think of a resident entering an apartment building or housing complex gate by entering a secret code. They will still need a second sequential factor (key) to unlock their front door. 2SV has become an essential security practice by offering:
- Protection from hacking and data breaches. Many common hacks and scams rely on compromised or stolen passwords to gain unauthorized access. Brute-force attacks use algorithms to guess at passwords, while credential stuffing attacks attempt to find matching accounts for passwords purchased on the dark web. Neither of these hacking tactics alone has any impact when 2SV requires the hacker to produce additional knowledge, possession, or inheritance factors.
- Protection from phishing. The social engineering tactic known as phishing utilizes emails that appear to be from reputable sources to trick unsuspecting recipients into sharing their credentials, revealing personal information, or clicking on unsafe links. Like other malicious hacking tactics, phishing attacks are used to illegally obtain user credentials that can be sold or exploited. A second identifier can reduce the likelihood of a successful phishing attack.
- Identity protection. Over 1 million cases of identity theft were reported in the U.S. in 2022 alone. Some identities were stolen for the purpose of stealing money and opening fraudulent accounts, while others involved medical or legal information used for impersonation scams. 2-step verification provides protection from identity theft by further restricting access to accounts like social media and email that reveal volumes of personal information.
- Mobile device security. Protecting mobile devices has taken on new importance due to the mobility of today’s workforce and bring your own device (BYOD) policies. 2SV is an effective way to keep the company and personal data stored on your mobile devices safe, even when a device is lost or stolen. Inheritance factors such as fingerprints and facial recognition have been well received by mobile device users based on a combination of security and ease of use.
- Privacy protection. Data privacy laws and policies help us to control how our own personal information is collected, stored, and shared while ensuring companies take steps to prevent consumers from being hacked. By providing a secondary authentication gate, 2SV helps to secure data privacy for businesses and consumers. Along with data encryption and password managers, 2SV is viewed as one of the most important and effective data security tools available.
- Account recovery. When you’re locked out of an account, 2SV can become a useful recovery method. A secondary factor, such as a code sent through an email or text, can be used to reset your password and recover the account. During the recovery process, 2-step verification is applied in reverse order when the code is entered first, followed by the recreated password.
- Maintaining regulatory compliance. Strengthened authentication is an important regulatory compliance element that weaves its way through consumer privacy, data protection, and payment handling regulations established by the PCI DSS security standard. Complying with applicable regulations can be a driving factor for implementing 2SV, although many companies have already realized the benefits of this practice for themselves and their customers.
Examples of 2SV in use
2-step verification is all around us and can even be found in unsuspecting locations like supermarkets, offices, and vehicles. Examples of common 2SV applications include:
- ATM transactions: Using a debit card to bank or shop might not seem like an example of 2SV until you examine the process. First, you insert the card into a reader to begin the transaction. The card is a possession factor since it’s something tangible that only you possess. The PIN you use to complete the transaction is a knowledge factor that confirms your identity.
- SMS codes: A familiar verification process common to both 2SV and 2FA are the text message codes so often required to gain account access, especially for banking, government service, and other secure websites. After providing your password, you complete a second verification step by entering a four- to six-digit code received in a text or email.
- Push notifications: Push notifications are the pop-up messages that appear on a person’s device to remind them when additional action is required. To use push notifications, the person will need to register their device or install an appropriate app. Since the authentication is sent to the device, rather than through text or email, push notifications are considered a possession factor.
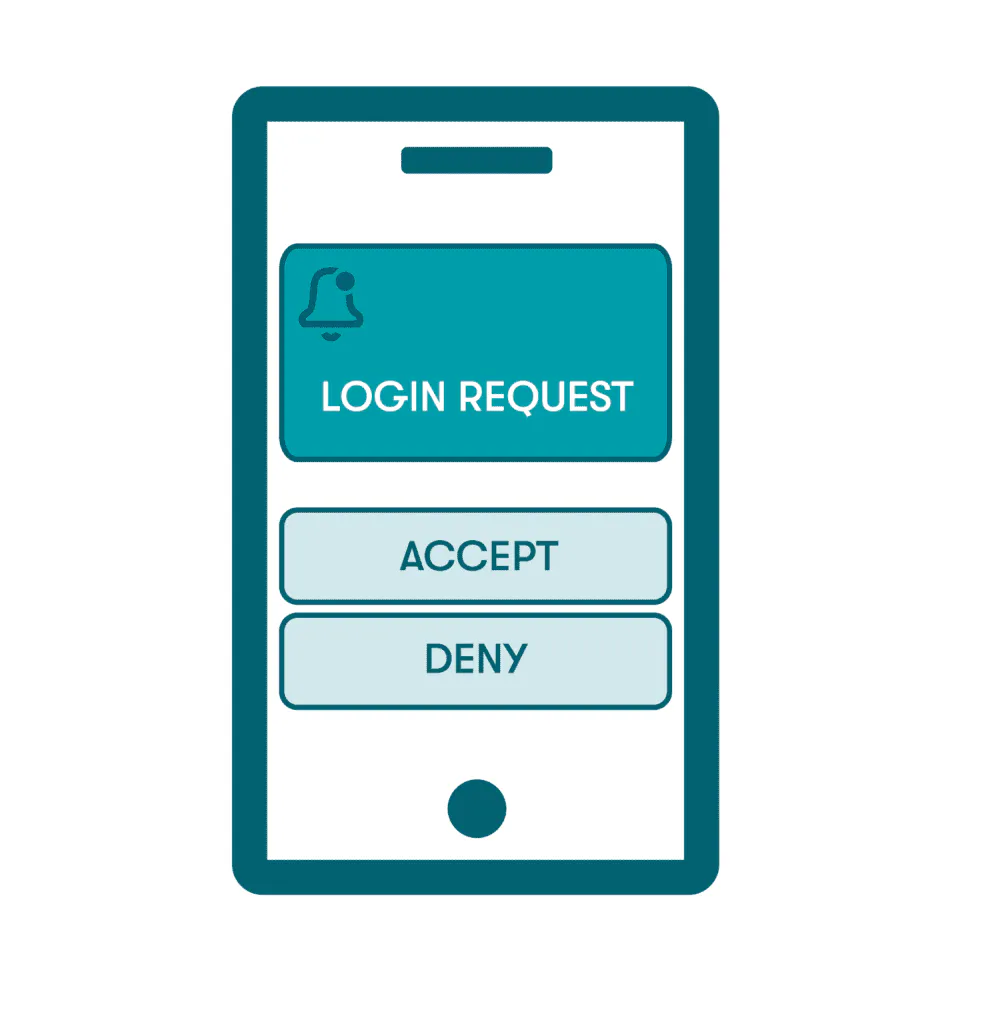
- Authenticator apps: An authenticator app can be installed on a mobile device to support 2SV by generating security keys within a specific time window. Time-based algorithms generate random codes that time out quickly, so there’s no risk of lost or stolen codes. Much like the other commonly used secondary factors, authenticator apps are typically used in conjunction with traditional passwords.
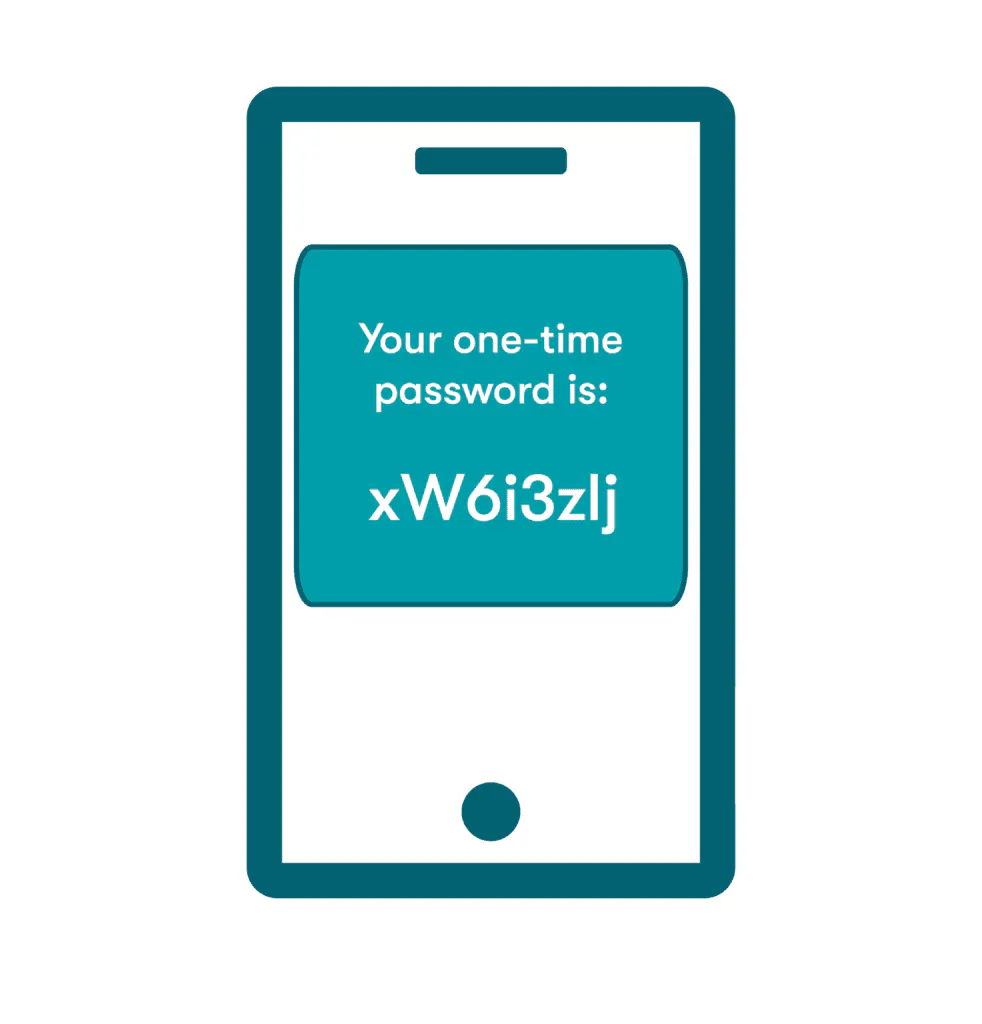
- One-time passwords: A one-time password (OTP) works much like an alphanumeric version of a text message code, since it can only be used to access an account once and has no value after the login is completed. Time-based one-time passwords (TOTPs) might be active for as little as 60 seconds before a new OTP is needed. As a highly secure knowledge factor, one-time passwords are also used during the account recovery process.
- Biometric methods: Biometric inheritance factors and other passwordless authentication methods are quickly gaining momentum as the technology improves. With 81% of hacking-related breaches leveraging weak or stolen passwords, biometric methods are viewed by security experts as a strong, long-term 2SV option that reduces data breaches and improves the user experience.
- Security questions: The make of your first car and name of your elementary school might be etched in your memory for a good reason. Security questions are regularly deployed as a 2SV tool, especially when people are logging in from unfamiliar devices or locations and security is ramped up. Since a password/security question combination leverages two knowledge factors, it provides an example of a 2SV authentication process that does not qualify as 2FA.
How Dashlane uses 2SV to protect your data
Dashlane’s patented security architecture uses the benefits of 2SV to protect your data in many important ways. When you log on to a new device using your Master Password, we send a code to your email address to complete the 2SV process.
Dashlane provides secure, encrypted vaults for password storage and sharing that protect all your data. Features, including a Password Health score and a VPN, improve your password hygiene, while Dark Web Monitoring scans the depths of the internet for your credentials and alerts you if they’ve been impacted. Patented zero-knowledge architecture ensures that no one, including Dashlane, can access your unencrypted passwords and personal information.
Much like valuable 2SV practices, embracing 2-factor authentication (2FA) can help you prevent data breaches and protect your privacy.
Get started with implementing the most critical 2FA best practices by reading A Beginner’s Guide to 2-Factor Authentication.
References
- Dashlane, “What a Secure System Is & How to Implement It in Your Business,” October 2022.
- Dashlane, “7 Password Hygiene Best Practices to Follow,” February 2023.
- Incode, “The Future of Biometrics Technology: An Overview by Industry,” December 2022.
- Dashlane, “2-factor authentication (2FA) in Dashlane,” 2023.
- Incognia, “What are the Key Differences between 2FA and MFA?” 2023.
- Dashlane, “What the Hack Is 2FA?” January 2020.
- Dashlane, “A Guide to Protecting Passwords from Hackers,” February 2023.
- Dashlane, “What Is the Dark Web?” March 2020
- Dashlane, “Why Dashlane Will Never Ask You for Credentials in an Email (Because That’s How Phishing Works),” November 2021.
- FTC.gov, “Data shows consumers reported losing nearly 88 billion in scams,” February 2023.
- Dashlane, “How to Protect Yourself From Identity Theft,” August 2023.
- Dashlane, “How to Mitigate BYOD Risks with a Password Manager,” May 2023.
- Dashlane, “What Is Data Privacy & Why Is It Important?” April 2023.
- Dashlane, “A Complete List of PCI Password Requirements for Businesses,” June 2023.
- Dashlane, “How Dashlane Makes 2FA Easy,” June 2022.
- Thales Group, “What Does OTP Mean,” 2023.
- Dashlane, “6 Pros & Cons of a Future Without Passwords,” July 2023.
- Dashlane, “How a Password Manager Helps Prevent a Data Breach,” December 2017.
- Dashlane, “Putting Security First: How Dashlane Protects Your Data,” January 2023.
- Dashlane, “Dark Web Monitoring: Your Employees Are Likely Using Compromised Passwords,” July 2022.
- Dashlane, “A Beginner’s Guide to Two-Factor Authentication,” August 2022.
Sign up to receive news and updates about Dashlane
