An Effective Cybersecurity Audit Should Be Able to Give You These Insights
Audits of all types are useful gap analysis and continuous improvement tools. This is especially true for cybersecurity audits that strengthen IT systems to improve protection from hacks, data breaches, and other security issues. Let’s take a closer look at the key components of a cybersecurity audit and the benefits and insights it can bring.
What is a cybersecurity audit?
A cybersecurity audit is an in-depth review of a company’s digital security assets, risk factors, policies, and preparedness for cyber threats. IT security auditing is performed by trained third parties or employees of the company with intimate knowledge of existing security tools and processes. Cybersecurity audits identify and address security weaknesses to maintain protection from cyberattacks.
Want to learn more about using a password manager for your business?
Check out Dashlane's password manager for small businesses or get started with a free business trial.
Insights your organization can gain from cybersecurity audits
Thoroughly examining your organization’s cybersecurity posture brings benefits and knowledge that are hard to obtain any other way. A cybersecurity audit provides valuable insight into:
- Vulnerability identification: When cybercriminals target a business, they look for weaknesses that will allow them to steal or compromise company assets. The most important insight gained from a cybersecurity audit is a complete understanding of the current cybersecurity threats and vulnerabilities presented by both external and internal factors.
- Compliance status: Cybersecurity standards, including the California Consumer Privacy Act (CCPA), Payment Card Industry Data Security Standard (PCI DSS), General Data Protection Regulation (GDPR), and Health Insurance Portability and Accountability Act (HIPAA), protect consumer information and privacy. Cybersecurity audits provide insight into how well an organization is complying with applicable standards.
- Policy effectiveness: A cybersecurity policy helps establish a security culture, outline data and asset protection requirements, and define the tools and practices needed to minimize risks. Despite these benefits, vague or poorly written security policies can lead to confusion that undermines cybersecurity. Auditing your organization’s cybersecurity policy helps you identify improvement opportunities.
- Third-party risks: Vendors, partners, contractors, and customers can all be privy to sensitive company data at various times. Unfortunately, these external parties don’t always maintain the same levels of cyber protection. Assessing third-party risks lets you determine if tighter controls or new systems are required.
- Disaster recovery readiness: Disasters aren’t limited to data breaches and natural occurrences like floods, fires, and earthquakes. Insider threats, cloud data center disruptions, and supply chain problems are among the issues that can suddenly threaten business security. An audit helps you review your company’s preparedness and contingency plans for any foreseeable disaster.
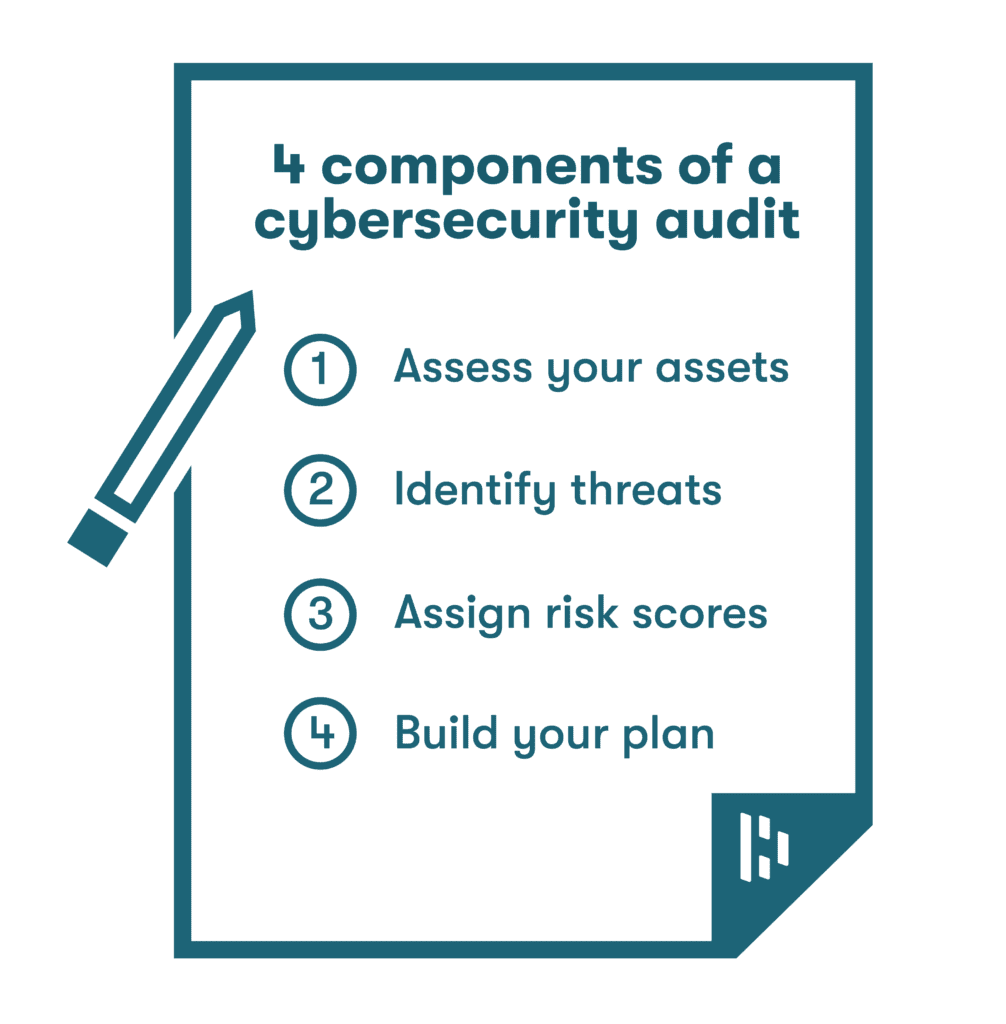
Key components of a cybersecurity audit
Many different cybersecurity audit strategies and options are available, but it can be difficult to know where to start. Taking these key actions will help you audit data security effectively for your organization:
- Assess your organization’s assets. It’s impossible to complete a comprehensive audit without a complete asset inventory. Assets include anything that contains cyber relevance, such as computers, servers, data, applications, and important internal documentation. While you may not have time to audit every asset, knowing exactly what you have helps you decide where to focus.
- Identify threats. Some common threats organizations experience include social engineering attacks (phishing), malware, poor password habits, and malicious insiders. Additional threats might stem from practices like bring your own device (BYOD) programs that take sensitive company information outside the workplace.
- Assign risk scores. Placing numeric values on the threats you’ve identified is essential because it allows you to prioritize actions and responses. The components of a risk score typically include the potential damage, the likelihood of occurrence, and the current cybersecurity defenses in place. Reviewing industry trends and compliance implications can help you develop more accurate scoring.
- Build your plan. The output of any information security audit should be a well-defined action plan. Depending on the audit results, the action plan might include immediate fixes like software upgrades and improved data backups, along with employee training to be rolled out later on.
Benefits of performing a cybersecurity audit
Well-planned and executed computer security audits provide insight into current performance while shedding more light on the steps needed to address emerging threats.
- Understand vulnerabilities: A cybersecurity audit can improve a company’s security posture over time by exposing vulnerabilities related to:
—Current cybersecurity controls: Are your current cybersecurity tools and practices sufficient to protect your assets? Penetration testing and white hat hacking can be used to put the system through its paces and identify issues.
—Current policies and processes: How complete and effective are your current cybersecurity policies? Are employees aware of the rules, guidelines, and reaction plans? Elements of the audit that review documentation effectiveness can identify human-based vulnerabilities. - Uncover inefficiencies: A proactive cybersecurity audit can improve operational efficiency by minimizing redundant or unnecessary security practices and ensuring incident response plans optimize resources. An effective audit decreases the number of security incidents and improves efficiency by curtailing time-consuming and expensive IT responses.
- Proactively improve policies: Organizations often only revisit or improve their cybersecurity policies after a cybersecurity incident demands a harder look at existing policies. Proactive auditing decreases hacking and data breach frequency by periodically revisiting and refreshing policies for practices like password management, which is a factor in over 80% of all data breaches.

- Demonstrate compliance: While you can use a cyber audit to assess organizational compliance to relevant standards, the audit results can also demonstrate compliance with these standards. Audit reports include risk assessments, corrective action plans, and management reviews that demonstrate a commitment to security during the certification process.
- Improve employee awareness and training: Assessing employee awareness of important security issues is equally as important as reviewing cyber tools and policies. Employees should be interviewed during the audit to identify weaknesses or gaps in their knowledge that can be addressed in the next training cycle as the security culture is reinforced.
Challenges and limitations of IT security auditing
While the steps that make up an effective cyber audit are well established, the industry landscape and threats constantly change. This creates challenges and limitations for auditors based on:
- Evolving threats: Artificial intelligence (AI), machine learning (ML), and automation allow hackers to develop new social engineering scams and malware strains faster and better. Audit strategies and risk assessments must be adapted yearly (or more frequently) to carefully consider these continually evolving threats.
- Complex network and security infrastructure: Network and security boundaries have expanded in recent years as cloud computing and remote working have become the norm. The diversity of devices and architecture has multiplied entry points for cybercriminals while making cybersecurity audits more complex.
- Changing regulatory requirements: Establishing and maintaining regulatory compliance are among the most important outputs of security auditing, so all businesses should be up to date on the latest cybersecurity regulations. Continually monitoring major cybersecurity laws and standards for revisions can be an effective way to keep audit practices in line with the latest guidelines.
- Resource constraints: IT security auditing requires a significant time and resource commitment that becomes challenging when IT resources are already stretched to the limit. Automated software tools to streamline audits and outsourcing audit responsibilities to third parties are two of the more popular strategies for overcoming these constraints.
How to prioritize cybersecurity audit findings
The risk-scoring method you establish will pay dividends when it comes time to assign actions and close out audit findings. The factors used to calculate the risk score quantify the significance of security gaps. Findings with the highest risk score should always be given top priority. A cybersecurity risk scorecard can also be a convenient way to convey high-level security status and progress to management.
In-house vs. outsourced cybersecurity audits
Who should perform the audit? Arguments can be made for both the in-house and outsourced approach to auditing.
- In-house audits:
—Pros: In-house audits are inexpensive for both small and large businesses, are less disruptive to internal workflows, and can establish a baseline for future audits.
—Cons: In-house audits can also have a steep learning curve for those performing cybersecurity audits for the first time and can suffer from bias when auditors review their own processes and results. - External audits:
—Pros: Using highly trained external auditors can be the appropriate choice for complex systems with many vulnerabilities. External audits typically minimize bias while ensuring compliance with legal requirements such as the Gramm-Leach-Bliley Act.
—Cons: External audits come with a higher price tag, require more coordination, and can disrupt office workflow.
How Dashlane supports cybersecurity auditing
Cybersecurity audits are just one important element of an overall cybersecurity strategy. Tools like credential managers simplify the auditing process by providing a convenient dashboard with a Password Health score to monitor weak, reused, and compromised credentials for individuals and the company overall. This heightened awareness minimizes risks from weak, reused, and compromised employee credentials that can lead to data breaches.
Dashlane also provides strong AES-256 encryption, 2-factor authentication (2FA), and a VPN to ensure secure web browsing for remote employees. Dark Web Monitoring scans the depths of the internet for your credentials and alerts you if they’ve been impacted by a data breach, while our patented zero-knowledge architecture ensures no one else (not even Dashlane) can access unencrypted employee data.
Completing a cybersecurity audit for your organization can feel daunting, but it doesn’t have to. Our useful mini-guide teaches you how to conduct a security audit in 5 steps.
References
- Dashlane, “11 Cyber Threats To Be Aware of & Defend Against,” April 2023.
- Dashlane, “A Complete List of PCI Password Requirements for Businesses,” June 2023.
- Dashlane, “Creating a Password Policy Your Employees Will Actually Follow,” July 2022.
- Venminder, “4 Best Practices to Reduce Third-Party Cybersecurity Risk,” December 2022.
- Dashlane, “How to Conduct Your Own Internal Security Audit,” June 2023.
- Noetic, “Defining Assets in Cybersecurity Asset Management,” July 2023.
- Dashlane, “Everything You Should Know About the Social Engineering Attack at Uber,” September 2022.
- Dashlane, “7 Password Hygiene Best Practices to Follow,” February 2023.
- Centraleyes, “What is Cyber Risk Score?” 2023.
- Dashlane, “Cybersecurity Strategy: Best Practices for Small-to Medium-Sized Businesses,” October 2022.
- Dashlane, “How Secure Are Your Cybersecurity Tools?” February 2021.
- Dashlane, “How to Create an Effective Password Policy for Your Organization,” 2023.
- OKTA, “3 Common Mistakes That Lead to a Security Breach,” February 2023.
- Dashlane, “10 New Cybersecurity Trends at Small Businesses,” July 2022.
- Dashlane, “A Guide To External Security Threats in 2023,” May 2023.
- BDO Digital, “Preparing for the Impact of New 2023 Cybersecurity Regulations,” May 2023.
- Huntsman, “Cyber security audit challenges in 2020,” January 2020.
- Federal Trade Commission, “Gramm-Leach-Bliley Act,” 2023.
- Dashlane, “A Global Look at Password Health Scores in 2023,” 2023.
- Dashlane, “How Dashlane Is Making 2FA Easier for IT Admins and Employees,” February 2023.
- Dashlane, “How to Conduct a Security Audit in Five Steps,” 2023.
Sign up to receive news and updates about Dashlane
