MFA for Shared Accounts: Eliminate Security Risks
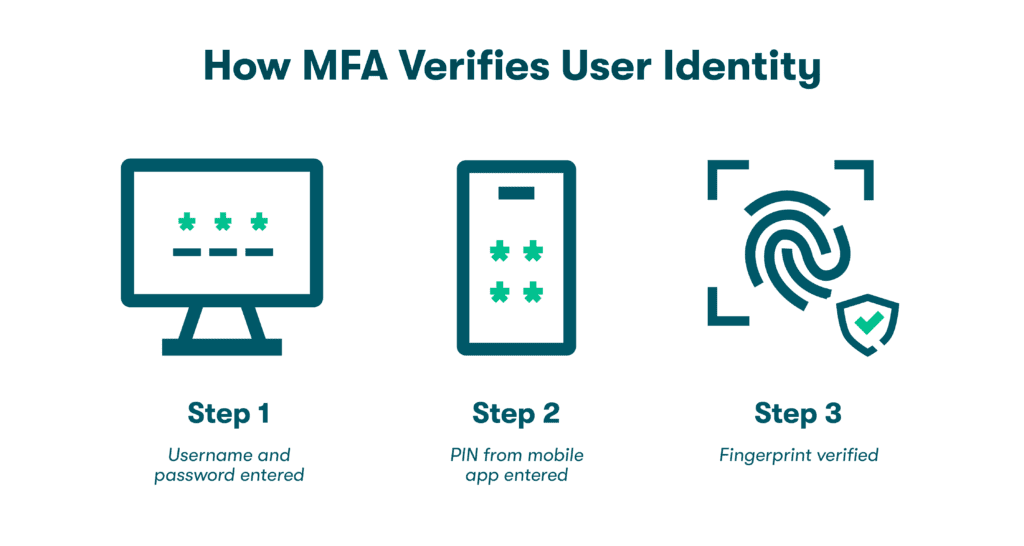
Multifactor authentication (MFA) is an online verification method that asks users to provide two or more identifiers, such as passwords, codes sent through an app, or fingerprints on their phones. This security measure makes it much more difficult for cybercriminals to gain unauthorized account access. Shared account MFA applies this valuable practice to safeguard accounts with two or more users.
A shared account is any online account or app that multiple credentialed users can access. Sharing accounts at work and home is common due to the cost savings and convenience it can bring. Account sharing is typically done in one of two ways.
- Individual app users with different credentials. Creating separate credentials for each account user has been a long-standing business practice because it guides workers to a common workspace while maintaining user traceability and accountability. Individual accounts where each user creates their own username and password include secure healthcare accounts governed by HIPAA regulations.
- Individual app users use the same credentials. This sharing model is frequently used in homes, with 79% of Americans admitting they share passwords. Retail and video streaming services that link to common banking information, as well as WiFi and email accounts, are some of the most common ones to share with family and friends. This introduces shared account password management challenges in the workplace since it can be difficult for IT teams to know who has been using a tool, app, or company card and whether that use was authorized.
Want to learn more about using a password manager for your business?
Check out Dashlane's business plans or get started with a free business trial.
What accounts are commonly shared?
The most commonly shared accounts are:
At work:
- Social media accounts: Social media accounts are usually shared so that multiple marketing people can post from the same company account and review analytics. Social media accounts’ direct link to brand reputation can also make password sharing risky for businesses if credentials aren’t properly monitored and controlled.
- Company credit cards: Rather than issuing individual credit cards to each employee, many organizations allow workers to share credit cards for low-dollar purchases to reduce paperwork and accounts payable transactions. Despite these benefits, sharing company credit cards increases security risks by increasing the chances of misuse or fraud, making transactions harder to trace, and creating a lack of ownership among those sharing the account.
- Shared digital tools: Employees once shared accounts by default for expensive apps with per-seat licenses, but cloud computing models have made it easier for each employee to enjoy untethered access to the tools and apps they need. Unique credentials and MFA for shared accounts give IT teams better insight into who has been using a shared tool at any given time and what transactions were made by a specific user.
At home:
- Retail accounts: Online retail accounts like Amazon are commonly shared by family members, so shopping carts, wish lists, and payment information can be located more easily. This type of sharing can be risky since logins provide direct access to multiple bank accounts and credit cards. You should change retail account passwords immediately if any account member is impacted by a data breach or finds their information on the dark web.
- Streaming services: Video streaming accounts are frequently shared so that the same logins can be used by family members in different locations, although streaming pioneer Netflix recently created a stir by announcing they would no longer allow accounts to be shared outside of a single residence. Either way, sharing an account means sharing a password, which comes with security risks.
- Financial accounts: Bank and credit card accounts also rank among the most commonly shared, especially between spouses and partners. This type of account sharing can create a dilemma when family dynamics change, and access for one or more parties must be revoked. Cognizant of these risks, many banks have been early adopters of mandatory 2-factor authentication (2FA).
Sharing passwords is safer with a password manager. Learn why in our comprehensive blog post.
The risks associated with account sharing
Many of the security risks we protect ourselves against as individuals can be multiplied by account sharing, especially when MFA or 2FA aren’t used to verify identity. These risks include:
- Greater chances of a hack: Hacking includes activities intended to exploit computer system weaknesses for personal gain. Many well-known hacking tactics use social engineering methods like phishing emails to lure recipients into sharing account numbers or credentials. The impact of these attacks can be multiplied many times over when others share this information. Two common types of tactics are:
- Brute-force attacks: Using brute-force tactics, the hacker deploys a computer algorithm to guess at account credentials until a match is found. If the matching credentials also happen to be reused for other accounts or shared with other users, it becomes more difficult to contain the damage.
- Credential stuffing: In a credential stuffing attack, hackers use previously stolen credentials to gain access to a large number of accounts. Like a brute-force attack, repetition and automation are the keys to success. These tactics can also impact multiple users if the stolen credentials are shared. MFA can prevent these tactics from succeeding since the stolen usernames and passwords alone won’t provide account access.
- Employees or users leaving: Shared accounts in the workplace can complicate onboarding and offboarding activities when IT teams are unsure of which account credentials have been shared. This can lead to unnecessary password resets and increase the risk of disgruntled or dishonest employees who leave the company with active credentials in hand and, in rare cases, misuse or sell them.
- Harder to manage: Shared accounts can be harder to manage both at home and in the workplace. Sharing access to tools that impact company finances, inventory, or communication without systems in place to ensure accountability can lead to confusion, especially during audits or investigations. To a lesser degree, shared accounts at home can lead to confusion and disputes over password changes, purchases, and order cancellations.
What to avoid when sharing accounts
Sharing accounts is almost unavoidable in some circumstances, so when you do need to share credentials and account access, avoid these common pitfalls:
- Unsecure sharing portals: The methods we use to share account access are just as important as the information contained in the accounts. Sharing passwords using unencrypted methods like text messages or emails leaves them vulnerable during a cyberattack. Collaboration platforms like Slack and WhatsApp should also be avoided since the unencrypted messages are often stored indefinitely.
Quality password managers include a secure password-sharing portal that allows you to transfer credentials safely. For example, the Dashlane sharing portal can be used to share Secure Notes or passwords with other Dashlane users. - Unclear cybersecurity policies: A cybersecurity policy is a good place to document workplace account-sharing expectations. The policy might also include guidelines for things like password manager use, data encryption, and shared MFA that reduce the risks of password sharing. While a strong cybersecurity policy can build a security culture and improve an organization’s security posture, a weak or unclear policy can have the opposite effect.
- Shared email accounts in the workplace: Email accounts might be shared in the workplace so that messages can be written by closely affiliated coworkers on the others’ behalf. During a data breach, this practice can expose multiple users’ account numbers, passwords, and other confidential data. Sharing email accounts with others also leads to privacy concerns when messages are read by someone other than the intended recipient. A collaborative shared group mailbox that doesn’t introduce security, privacy, or accountability concerns is a safer option.
- Weak passwords: The worst account passwords to share with others are weak passwords that are vulnerable to hacking and data breaches. Strong passwords should be at least 12 characters long and include a mixture of uppercase letters, lowercase letters, numbers, and special characters (when allowed). A secure password also leaves out words and phrases like your name, your pet’s name, or your street name that can be linked to your identity.

MFA is an effective way to minimize the risks from shared accounts. There are a growing number of strong authentication methods available that include:
- Authentication protocols: An authentication protocol is a set of rules used by IT departments to verify the identity of users. The protocol must list all the steps to complete the authentication process, and parties on both sides of the transaction must follow the same protocol. Application Programming Interfaces (APIs) are protocols used to complete the authentication process for many machine-to-machine transactions.
- PINs sent by text, app, or email: The most common 2FA and MFA methods send a numerical code to the user through email, text, or an app as an additional identifier to supplement their username and password. When accounts are intentionally shared, each user should have access to the specified email account or have their individual device phone number registered. Shared 2FA PINs are an excellent way to prevent unauthorized access as long as an intruder doesn’t gain access to the account holder’s email or phone.
- Fingerprints or facial recognition (biometrics): Biometric factors like facial recognition and retinal scans are part of a growing trend toward passwordless authentication. Although the earliest biometric methods weren’t 100% hackproof, biometric authentication is gaining popularity based on its portability and intrinsic individuality. It also frees users and IT teams from password creation, storage, and protection processes that can consume valuable time and resources.
- FIDO-based authentication: Since 2013, the Fast Identity Online (FIDO) Alliance has been working to develop new passwordless, phishing-resistant forms of authentication technology based on interoperability between device types. FIDO is currently working with Apple, Microsoft, and Google to develop new ways to use mobile devices as identification methods for laptop and desktop computers while storing private passkeys in the cloud.
What makes these solutions appropriate for shared accounts?
Each of these MFA methods addresses the primary weakness of shared accounts, which is the lack of individuality; when more than one person can access an account, it becomes even more important to positively identify them. Unlike passwords and usernames that can be lost or stolen and then used by an anonymous person, MFA methods are tied directly to some combination of the verified account holder’s knowledge, physical features, device, and location.
Sharing accounts is likely to continue. MFA is making it easier to ensure these accounts can be accessed by trusted relatives, friends, and coworkers, but not hackers. The ongoing advancement of authentication methods and password managers will help to safeguard these shared accounts in the future.
Password security is easier than you might think, but many companies wait too long to implement a solution. Discover the best practices for safeguarding sensitive business data.
References
- The HIPAA Journal, “HIPAA Password Sharing Policy,” 2023.
- The Zebra, “79% of Americans Share Passwords, But Only 13% Are Worried About Identity Theft,” January 2023.
- Dashlane, “Always Change Your Passwords After a Breach,” March 2020.
- Forbes, “Netflix’s Password Sharing Crackdown—And What Amazon Prime, Hulu, Others Are Doing—Explained,” February 2023.
- Dashlane, “5 Things to Know Before Sharing Passwords With Your Partner,” February 2021.
- Torpago, “Employees Sharing Corporate Credit Cards? Your company is at risk,” January 2023.
- Dashlane, “The Top 3 Reasons Businesses Get Hacked—and How to Avoid Them,” January 2021.
- Dashlane, “What Is Credential Stuffing,” September 2020.
- InformationWeek, “75% of Insider Cyber Attacks are the Work of Disgruntled Ex-Employees: Report,” July 2022.
- Dashlane, “Sharing Passwords Through Slack Is Risky,” November 2019.
- Dashlane, “Share your saved items in Dashlane,” 2023.
- Wagento, “The Major Security Risks of Having a Shared Email,” October 2021.
- Frontegg, “Authentication: Methods, Protocols, and Strategies,” February 2022.
- Dashlane, “What is Passwordless Authentication, and Why Should You Care?” November 2022.
- Dashlane, “Is a Passwordless Future on the Way? What You Should Know About FIDO-Based Authentication,” May 2022.
- Dashlane, “How to Safeguard Sensitive Data for Businesses,” 2023.
- Dashlane, “What Is a Passkey and How Does It Work?” November 2022.
- Dashlane, “6 Things a Safe Username Should Always Do,” February 2023.
- Dashlane, “A Complete Guide to Multifactor Authentication,” November 2022.
- Dashlane, “A Beginner’s Guide to Two-Factor Authentication,” August 2022.
- Dashlane, “How Much Time Does Your Company Spend Managing Passwords?” June 2022.
- Dashlane, “Creating a Password Policy Your Employees Will Actually Follow,” July 2022.
- Dashlane, “How to Create a Culture of Security,” March 2022.
- Dashlane, “How Strong Is Your Password & Should You Change It?” August 2022.
- Dashlane, “What Is Password Sharing & When Should I Use It,” February 2023.
Sign up to receive news and updates about Dashlane
