Password Psychology: How to Create Safe Passwords at Work
Ideally, our cybersecurity habits would always be based on data, best practices, and logic. However, sometimes our emotions and ingrained habits can take over. Let’s take a look at the impact of password psychology and learn how we can overcome it.
The psychology behind password creation
Industrial, forensic, and developmental psychology are familiar specialties for scientists and scholars studying human behavior. Password psychology extends many of the same principles to the cybersecurity field. Password security psychology is based on:
- Password personality types. Studies have shown that basic personality traits like openness, conscientiousness, and agreeableness directly influence password hygiene and behavior. For example, people who are considered conscientious tend to create stronger passwords, while people who are classified as agreeable or extroverted generally create weaker passwords. Attitudes and knowledge about password security can counteract some of the natural tendencies based on personality.
- Convenience vs. security. Another element of password security concerns human nature and our tendency to choose convenience over security. Without a password manager to assist you creating, memorizing, storing, and recalling strong passwords takes more time and effort. This plays into the hands of cybercriminals who prey on weak passwords that are easier to guess, especially with advanced hacking software.
- Developing password habits. Good password hygiene doesn’t happen overnight. Like other types of hygiene, password hygiene relies on best practices that are implemented over time to make sustainable improvements. Developing strong password habits can keep you from slipping back into dangerous patterns that undermine security.
Want to learn more about using a password manager for your business?
Check out Dashlane's business plans or get started with a free business trial.
Password management concerns for workers
Change and stress can influence our behavior in all walks of life. An evolving workplace and new technology continue to reshape our password habits. The top password concerns for workers include:
- Remote working: The ongoing trend towards remote working has introduced new challenges to password hygiene, including unsecured networks, unsafe password sharing, and lax policy enforcement, that can tilt the balance toward convenience over security. Written password policies and training that includes remote employees in the organization’s security culture are among the tactics companies can use to make remote working more secure.
- Bring your own device (BYOD): Policies that allow employees to use their own device for work bring improved flexibility and job satisfaction but can also blur the lines between business and personal use. Policies to control safe usage, 2-factor authentication (2FA), and a password manager can make BYOD more secure without undermining the benefits.

- Too many accounts: Today, the average person has as many as 240 password-protected accounts. This makes it more difficult to create strong and unique passwords for each one. Our password psychology comes into play when we create simpler passwords that are easier to remember or fool ourselves into believing that easy-to-recall phrases like our name or street name don’t threaten our security.
- Increased risk for hacking and scamming: Data breaches are becoming more common each year, and many common hacking tactics and scams rely on password security psychology as an inroad to our data and accounts. The long list of cybersecurity threats we need to defend ourselves against includes:
- Phishing: The social engineering tactic known as phishing is often presented in the form of an unsolicited email that attempts to trick you into opening a dangerous link or sharing private information. Bad spelling, poor grammar, and web addresses that don’t match the company are telltale signs of a phishing email.
- Man-in-the-middle attacks: Unsecured WiFi networks in places like airports and hotels have become havens for data-intercepting tactics like man-in-the-middle (MITM) attacks. The hacker will intercept communications directly or create a spoof hotspot to trick unknowing patrons onto an unsafe WiFi network. A VPN mitigates the risk of MITM attacks in public settings by encrypting all data going into or out of the device and routing it through a secure portal.
- Malware: A common objective of phishing and other cyberattacks is to infect your system with malicious software (malware) that impacts the function of your computer or device. While some malware strains are simply meant to annoy or inconvenience you, other varieties pose more serious financial and privacy threats. There are 2 common types of malware:
—Spyware: This form of malware installs itself onto your device and monitors your computing activity while relaying information to a hacker. This can put sensitive information like credit card and bank account numbers at risk. Since the function of your computer isn’t directly impacted, spyware can also be difficult to detect.
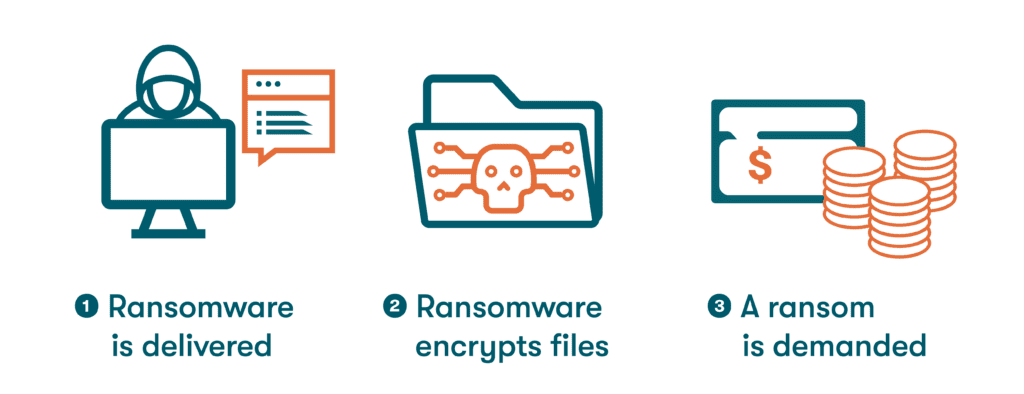
—Ransomware: This form of malware is usually targeted at businesses and can hold a device or network hostage until a ransom is paid in return for restored access to locked files. When businesses or individuals who experience a ransomware attack give in to fear and anxiety and pay off the cybercriminals, this often emboldens the hackers to seek out new targets and improve their methods.
Password security statistics
Recent statistics based on industry data and user surveys hint at the impact of password psychology on our behaviors and attitudes. Fear, complacency, and insecurity continue to drive password trends that should be based on best practices and risk mitigation.
- 91% of survey respondents stated they knew password reuse was dangerous, yet 66% of the group claimed they continue to reuse the same password or a slight variation of it.
- 79% of Americans share passwords, but only 13% are worried about identity theft.
- 61% of respondents say they are ready to transition to non-password login methods. This number climbs to 73% for users with multiple devices.
- 90% of internet users worry about being hacked. This statistic reflects a justifiable element of fear that can positively influence password habits.
- 61% of data breaches across all sectors involve compromised credentials.
“I believe that it’s not a question of if an organization will experience a data breach but rather when will it happen. We all have to be prepared.”
How to create safe passwords for work
The more you learn about password psychology, the more you’ll realize cybercriminals rely on human nature and poor password hygiene. Weak passwords open the door to common hacking tactics like brute force attacks that are rendered ineffective by strong password habits. Here are 5 ways to create safe passwords for work:
- Create unique passwords: A strong, unique, and random password should use at least 12 characters and include a mixture of uppercase letters, lowercase letters, numbers, and special characters. We must overcome the password psychology that leads us to add family names, pet names, or phone numbers to our passwords for the sake of memorization. These phrases don’t make our passwords unique or secure.
- Don’t reuse passwords: The password reuse habit can be hard to break, especially if you’ve been repeating the same password for years without knowing for sure which of your accounts are linked to the same password. A password manager that includes a password health score helps you eliminate this habit by tracking your weak, reused, and compromised passwords.
- Only share passwords securely: Passwords for social media accounts and digital tools are commonly shared among coworkers. This can become a security liability if someone in the group is impacted by a cybercrime since everyone who shares the stolen password will be vulnerable. Text messages, emails, and Slack messages aren’t secure sharing methods since the information isn’t encrypted, and the data can be stored indefinitely.
With Dashlane’s password-sharing feature, you can safely share passwords with other Dashlane users through a secure, encrypted portal that helps you eliminate unsafe password-sharing methods.
- Update passwords when necessary: Although there aren’t set rules for how often you should update your passwords, the 30/60/90-day mandatory password reset is no longer a best practice. However, you should always change passwords after you’ve been impacted by a data breach, if you’ve shared a password unsecurely, or when you’ve used a public WiFi network without a VPN.
- Use a password manager: A password manager for your team helps you improve your password habits and hygiene by offering password generation, an encrypted vault for secure password storage, and convenient autofill. By eliminating manual tasks and memorization, a password manager ensures that convenience and security go hand-in-hand.
How Dashlane improves your password psychology
As we begin to understand our own password personality types and entrenched password habits, using a password manager to address password challenges becomes a logical choice. With standard features like a Password Health score, 2FA, Dark Web Monitoring, and a secure VPN to protect you from unsafe websites and unsecured networks, Dashlane makes it easy to overcome the human psychology behind dangerous password habits.
In addition to its advanced security features and convenience, Dashlane Password Manager is surprisingly easy to set up and use. Learn the basics, along with some answers to frequently asked questions, in Dashlane Business: Employee Guide for Managing Passwords.
References
- Help Net Security, “Password psychology: People aren’t protecting themselves even though they know better,” May 2020.
- EAI, “Impact of Personality Types and Matching Messaging on Password Strength,” May 2021.
- Dashlane, “How Strong Is Your Password & Should You Change It?” August 2022.
- Dashlane, “7 Password Hygiene Best Practices to Follow,” February 2023.
- Dashlane, “How Password Reuse Leads to Cybersecurity Vulnerabilities,” May 2023.
- Dashlane, “How To Maintain Security When Employees Work Remotely,” October 2022.
- Dashlane, “How Businesses with a BYOD Policy Can Secure Employee Devices,” January 2022.
- Dashlane, “How Dashlane Makes 2FA Easy,” June 2022.
- Dashlane, “A look at Password Health Scores around the world in 2022,” 2022.
- Varonis, “89 Must-Know Data Breach Statistics [2022],” June 2022.
- Dashlane, “Why Dashlane Will Never Ask You for Credentials in an Email (Because That’s How Phishing Works),” November 2021.
- Microsoft, “Prevent malware infection,” February 2023.
- Dashlane, “What the Hack Is Malware?” February 2020.
- Dashlane, “How to Prevent Ransomware Attacks on Your Devices,” March 2023.
- NIST, “Man-in-the-middle attack (MITM),” 2023.
- Dashlane, “Why Do You Need a VPN? Don’t Miss These 3 Key Benefits,” December 2022.
- Threat Post, “ThreatList: People Know Reusing Passwords Is Dumb, But Still Do It,” May 2020.
- The Zebra, “79% of Americans Share Passwords, But Only 13% Are Worried About Identity Theft,” January 2023.
- Tech.co, “Report: Most People Are Comfortable Going Passwordless,” July 2022.
- Dataprot, “Save Your Data with These Empowering Password Statistics,” January 2023.
- Dashlane, “How a Password Manager Helps Prevent a Data Breach,” December 2017.
- Dashlane, “What the Hack is a Brute Force Attack?” February 2020.
- Dashlane, “Random on Purpose – Dashlane Commercial Fall 2020,” 2020.
- Dashlane, “Everything You Need to Know About Your Password Health Score,” October 2020.
- Dashlane, “Why Sharing Passwords on Slack is Dangerous,” November 2019.
- Dashlane, “Share your saved items in Dashlane,” 2023.
- Dashlane, “How Often Should You Change Your Password for Online Accounts?” January 2023.
- Dashlane, “Password Management 101,” 2023.
- Dashlane, “Dark Web Monitoring: Your Employees Are Likely Using Compromised Passwords,” July 2022.
- Dashlane, “Dashlane Business: Employee Guide for Managing Passwords,” 2023.
- Dashlane, “How to Create an Effective Password Policy for Your Organization.”
Sign up to receive news and updates about Dashlane
