A Complete Guide to Managing Technology Risk at the Enterprise Level
Safeguarding your organization from technological risks is an ongoing challenge. Whether you’re looking to identify, prevent, or combat these risks, this comprehensive guide covers everything you need to know about technology risk management to improve the safety, availability, and confidentiality of your systems and data.
What is technology risk?
Technology risk, or information technology risk, refers to the possibility of technology failures that can severely compromise business operations. This risk comes in many forms, such as information security breaches, cyberattacks, service outages, and unauthorized access to sensitive data like passwords.
Want to learn more about using a password manager for your business?
Check out Dashlane's business plans or get started with a free business trial.
Technology risk examples
Even though technology risks differ based on the industry and the type of infrastructure, some of the most common types include:
- Hacks. Hacking can be malicious (in the case of cybercrime) or non-malicious (for example, white-hat hackers who help test systems.) On the malicious side, hacking refers to a multitude of cybersecurity threats designed to gain unauthorized access, disrupt operations, steal sensitive information, or cause harm. Businesses frequently encounter these threats, particularly in the form of phishing and malware attacks.
—Phishing. This cyberattack relies on fraudulent messages, particularly emails, containing embedded links to trick individuals into revealing sensitive information like passwords or financial details.
—Malware. Short for ”malicious software,” malware refers to any type of software designed to harm or exploit computer systems or networks. Malware, such as computer viruses, causes harm by damaging programs or deleting files, while ransomware locks a user's computer or files until a ransom is paid. - Data breaches. Data breaches occur when confidential information is accessed or exposed to unauthorized individuals. External security threats such as hacking, malware, and phishing can expose sensitive data to outsiders. Disgruntled employees, former employees with a working company login, or those lacking proper training can also accidentally or purposefully contribute to data breaches.

- Personal devices. Personal devices often lack data encryption or get misplaced, making them highly susceptible to data loss or theft. Since IT teams have limited control over the security of personal devices, businesses must take the necessary steps to secure them by implementing password managers, antivirus software, and security patches.
- Unsecured Wi-Fi. Inadequate Wi-Fi security, remote access through unsecured servers, and connecting to spoofed Wi-Fi networks in public places increases the risk of unauthorized access and data theft. One way to prevent potential information exposure is to use a virtual private network (VPN).
- System failure. This technology risk arises when the tools, equipment, or systems supporting business operations encounter major disruptions or malfunctions. Such risks can result in an inability to perform crucial functions, as well as data loss, downtime, and significant financial and operational repercussions. It's important to have robust monitoring mechanisms, backup measures, and disaster recovery plans in place to minimize the impact of system failures and maintain uninterrupted operations.
- Third-party risks. Many organizations rely on external service providers or third-party software. If these partners lack strong internet security, your business may fall prey to data breaches or operational disruptions through them. You should review your provider agreements, as they may state that the provider is not liable for business interruption losses.
From big enterprises to recently funded startups, every business faces the ever-present threat of security breaches. Learn how Dashlane fortifies your defenses and protects against security threats.
Why is technology risk management important?
Despite several advancements in modern technology, various technology risks continue to impact workplaces. A technology risk management strategy can help effectively prepare and protect business data in the following ways:
- Identify and address potential technology risks before they occur
Outdated software in IT infrastructure can introduce compatibility issues and lead to bottlenecks, causing delays and prolonged system downtime. Regular technology risk assessments enable managers to quickly identify and address potential risks, ensuring smooth and uninterrupted operations.
- Monitor and protect data in real time
Real-time data and reliable statistics eliminate time delays, enabling prompt action in the event of a cyber incident. Utilizing the right tools streamlines the reporting process, making it easier to track and manage risks.
- Reduce costs associated with reputational and financial losses
Implementing a risk assessment schedule enables proactive identification and resolution of technological issues, preventing reputational damage and unnecessary recovery expenses. Businesses should also conduct timely assessments of IT systems, including personnel, investment, and IT infrastructure, to ensure efficient allocation and optimization of resources.
- Manage threats swiftly without losing business continuity
24/7 monitoring of IT systems is essential for uninterrupted business operations and preventing unnecessary stress for employees. A robust technology risk management strategy enables businesses to respond more swiftly to disruptions, minimizing downtime and ensuring business continuity.
- Gain trust from employees and clients
Creating a low-risk IT environment for employees fosters a strong working relationship, demonstrating a commitment to their security and well-being. Building trust with customers and stakeholders is essential, and risk management in technology provides reassurance that investments are protected even in emergencies.
5 steps to implement a technology risk management policy
A technology risk management policy includes a detailed step-by-step plan, starting from risk assessment to routine monitoring, to ensure your organization is a step ahead when combating technological risks. Implementing such a policy usually consists of the following steps:
- Conduct a technology risk assessment
Begin by evaluating your organization's digital infrastructure, systems, and processes to identify potential risks and vulnerabilities. This assessment involves conducting thorough audits, vulnerability scans, and analyses of existing controls to help you understand your business's specific technology risks.
- Develop a technology risk management policy
Next, create a comprehensive policy that outlines the objectives, principles, and guidelines for managing technology risks within your organization. This policy should address areas such as data security, incident response, access controls, employee training, and risk mitigation strategies. By clearly defining expectations and procedures, the policy ensures consistency and promotes a culture of security throughout the organization.
- Establish roles and responsibilities
Establish distinct roles and responsibilities for the individuals involved in the technology risk management process. Assigning specific responsibilities ensures that everyone understands their role in managing technology risks and can work together to mitigate potential threats effectively.
- Implement the framework
Now it's time to put your technology risk management framework into action and implement the necessary controls, procedures, and safeguards. This involves deploying security measures (like firewalls, encryption, and access controls) and establishing incident response protocols, employee awareness programs, and ongoing monitoring processes.
- Monitor progress and reassess
Keep an eye on your system logs, conduct periodic vulnerability assessments, and stay updated on emerging threats and industry best practices. By monitoring progress and reassessing risks, you can identify any new risks or changes in the technology landscape and make necessary adjustments to your risk management strategy to maintain robust protection.
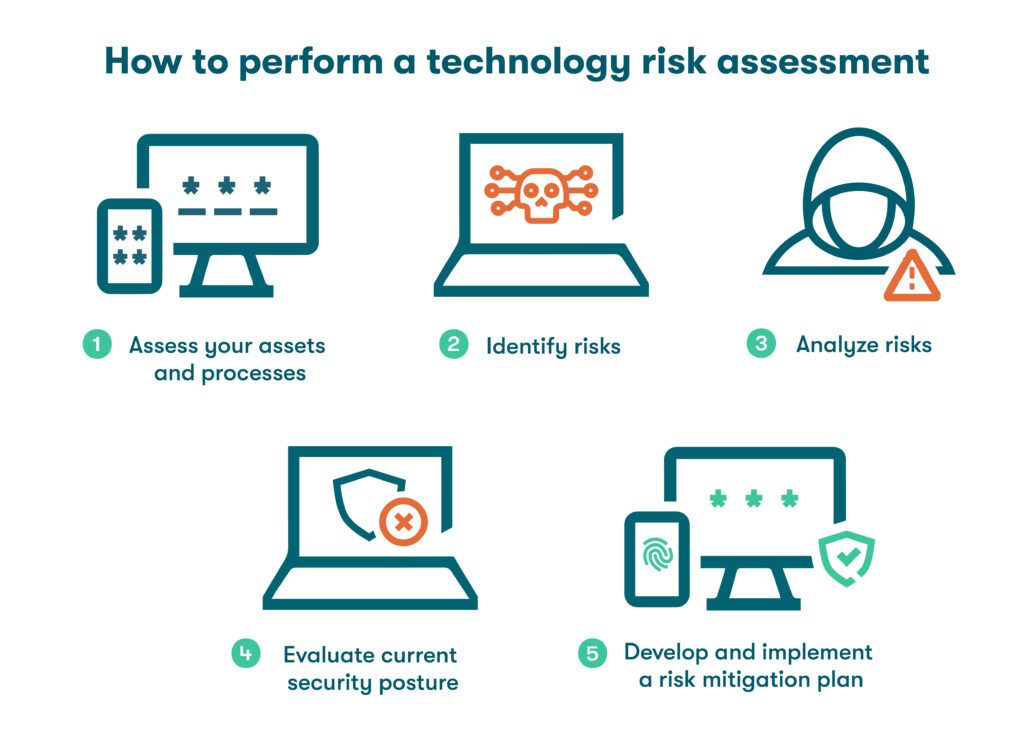
How to perform a technology risk assessment
As noted above, the first step in implementing an effective technology risk management policy is to perform a technology risk assessment or a security audit. Follow these steps to risk-assess your business:
- Assess your assets and processes
Identify valuable assets of the business, such as servers, client contact information, and trade secrets. Since it’s impossible to go through each and every asset, focus on those that are mission-critical by establishing criteria, such as monetary value and organizational importance.
- Identify risks
After prioritizing your assets, conduct a thorough examination to identify potential threats associated with each one. A threat refers to any factor that can cause harm to your organization. Be vigilant for signs of hardware failure and suspicious or malicious activities, such as data breaches, theft of sensitive information, and employee impersonation.
- Analyze risks
Thoroughly examine the identified risks to better understand their potential impact on your organization. Consider factors such as financial loss, operational disruption, reputational damage, and regulatory compliance. This analysis helps prioritize risks based on their severity and provides insights for effective risk mitigation strategies.
- Evaluate your current security posture
Assess your organization's existing security measures to identify strengths and weaknesses. Identify any gaps or areas for improvement that need to be addressed to enhance your overall security posture and reduce vulnerabilities.
- Develop and implement a risk mitigation plan
Based on the risk analysis and security evaluation, create a comprehensive plan outlining specific actions and measures to mitigate identified risks. Implement the risk mitigation plan systematically, allocate resources effectively, and regularly monitor and update it to adapt to evolving threats.
The challenges of manual technology risk assessments
When you follow the above steps to conduct a technology risk assessment, it’s essential to use modern tools to streamline the process, maintain accuracy, and avoid human error.
Ongoing technology-based assessments come equipped with automated data collection, analysis, and reporting tools. Manual workflows pose several challenges, some of which are:
- Inefficient data management. Carrying out assessments manually makes it challenging to organize and analyze data effectively, resulting in incomplete or fragmented risk assessments.
- Time-consuming process. Manual assessments require significant time and effort to gather and analyze data, leading to delays in identifying and addressing risks.
- Human error. Depending solely on manual processes increases the risk of human error, such as overlooking critical information or misinterpreting data.
- Lack of standardization. Manual assessments often lack standardized processes and criteria, making it challenging to compare and prioritize risks consistently.
Old technology must be removed and replaced with newer, more advanced tools.
Technology retirement vs. new technologies
Technology retirement refers to replacing outdated technology to keep your business running efficiently. By embracing modern technology solutions, organizations can enhance productivity, streamline operations, upgrade security systems, and assess technological risks more efficiently and accurately.
Problems of using outdated technology:
- Data security risks. Using outdated technologies exposes your business to increased data security risks. Outdated tech lacks updates and security measures, making it more vulnerable to hacks. This increases your risk of experiencing security breaches and unauthorized access.
- Less compatibility. Technology that has gone obsolete often lacks compatibility with modern systems and software, limiting your ability to collaborate and integrate safely and effectively with partners and clients.
- Potential data loss. The risk of potential data loss is higher with outdated technology, as it may lack reliable backup mechanisms or fail to handle data storage efficiently.
- Lower productivity. Older technology can lower productivity due to slow performance, frequent system crashes, and compatibility issues that hinder efficient workflows.
Benefits of using newer technology:
- Latest security features. Modern technology is loaded with advanced security features. Reliable password managers and endpoint security platforms like Cloudflare and Crowdstrike help protect your data, devices, and systems from evolving cyber threats.
- Enhanced flexibility. Upgraded technology improves compatibility with a wide range of systems and workflows, enabling seamless collaboration and data exchange.
- Remote work support. Newer technology is better equipped to handle challenges posed by remote work. It provides enhanced connectivity, cloud-based collaboration tools, and remote access capabilities without compromising security.
- Improved efficiency. Upgrading to newer technology improves efficiency by streamlining processes, automating tasks, and providing faster and more reliable performance.
- Competitive edge. With modern technology, you can leverage advanced tools and innovations to get a competitive edge and drive growth for your business.
Periodic technological risk assessments, coupled with comprehensive policies and modern IT systems, provide 360-degree defense against cybersecurity threats. While the initial process may take a bit of work, completing the assessment and getting proper systems in place will go a long way in helping to safeguard business operations.
Need help convincing management to invest in your organization’s IT security? Read our comprehensive guide to building the case for a password manager in 8 steps.
References
- RiskOptics, “What is Technology Risk?” June 2022.
- Netwrix, “Beginner’s Guide to IT Risk Management,” March 2023.
- Netwrix, “How to Perform IT Risk Assessment,” March 2023.
- AnyConnector, “What Is Technology Risk? How to Manage Business Threats,” March 2021.
- Thales, “2022 Thales Data Threat Report,” 2022.
- eSecurity Planet, “Automating Security Risk Assessments for Better Protection,” January 2021.
- Shi, “The importance of modernizing old technology — and how to do it,” April 2023.
- ERMA, “4 Types of Beneficial Risk Management Technology,” July 2022.
- Dashlane, “Why Do You Need a VPN? Don’t Miss These 3 Key Benefits,” December 2022.
- Dashlane, “How to Create a Culture of Security,” March 2022.
- Dashlane, “11 Cyber Threats To Be Aware of & Defend Against,” April 2023.
- Cobalt, “Cybersecurity Statistics for 2023,” December 2022.
- Dashlane, “How Businesses with a BYOD Policy Can Secure Employee Devices,” January 2023.
- Dashlane, “Putting Security First: How Dashlane Protects Your Data,” January 2023.
- Dashlane, “Are Password Managers Safe for Businesses?” January 2023.
- Dashlane, “How To Maintain Security When Employees Work Remotely,” October 2022.
Sign up to receive news and updates about Dashlane
