
They say imitation is the sincerest form of flattery. Clone phishing gives new meaning to this adage when cybercriminals replicate real professional and personal emails for malicious purposes, increasingly with the help of AI.
Let’s take a closer look at some clone phishing traits and prevention strategies.
What is clone phishing?
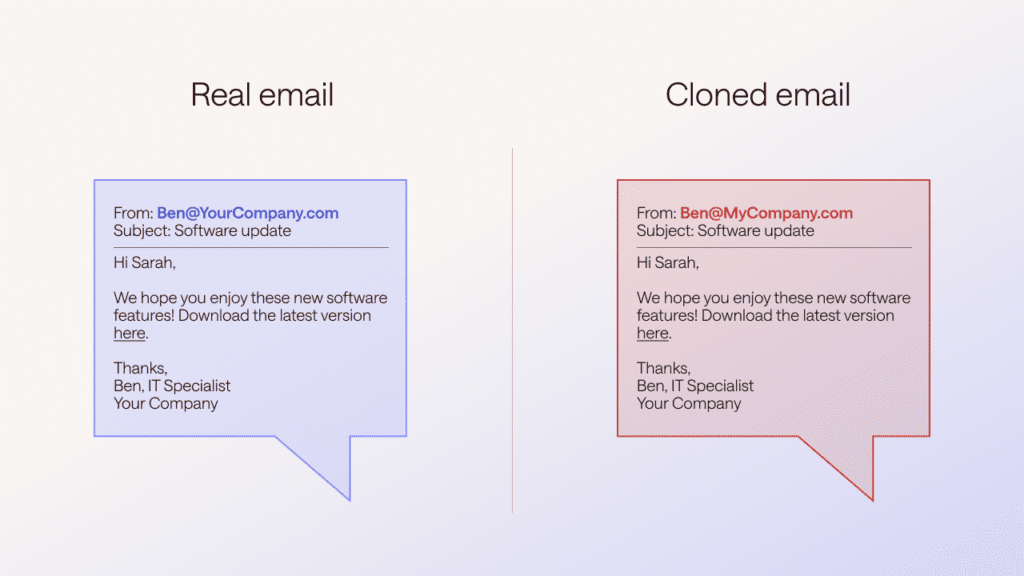
Phishing is a common social engineering tactic that uses emails appearing to be from a trusted sender to trick recipients into providing personal information or clicking on unsafe links. A clone phishing attack takes this method to the next level by using replicas of legitimate emails to heighten believability.
This attention to detail can make clone phishing emails difficult to spot.
Clone phishing vs. spear phishing
Spear phishing is a type of phishing attack that profiles specific targets. Hackers perform additional research to help them personalize message content. Whaling attacks take this a step further by targeting only high-level executives.
Clone phishing tactics can be used for both spear phishing and whaling attacks since copying an official email format helps convince the target that the email and sender are above board.
Clone phishing examples
Since clone phishing helps get malicious emails past our defenses, the attacks are becoming more common and diverse. Some dangerous clone phishing examples you may have already experienced include:
- Replicated bank emails: Using a realistic bank email format and signature as a template, hackers send emails appearing to be from your bank to get access to your financial account information or login credentials. A fake bank email might include a fake link to a refund or a request to update your credentials. Keep in mind that your bank will never ask you to disclose personal information or account numbers through email.
- Duplicate emails from IT: Hackers realize many email recipients are likely to trust any message from their IT department and follow the instructions they include, such as installing or updating software. A clone phishing attack might use an IT email that was previously sent to someone else as a model, and then add a link to a malicious website or malware in place of the original software link.
- Imitated emails from streaming services: Accounts like streaming services are so common that they make it easy for attackers to find examples of legitimate email messages, and then add their own malicious spin. One common tactic involves notifying a recipient that their payment method failed and asking them to re-enter their card or bank account information.
8 common traits of a clone phishing email
Clone phishing emails are dangerous because they’re harder to identify than a traditional phishing scam. Still, there are some common traits you can look for to bolster your security and lessen the impact of clone phishing:
- Suspicious email address: Look closely at the sender’s email address since this is one thing the hackers can’t clone. The presence of extra characters or missing characters can be red flags, so always research the sender or simply delete the message when in doubt. You can also contact the sender directly or compare the company’s actual website to the domain name in the sender’s email to see if there are any discrepancies.
- Spoofed hyperlinks: Hackers can use formatting or radio buttons to conceal the actual hyperlink address, so always hover over any link to review the full URL before you click on it, even if you believe the email is legitimate. A spoofed hyperlink might look very similar to the actual address, with only subtle changes, like 0’s in the place of O’s, that are easy to miss.
- Unexpected links or attachments: Most of the emails you receive from friends, coworkers, or businesses only include attachments in response to something you had requested or were otherwise aware of in advance. If you receive an email with a link or attachment you don’t need or weren’t expecting, it’s best to refrain from opening or downloading the file.
- Requests for sensitive information: A request for sensitive or personal information is a trait shared by all phishing email types. Most reputable companies will never ask you for information like credentials or account numbers in an email. Don’t reply or respond to questions in an email before you have verified the sender's legitimacy.
- Urgency and scare tactics: Phishing emails capture our attention by conveying an unusual sense of urgency, threatening dire consequences if we don’t respond, or presenting offers that sound too good to be true (and always are). All phishing emails use these strategies, including clone phishing emails.
- Generic salutations: Would someone attempting to reach you regarding an urgent matter begin their message by saying, “Dear Sir or Madam,” or simply “Hello”? Probably not. These generic greetings are often found in spam emails or shotgun marketing campaigns. If an email sender doesn’t know your name, they certainly shouldn’t be allowed to know anything else about you, so don’t respond.
- Odd grammar at times: Poor spelling and grammar used to be hallmarks of phishing emails. Cloned emails are less prone to these errors, since they’re copied from actual messages, but newly added sections might still have these flaws. Generative artificial intelligence (AI) tools are beginning to make it easier for cybercriminals to write phishing emails in a more professional tone.
- Unusual branding: By cloning an email, hackers will try to make the logo, background, font, and format look just like the real thing, but they sometimes come up short. If details like the logo size or color scheme seem off, it could be that the company has updated its branding, but it could also indicate a fake. Carefully review the URL and other information if the appearance of the email is inconsistent.
7 security tips for preventing clone phishing attacks
Advanced cybersecurity tools can minimize the cloning security risk. Social engineering tactics like phishing that rely on human nature and human error can also be prevented through ongoing training and awareness.
For businesses:
- Foster a culture of security: Companies can establish a culture of security by sharing objectives and statuses from the top down and helping each employee understand how their own actions impact the overall security posture of the company. A strong security culture can prevent clone phishing attacks by encouraging two-way communication with IT teams and timely reporting of suspicious emails.
- Create a cybersecurity training program: Training contributes to the security culture by teaching employees what to look for and how to respond to warning signs. Elusive hacking tactics like clone phishing are one reason why the global security awareness training market is growing by 15% each year.
- Run simulated phishing campaigns: Many companies are contracting white hat hackers and other phishing experts to develop simulated phishing campaigns. These long-term programs use realistic sample phishing emails sent to employees to test their judgment and awareness. If an employee mistakenly responds to a test phishing email, it becomes an opportunity to educate that employee on the danger signs they missed.
- Deploy email security tools: Email security tools, including firewalls and email security software, scan incoming messages and traffic based on pre-defined criteria. Many email services for businesses include configurable email filters that prevent phishing emails from reaching users. Antivirus and anti-malware software packages support these tools by identifying and eliminating malware that’s frequently spread through phishing attacks.
- Leverage AI phishing alerts: Dashlane’s AI-powered phishing alerts help organizations stop clone phishing attacks before employees enter their credentials. By detecting look-alike login pages and spoofed domains in real time, Dashlane warns users directly in their browser, reducing the risk of credential theft and preventing a common phishing tactic from turning into a breach.
For everyone:
- Use a credential manager: A credential manager lessens the impact of clone phishing by creating strong, complex passwords that are never stored or shared in an unencrypted format. If the phishing attack includes a spoofed URL, the best credential managers prevent you from unknowingly autofilling your credentials when the URL does not match the verified website address.
- Take advantage of Scam Protection: With Dashlane Scam Protection, you get real-time protection from phishing scams as you browse. The Dashlane browser extension uses proprietary AI to analyze 79 webpage signals and detect scams before you click or sign in—alerting you in the moment so you can avoid sharing personal information and keep your accounts safe.
- Keep software updated: Patch management and software updates help ensure system vulnerabilities are addressed quickly to reduce the effectiveness of phishing and other hacking tactics. Web browsers should also be kept up to date so features like certificate validation and pop-up blockers can most effectively minimize the impact of a phishing attack.
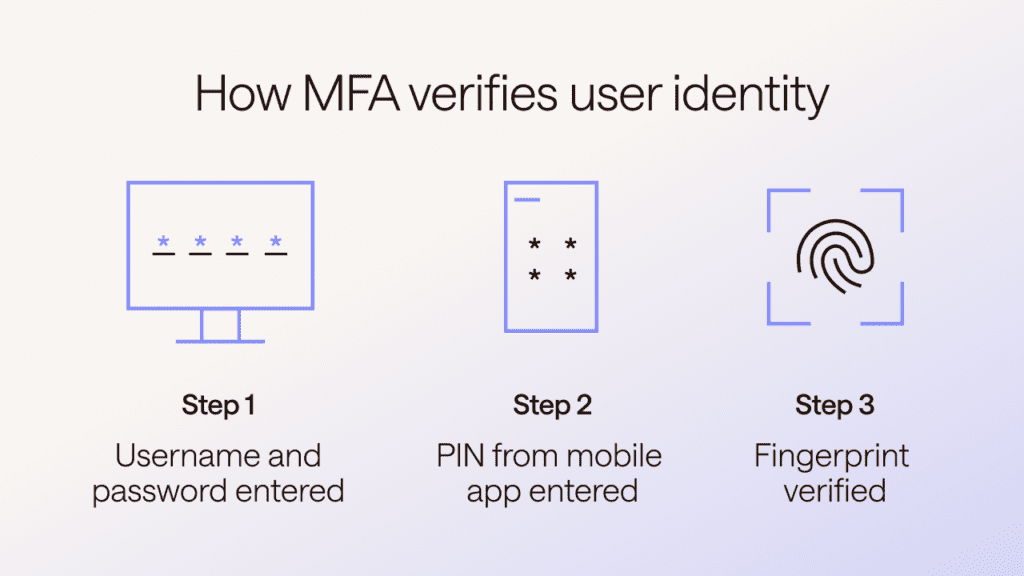
- Turn on multifactor authentication: Multifactor authentication (MFA) uses additional factors like codes sent through an app, fingerprint scans, or passkeys to verify user identity. Although MFA won’t stop a phishing email from reaching your inbox, the extra layers of security make it more difficult for hackers to access accounts if they manage to steal credentials through a clone phishing attack.
Outsmarting clone phishing
Attackers are using AI to create more convincing clone phishing messages at faster rates, scamming both individuals and businesses around the globe.
Smarter scams require smarter preventative measures. Dashlane offers leading password management built on zero-knowledge architecture, AI phishing alerts for businesses, and Scam Protection for individuals, keeping you protected and giving you peace of mind.
References
- Mimecast, “What is a whaling phishing attack?” 2023.
- Canadian Bankers Association, “Does this email look phishy? Check out examples of the latest scam emails,” July 2023.
- Dashlane, “Email Security Best Practices to Protect Your Business,” August 2023.
- Microsoft, “Protect yourself from phishing,” 2023.
- Dashlane, “Why Dashlane Will Never Ask You for Credentials in an Email (Because That’s How Phishing Works),” November 2021.
- Dashlane, “Strange Security: What to Know About Generative AI and Cybersecurity,” June 2023.
- Dashlane, “How to Create a Culture of Security,” March 2022.
- Cybercrime Magazine, “2023 Cybersecurity Almanac: 100 Facts, Figures, Predictions, And Statistics,” May 2023.
- Dashlane, “Interview With a Hacker: Rachel Tobac Tells You How to Defend Yourself From…Well, Her!” March 2021.
- NIST, “Phishing,” 2023.
- Dashlane, “These New Alerts Notify You When Something’s Phishy,” September 2023.
- Dashlane, “A Complete Guide to Multifactor Authentication,” October 2023.
- Dashlane, “What Is a Passkey and How Do Passkeys Work?” February 2024.
- Dashlane, “Putting Security First: How Dashlane Protects Your Data,” October 2023.
- Dashlane, “Essential Guide to Common Cybersecurity Terms,” 2023.
Sign up to receive news and updates about Dashlane
Related articles






