How to Protect Yourself From Identity Theft
Identity theft is a serious crime that can impact your credit, finances, and reputation. New cybersecurity tools and practices are constantly being developed to address this threat. Yet, the number of reported incidents continues to grow, and most adults don’t know what to do if their identity is stolen. No matter how well you’re currently protecting your passwords and personal information, there could be additional tools and tactics you can apply as you learn how to protect yourself from identity theft.
What is identity theft?
Identity theft is a crime involving personal or financial information stolen to commit fraud or complete unauthorized transactions. Identities can be compromised through the theft of physical items like mail, IDs, and documents, but more recent identity theft cases often involve technology and the internet.
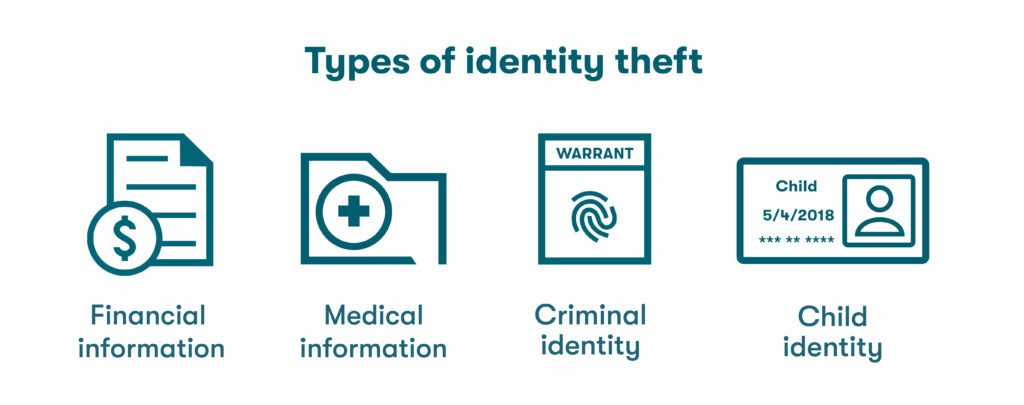
Types of identity theft
When people think about identity theft, they often think about new accounts, like credit cards or loans, opened in someone else’s name without their knowledge. Unfortunately, it can involve a lot more than that. The list of malicious activities has expanded as cybercriminals find new ways to exploit the backgrounds and reputations of unsuspecting citizens. Some of the more common types of identity theft include:
- Financial: The most common form of identity theft includes the use of someone else’s personal information for financial benefit. Fraudulent requests for credit are one example, but a criminal might also duplicate existing debit cards for their own use or withdraw small sums from a bank account over time, hoping to go undetected.
- Medical: This type of identity theft is more common in countries like the U.S. that don’t have universal healthcare. It occurs when someone poses as another person to obtain free medical care or prescription drugs. Unexplained healthcare charges and inaccurate medical records are among the consequences of this activity. The scammer might even apply for government-sponsored programs (like Medicaid in the U.S.) by using someone else’s name.
- Criminal: If you receive an unexplained court summons or traffic ticket, you may have been impacted by criminal identity theft. Identity thieves use stolen personal information to deceive authorities or avoid criminal prosecution, arrests, or fines. The fallout from these crimes can lead to failed background checks or even unfounded arrest warrants.
- Child: When employing this form of identity theft, the criminal steals personal information, including the name and government-issued ID of a child, to create a false identity of their own. In the U.S., children are targeted because they don’t typically have an existing credit history and are therefore less likely to be monitoring their credit.
Want to learn more about using a password manager?
Check out our personal plans or get started with a free trial.
How to recognize the signs of financial identity theft
Identity theft prevention begins with learning to recognize the common signs. Careful monitoring and attention to detail will help you notice issues associated with financial identity theft. These may include:
- Unusual financial transactions: Financial accounts are the most popular target for identity thieves. The internet and phone apps make it easy to check balances and transactions quickly. Periodically review each transaction in detail, no matter the dollar value, to ensure nothing looks unusual or suspicious.
- Credit score changes: In the U.S., an alarming sign of identity theft is a credit score that changes rapidly for no apparent reason. Regularly checking your credit can help you understand the factors driving your credit score and quickly recognize any new accounts that you didn’t open.
- Unfamiliar mail or email: Your home address and email account provide hackers with valuable clues to your identity, especially when email accounts loaded with personal information are breached or private mail is intercepted. Unusual messages, unexplained bills, or an absence of statements you typically receive can all be signs of interference by an identity thief.
- Tax issues: Tax fraud can be advantageous for scammers who use another person’s government ID number to illegally collect a tax refund. In the U.S., the IRS flagged more than one-million tax returns for potential identity theft during the 2023 tax season, with the associated refunds worth over $6 billion. When an impacted individual attempts to file a legitimate tax return later on, it might be rejected as a duplicate.
- Information found on the dark web: The dark web is the ominous corner of the internet where cybercriminals buy and sell digital contraband, including passwords, account information, and government ID numbers—all with complete anonymity. If a dark web scan reveals your personal information has been found, you may be vulnerable to (or have already experienced) identity theft.
Identity theft can be a pain, but keeping an eye on your data doesn’t have to be. Dark web monitoring scans for compromised passwords and sends real-time alerts if information is found. Learn more about the benefits of Dashlane’s Dark Web Monitoring.
How to protect against identity theft
Identity thieves rely on human nature and lax controls to illegally obtain personal information. Preventing identity theft is made easier by following these proactive tips and practices:
- Monitor or freeze your credit
Once you begin to receive bills or other correspondence related to new accounts you didn’t open, the damage is harder to undo. In the U.S., regularly reviewing your credit report helps you stay aware of any suspicious activities. As an extra precaution, you can freeze your credit to prevent any new accounts from being opened in your name. When you need to apply for credit, simply unfreeze your credit for a specified window of time.
- Be wary of phishing emails
Social engineering tactics are commonly used in identity theft scams to trick people into providing personal information under false pretenses. Phishing attacks can arrive as phone calls, text messages, or emails that appear to be from legitimate sources. These notifications direct us to provide personal information or contain links to harmful malware. Phishing scams can often be identified by poor spelling and grammar, contact info that doesn’t match the sending company’s website, or an unusual sense of urgency, but as scammers get more clever, these emails are getting harder to spot. When in doubt, use other means to validate the message, such as logging into the account through a browser or app or contacting customer support directly.

- Use antivirus software
Malicious software (malware) is any type of intrusive software that is intended to interfere with a computer’s function. Dangerous malware types like spyware and ransomware can be used to steal personal information or money. The best way to combat malware is by using antivirus software to quarantine and remove malicious files from your device. The relatively low cost of antivirus software pales in comparison to the potential financial and privacy loss from identity theft.
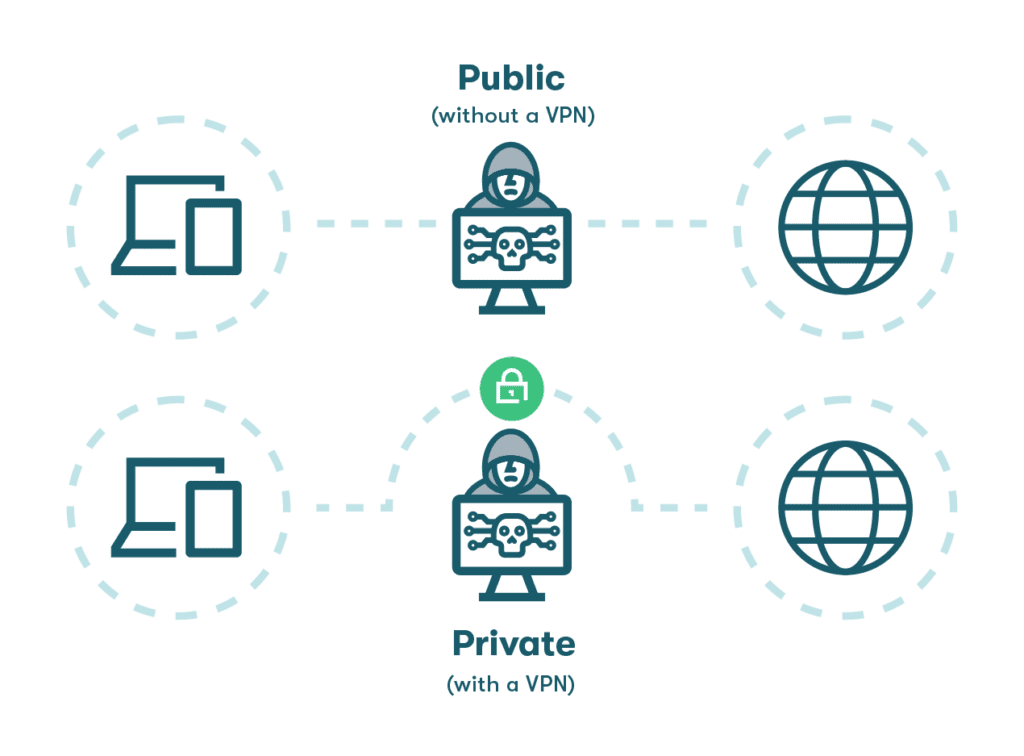
- Don’t use public WiFi without VPN
Public WiFi networks in places like airports, cafés, and hotels are susceptible to data intercept tactics, including network spoofing and man-in-the-middle (MITM) attacks. A virtual private network (VPN) protects your privacy, passwords, and identity by encrypting the data going into or out of your device and routing it through a secure portal. A VPN also masks your IP address so you can browse the internet privately.
- Monitor the dark web
Cybercriminals are likely to sell stolen information that can be used for identity theft on the internet, so scanning the dark web provides an added layer of protection. Dashlane’s Dark Web Monitoring tool continually scans the darkest recesses of the internet for your email address, passwords, and other personal information and notifies you if they are detected.
- Use strong passwords
Good password hygiene prevents cybercriminals from accessing your personal information. A strong password includes a random mix of uppercase letters, lowercase letters, numbers, and special characters, and it should be at least 12 characters long. Common phrases and identifying information like your name and address should always be left out. Password safety also means:
- You shouldn’t reuse passwords: Avoid reusing passwords since multiple accounts can be compromised if a reused password is stolen, making the potential impact more severe and harder to contain.
- You shouldn’t share passwords insecurely: Always use a secure portal to share passwords since unencrypted sharing methods like email, text messages, and Slack are more easily compromised and the information is stored indefinitely.

- You should use 2-factor or multifactor authentication
Push notifications and codes sent through an app or text to verify user identity are examples of 2-factor authentication (2FA). The few extra seconds required to log in are well worth it for the added identity protection. Multifactor authentication (MFA) uses two or more identifiers for the same purpose, sometimes including biometric factors like fingerprints or facial recognition.
- You should use a password manager
A password manager protects your identity by encrypting passwords and personal details, storing your information in a secure vault, and enabling 2FA for an additional layer of security. Automatic password generation and customizable autofill improve both security and convenience while eliminating the need to create and remember strong passwords for each account.
Dashlane also provides Dark Web Monitoring, a secure password sharing portal, and a Password Health score to track your weak, reused, and compromised passwords. The patented zero-knowledge architecture ensures no one (including Dashlane) can access your unencrypted information.
Should I pay for identity protection?
Paying for identity protection is an individual decision that depends on your budget, risk tolerance, and the perceived value of the services. For U.S. citizens, there are many free services available that automatically notify you when major changes to your credit score occur. While credit monitoring only covers one important aspect of identity protection, it spares you from continually scanning your own credit profile.
Fee-based identity protection plans vary in price depending on the extent and personalization of the services. High-end plans might include social media, dark web, and criminal database monitoring features that adapt to the latest cybersecurity trends and threats, as well as identity recovery insurance.
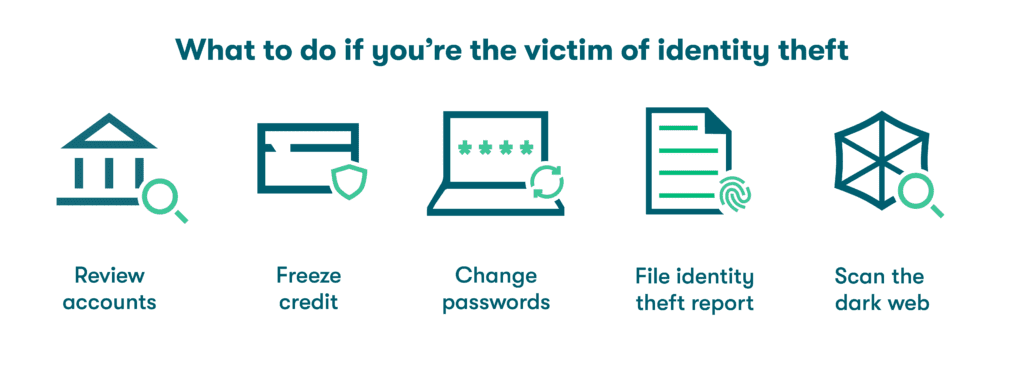
What to do if you’re the victim of identity theft
What is a valid response when identity theft occurs? Follow these important steps to help contain and minimize the impact:
- Review financial accounts. Look through your bank account and credit card transactions for purchases you didn’t make. Most credit card agencies have a standard process for disputing fraudulent charges. You can also contact each of your banking and credit vendors so they can be on the lookout for unusual or fraudulent activity.
- Freeze your credit. U.S. citizens can contact the three major credit reporting agencies to request fraud alerts against your credit profile. You can also freeze your credit to limit further activity until the situation is resolved.
- Change your passwords. Immediately change your passwords for impacted accounts if you're the victim of a data breach or identity theft. It’s also best to change your passwords if you’ve used an unsecured WiFi network without a VPN or shared passwords insecurely since these practices can open the door to cybercriminals. When updating passwords, use the password generator feature of a password manager to ensure your new passwords are strong and unique.
- File an identity theft report. File a report with the government agency responsible for identity theft. For example, in the U.S., you can file a report with the Federal Trade Commission (FTC) if you experience identity theft by visiting www.identitytheft.gov. This report creates a paper trail you can reference as you continue to rectify the situation. The FTC can also help you dispute charges you didn’t incur or set up a recovery plan.
- File a police report. Identity theft is a crime, and all crimes should be reported to the police. The police may not be able to catch the responsible cybercriminal or recover any money you’ve lost (especially if the criminal is overseas), but having the police report on file protects your good name if the thief commits further crimes while assuming your identity.
How Dashlane protects you from identity theft
Identity theft can have long-term consequences. To help protect against it, Dashlane maintains a laser focus on strengthening, encrypting, and safely storing your passwords. If your information is ever compromised, Dashlane also improves your awareness with tools like Dark Web Monitoring and a Password Health score. Further, if Dashlane were breached, the cybercriminals would not see your unencrypted data since our patented zero-knowledge architecture ensures that no one, including Dashlane, has access to your personal information.
Identity theft and data compromise can also be a big concern for businesses. The first step in protecting important business data is knowing if it has ever been compromised in a breach. Use our free online tool to find out if data connected to your business domain has been exposed.
References
- FTC.gov, “Data shows consumers reported losing nearly 88 billion in scams,” February 2023.
- AARP, “Money Can Be Stolen From Your Bank Account: Here’s How to Lower Your Risk,” October 2022.
- Identity IQ, “Criminal Identity Theft: What is it and How Does it Work?” August 2022.
- Aura, “10 Common Types of Financial Fraud & Schemes (With Examples),” January 2023.
- Dashlane, “5 Quick Tricks to Improve Your Online Security in 5 Minutes,” March 2020.
- Dashlane, “What To Do If a Scammer Has Access To Your Email Address,” April 2023.
- CNBC, “IRS flagged more than 1 million tax returns for identity fraud in 2023,” May 2023.
- Dashlane, “What Is the Dark Web?” March 2020.
- Lending Tree, “What is a Credit Freeze and How Is It Done?” November 2022.
- Dashlane, “What the Hack Is Phishing?” March 2020.
- Dashlane, “What the Hack Is Malware?” February 2020.
- Dashlane, “How to Prevent Ransomware Attacks on Your Devices,” March 2023.
- Security.org, “Do You Still Need Antivirus?” January 2023.
- Dashlane, “How Strong Is Your Password & Should You Change It?” August 2022.
- Dashlane, “How Password Reuse Leads to Cybersecurity Vulnerabilities,” May 2023.
- Dashlane, “7 Dangers of Sharing Passwords Without a Password Manager,” March 2023.
- Microsoft, “What is two-factor authentication,” 2023.
- Dashlane, “A Complete Guide to Multifactor Authentication,” November 2022.
- Dashlane, “Build the Case for a Password Manager in 8 Steps,” 2023.
- Dashlane, “Dark Web Monitoring: Your Employees Are Likely Using Compromised Passwords,” July 2022.
- Dashlane, “Understanding Your Dashlane Password Health Score,” October 2020.
- USA.gov, “Identity Theft,” April 2023.
- Dashlane, “How Often Should You Change Your Password for Online Accounts?” January 2023.
- Dashlane, “Resist hacks by using Dashlane's password generator tool,” 2023.
- Dashlane, “Putting Security First: How Dashlane Protects Your Data,” January 2023.
- Dashlane, “Dashlane's Security Principles & Architecture,” 2023.
- Dashlane, “Has your Business Been Breached?” 2023.
Sign up to receive news and updates about Dashlane
