
Phishing is the most common way attackers break into businesses, and AI is enabling smarter, more effective attacks.
At our recent webinar, Phishing Trends, Tactics, and Tools that Matter in 2025, Dashlane CPO Christophe Frenet explained how phishing is evolving and why traditional defenses fall short. He also answered questions from attendees, who ranged from non-technical employees to experienced security leaders.
Check out some insights from that event below, and watch the on-demand webinar for the full scoop.
How does AI make phishing attacks more effective?
AI-crafted phishing emails have an average click-through rate of 54%, compared to just 12% for all types of phishing emails.
Why are over half of people falling for AI phishing attacks? These attacks are more personalized and harder to detect. AI can scrape social media, websites, and public records to craft tailored messages that mimic real people—including executives—without the usual typos or clunky phrasing.
“Now, anyone can create hundreds of personalized phishing emails in seconds,” Christophe explains. “No technical skills required… Campaigns that once took days to plan and write can now be generated and launched instantly.”
By monitoring email threads, social media, and internal systems, AI can also time attacks for when targets are most vulnerable, like during travel or high-stress periods. It can even reference recent conversations to appear credible, testing and refining its phishing templates for higher success rates.
In addition, employees have learned to expect phishing attempts through email, but phishing has evolved beyond the inbox, often powered by AI.
“We’re seeing a rise in smishing attacks and vishing attacks—that is, phishing via text or voice,” Christophe explains. “Smishing attacks alone jumped 22% in [the third quarter] of 2024. One tap, one link, and you’re compromised.”
What does the average phishing attack cost a business?
Money: Phishing-related breaches cost organizations an average of $4.8 million in 2024. This includes direct losses like immediate response costs, legal fees, and regulatory fines, as well as indirect costs like system downtime and long-term remediation.
Time: A single phishing incident can trigger days or weeks of investigation, password resets, endpoint scans, and user communication. Core IT projects often get delayed while the team focuses on containment, then recovery. Worse, if the attack leads to malware installation, the cleanup effort can span multiple systems and departments. “[IT teams] get trapped in this never-ending cycle of playing catch-up,” says Christophe.
Productivity: Phishing also causes operational friction. Employees may be locked out of accounts, overwhelmed by urgent security alerts, or left confused about new policies rolled out in response to the breach. Productivity drops, and confidence in IT systems can erode, especially if communication isn’t clear or consistent during the response phase.
Reputation: A breach leads to difficult conversations with executives, customers, and even regulators, particularly if sensitive data was compromised. If gaps in security are exposed, your team may face increased scrutiny and budget pressure as well.
Why aren’t security training and phishing simulations more effective?
Even the best security awareness programs can’t fully prevent employees from falling for phishing attacks. As the saying goes, “It only takes one click to cause a breach.”
Beyond the increasing sophistication of the attacks themselves, there are several human factors at play:
Training fatigue: Let’s face it: Mandatory training is rarely popular. According to Dashlane’s 2025 State of Credential Security report, 22% of employees would rather be stuck in rush-hour traffic, 15% would give up a vacation day, and 11% would prefer a root canal over attending security training.
Fear: After realizing they’ve been phished, employees can feel embarrassed, especially if they received anti-phishing training. Some employees worry they’ll be judged, reprimanded, and even fired. This leads them to not report a successful phishing attack, allowing the incident to quietly escalate.
Mindset barriers: Many employees don’t view security as part of their role. They see it as IT’s responsibility, which means phishing awareness often takes a back seat to getting their work done.
For organizations, phishing is actually a systems problem, not an employee problem.
Employees shouldn’t be the last line of defense against threats. Instead, organizations need to build systems and provide tools that both support and protect employees while minimizing opportunities for error.
Why do antivirus and anti-malware software not detect phishing attacks?
Phishing attacks aren’t like traditional viruses or malware that install harmful code on your device. They’re social engineering tactics, meaning they manipulate human behavior.
Because there’s no malicious file to scan or quarantine, antivirus and anti-malware software often can’t detect phishing activity.
That’s why organizations need to protect themselves with layered defenses, like strong email filters, multifactor authentication, password managers with AI phishing alerts, and easy reporting channels.
If an employee gets phished, then uses Dashlane, will their passwords be compromised?
If an employee falls for a phishing attempt, it doesn’t automatically mean their Dashlane passwords are at risk.
Christophe explains, “The only way for your Dashlane vault to be compromised is if you entered your Master Password on a phishing website.” In most cases, clicking a bad link alone won’t expose anything stored in the vault.
To further reduce the chance of compromise, Dashlane was the first password manager to offer passwordless login options. Employees can unlock their vault using a trusted device with biometrics or a PIN—no Master Password required, and nothing for attackers to phish.
Soon, Dashlane will also offer security key access for businesses. With this method, the hardware key itself is the only way to unlock the vault, eliminating passwords and PINs altogether.
These options make it even harder for phishing attempts to succeed, while keeping employee credentials safe and accessible.
How can an organization proactively protect employees from phishing?
AI phishing alerts provide proactive, real-time phishing protection. Part of the Dashlane OmnixTM platform, these alerts use a proprietary AI model to analyze webpages in real time and detect phishing risks in less than 500 milliseconds.
If an employee lands on a suspicious site, Dashlane immediately issues an in-context alert in the browser—even if the employee isn’t logged into Dashlane. This prevents employees from accidentally handing over credentials to a fraudulent page that looks like a trusted login portal.
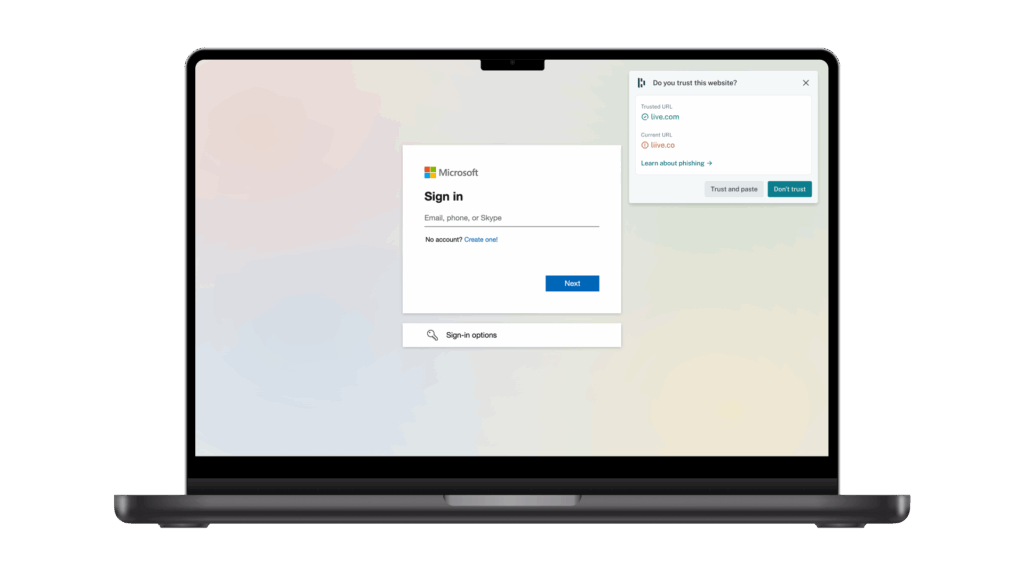
Thus, phishing attempts are stopped before an employee can give away their credentials, closing the gap between employee action and IT oversight. And security teams gain visibility into phishing activity across the company, helping them spot patterns, monitor threats, and respond quickly to emerging risks.
Instead of blaming employees when attacks get through, organizations can support them with platforms like Omnix that are designed to outsmart phishing attempts in real time.
Sign up to receive news and updates about Dashlane
Related articles






