What is Network Segmentation & How Does It Work?
With so many businesses relying on the internet, the cloud, and a mobile workforce, the traditional tools to protect network perimeters no longer suffice. Network segmentation has evolved to build secure walls around critical network assets. Let’s take a closer look at this innovative computing strategy’s diverse uses and benefits.
What is a segmented network?
Network segmentation is an architectural model that partitions a computer network into multiple segments or sub-networks that each function independently. The segmentation process also defines how traffic flows from one part of the network to another based on the network segmentation policy. The purpose of segmentation is to improve network performance and security.
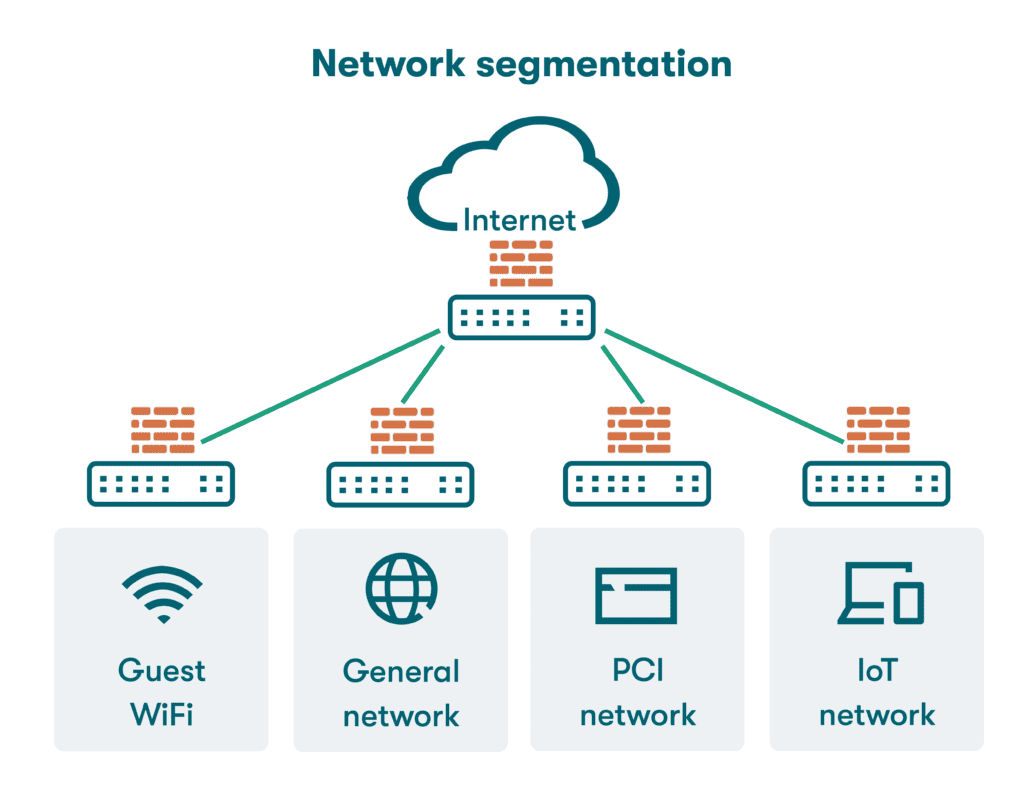
How does segmentation work?
Network segmentation practices began to take shape before the dawn of the internet, as firewalls and zone-based security practices were developed to protect networks from physical threats and unauthorized access. Cloud computing and virtual networks have made segmentation more challenging and complex, but many of the same basic principles still apply:
- Zero-trust strategies: A zero-trust security strategy is based on the assumption that no one (including machines) requesting access to a network or apps within it should be trusted—everyone must prove their identity and explain why they need access. A zero-trust strategy provides a foundation for segmentation by identifying assets within the network that require additional protection.
- Subdivided networks: Once critical resources and data have been defined and the ideal boundaries are designed, the process of creating multiple isolated network segments can begin. Using a virtual local area network (VLAN) to create a group of smaller networks connected to each other virtually or using subnets to divide the network based on IP addresses are two common approaches to network subdivision.
- Microperimeters: When network segmentation security is deployed, traditional definitions of inside or outside the network change. Microperimeters created through segmentation give individual apps or services their own dedicated perimeters. Security measures like authentication can be customized at this more granular level.
- Set access controls: Once the network is segmented, access controls for each area must be established so that the proper authentication process is followed when granting access and establishing policies for traffic flow. The principle of least privilege builds upon zero-trust strategies by only providing access to apps or devices when an individual needs them to perform their job.
Examples of network segmentation
Segmentation has become a common practice for companies seeking to fine-tune their security and data protection practices. Many segmentation examples are found in computing tasks and services that impact our daily routines, like those listed below.
- Guest WiFi. One familiar application of network segmentation is the guest WiFi services configured to provide WiFi to outsiders without allowing additional network access. This is accomplished by placing the guest WiFi on a separate subnet and creating a captive portal for authentication. Service industry companies frequently offer free public WiFi services to customers while keeping their in-house network invisible.
- Public cloud security. Cloud service providers host a wide variety of services and apps that belong to other organizations. Network segmentation controls allow these resources to be isolated for security purposes. Segmentation in the cloud also helps contain lateral movement by cybercriminals that could put other assets at risk. Cloud network segmentation requires automation to keep up with the dynamic provisioning of resources.
- PCI DSS compliance. Payment Card Industry Data Security Standards (PCI DSS) require merchants who manage credit card transactions to enact controls to protect consumers from data theft. PCI DSS compliance practices include network segmentation to provide a higher level of security for systems within the cardholder data environment (CDE). PCI DSS specifications also include comprehensive guidelines for password strength, storage, and protection.
- Demilitarized zones (DMZ). Despite the ominous name, a demilitarized zone (DMZ) is simply a public-facing sub-network set up to protect a company’s internal network from untrusted traffic. The resources in the DMZ, which might include email servers, web servers, and voice over internet protocol (VoIP), can be accessed through the internet, but the internal LAN can’t.
- Healthcare industry segmentation. The personally identifiable information (PII) in healthcare databases includes sensitive information such as social security numbers and medical record information that can be used to access services or obtain prescriptions illegally. Healthcare industry segmentation practices restrict access to apps and resources based on identity and deploy multifactor authentication to protect patient information.
- IoT device segmentation. The process known as Internet of Things (IoT) device segmentation categorizes IoT devices based on factors including their function, communication protocol, and security requirements to create logical groupings. Breaking IoT devices into these categories allows system administrators to apply the correct monitoring, access control, and security practices to each IoT sub-group.
Types of network segmentation
Network segmentation has expanded to include a wider variety of options. Commonly used segmentation strategies include:
- Physical segmentation: When a traditional physical segmentation strategy is employed, the network is broken into a collection of smaller subnetworks using hardware, with a firewall sometimes acting as the gateway to control traffic flows. In some cases, sensitive data is stored in a completely separate location to physically isolate valuable resources. Advanced planning helps ensure segments remain isolated while still communicating with one another.
- Logical segmentation: Logical segmentation is a popular option to divide the network into segments without adding additional hardware. With this approach, existing network infrastructure is used to create multiple VLANs connected to the same switch. A VLAN is a virtualized connection that joins multiple devices and network nodes from different LANs into one logical network.
- Perimeter-based segmentation: A perimeter-based approach to segmentation breaks the network into an internal and external segment based on trust factors. Like building a wall around a fortress, the internal segment is assumed to be safe from cyberattacks as long as the public-facing external network remains secure. This approach does not fully protect the network from insider threats or attacks that manage to breach the perimeter.
- Network virtualization: With the advent of the cloud, bring your own device (BYOD) policies, and a remote workforce, a traditional perimeter-based approach can fall short. Network virtualization enhances network segmentation benefits by assigning resources and security levels independent of the physical infrastructure. Virtualization technology uses software-defined networking (SDN) to allow each virtual network to function as a separate, isolated entity.
- Geographic segmentation: Network disaggregation allows data centers separated by thousands of miles to operate as a single entity. These long distances and built-in physical boundaries can also be used for segmentation. For example, a data center containing highly sensitive data may have additional security precautions yet still be connected to other less protected data centers in other locations.
- Microsegmentation: The practice of microsegmentation takes network segmentation to the next level by dividing the network into distinct security segments down to the workload or device level. This practice makes security practices more flexible within large data centers. Each service, app, or device can be configured with fine-tuned control over network access and traffic.
Network segmentation benefits
Segmentation has become an increasingly popular strategy based on a long list of benefits, including:
- Limiting data breach impact: In a flat, unsegmented network, hackers who gain unauthorized access can move freely throughout the entire network as they plunder valuable data or compromise sensitive files. Network segmentation limits the impact of data breaches by restricting the hackers’ movement to an isolated area.
—Protecting critical assets. The primary intent of network segmentation is to isolate critical systems from other areas of the network so secure perimeters can be established around these assets.
—Containing malware spread. Logical boundaries limit how far an attack can spread. For example, malware infections can be contained in one segment of the network before they impact more important applications and data. - Reducing network congestion: With the network divided into smaller segments, the traffic in each segment is reduced, so bottlenecks are minimized. Each segment can be allocated an appropriate amount of bandwidth to ensure critical servers and applications continue to operate smoothly.
- Improving compliance: By isolating sensitive data within designated areas of the network and limiting in-scope systems, segmentation controls make it easier to comply with regulations, including the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA), which mandate prevention of unauthorized access to consumer or patient information.
- Improving network monitoring: Segmentation simplifies network monitoring by allowing security teams to focus more resources and attention on critical segments. When security issues or performance problems are detected through monitoring, segmentation makes it easier to quickly identify and correct impacted systems before the issue spreads to other areas of the network.
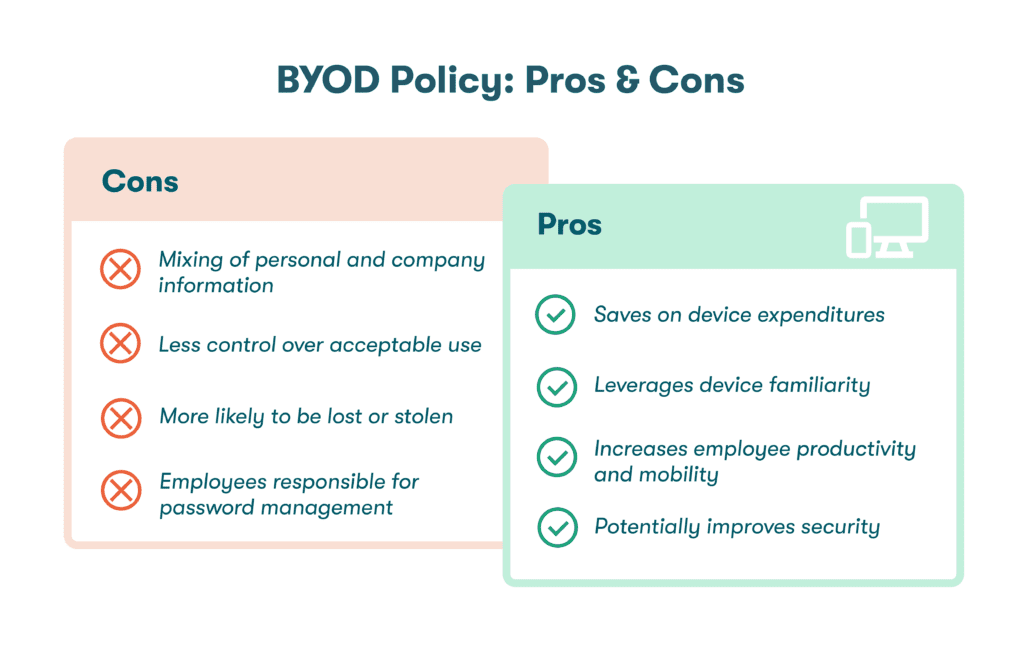
- Supporting BYOD: Network segmentation can be used to bolster the security of bring your own device (BYOD) practices by creating segments for employee-owned devices with predefined permissions and access levels. Along with employee training, 2-factor authentication (2FA), and the use of credential managers, segmentation helps mitigate the security risks associated with BYOD policies.
How to create a network segmentation policy
A network segmentation policy defines how the network is divided, the security protocols for each segment, and the access controls that define who can enter each area. Clearly defining the objectives of network segmentation and conducting a risk assessment to align security practices with asset value are important initial steps. This research and planning will help you select the right network segmentation architecture.
As part of a comprehensive cybersecurity strategy, Dashlane makes it easy for employees to create strong and complex passwords for all their work accounts and recall them automatically using customizable Autofill. Admins of Dashlane Business plans can also integrate Dashlane with any SAML 2.0 Identity Provider (IdP)—such as Azure, Okta, or Google Workspace—so employees can log in to Dashlane using their SSO credentials.
Dashlane’s secure, encrypted vaults for employee password storage ensure your organization’s data is always protected. Employees can use the intuitive Password Health score to improve their password hygiene, while Dark Web Monitoring scans the depths of the internet for their compromised credentials and alerts them with recommended actions to take if they’ve been impacted.
References
- TechTarget, “Network Segmentation,” March 2022.
- Dashlane, “Security Terms 101: What Zero-Knowledge Architecture, Encryption, and More Really Mean,” June 2023.
- Strongdm, “7 Network Segmentation Best Practices to Level-up Your Security,” March 2023.
- Search Guard, “What are Micro-perimeters in the Zero-Trusted Networks Approach?” 2023.
- Dashlane, “7 Business WiFi Security Best Practices To Protect Your Company,” June 2023.
- Tufin, “Cloud Network Segmentation: Mission Impossible?” February 2023.
- Dashlane, “A Complete List of PCI Password Requirements for Businesses,” June 2023.
- Dashlane, “6 Tips to Create Strong, Secure Passwords in a Digital World,” March 2023.
- eSecurity Planet, “What Is a DMZ Network? Definition, Architecture & Benefits,” April 2023.
- MedCity News, “How identity segmentation can reduce the attack surface for healthcare organizations,” June 2022.
- Dashlane, “A Complete Guide to Multifactor Authentication,” November 2022.
- Cloud-Fi, “How can IoT Network segmentation help set boundaries for a secure IoT framework?” February 2023.
- Uptycs, “Network Segmentation: Enhancing Security & Performance Through Segregated Networks,” May 2022.
- VMWare, “What is network segmentation?” 2023.
- VMWare, “What is Micro-Segmentation?” 2023.
- Dashlane, “A Business Guide to Data Breaches and Hacks,” 2023.
- Dashlane, “What the Hack Is Malware?” February 2020.
- GDPR, “Complete guide to GDPR compliance.”
- U.S. Department of Health and Human Services, “The HIPAA Privacy Rule,” 2021.
- Dashlane, “Why Security Teams Are Important,” November 2023.
- Dashlane, “How to Mitigate BYOD Risks with a Password Manager,” May 2023.
- Dashlane, “2-factor authentication (2FA) in Dashlane,” 2023.
- Dashlane, “Putting Security First: How Dashlane Protects Your Data,” January 2023.
- Dashlane, “Dark Web Monitoring: Your Employees Are Likely Using Compromised Passwords,” July 2022.
- Dashlane, “Dashlane's Security Principles & Architecture,” 2023.
Sign up to receive news and updates about Dashlane
