2026 Security Forecast: A CTO’s 5 Predictions About Passkeys, AI Threats, and More

As a CTO with over a decade in security, I've seen the industry evolve from perimeter defense to a complex, identity-driven landscape. My focus is always on where the next great risk and the necessary solution will emerge.
With 2026 on the horizon, I’m forecasting five key shifts related to the new threat paradigm and the mandatory security standards for enterprise survival.
And if you’re curious, check out the 2025 predictions made last year by Dashlane’s CEO, Director of Product Innovation, and myself. We got a lot of things right—no crystal ball needed.
#1: Passkeys make the leap to mainstream adoption
Based on 2025 momentum, I predict passkeys will finally reach the early majority in 2026.
Three catalysts will drive this transition:
- All major websites and platforms will support passkeys at scale
- Enterprise adoption will surge as organizations turn to passkeys to protect their weakest security link: Employee credentials
- FIDO Alliance's credential exchange standard will be increasingly relied on for seamless portability across providers
Expect to see major enterprise identity providers (Okta, Microsoft Entra) prioritizing passkey workflows. Fortune 500 companies will start announcing password elimination initiatives, with many consumer brands converting 20% or more of their user base to passkeys.
In addition, because passkeys eliminate the need for phishable, reusable passwords, credential-stuffing attacks will decrease for services with high passkey adoption. A prerequisite, however, is for online services to sunset password access so there’s no back door available when migrating to passkey authentication.
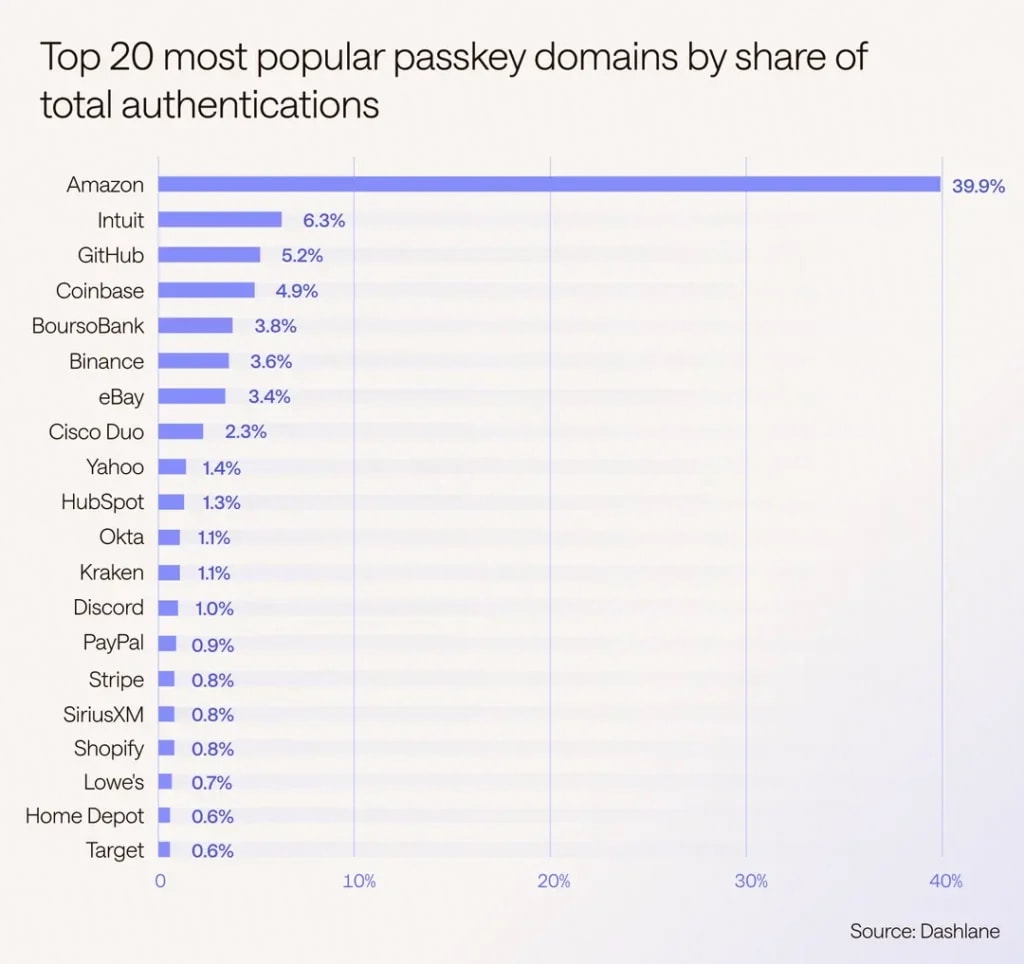
Wondering which services have high adoption? After analyzing millions of anonymized and aggregated web and mobile passkey authentications for our Passkey Power 20 report, Dashlane was recently able to identify the current most popular passkey domains. Here’s what we found:
#2: AI agents become the new attack surface (and security teams aren't ready)
As organizations increasingly deploy AI agents to handle tasks from customer service to code generation, I predict they’ll become threat actors’ favorite attack surface.
Unlike traditional apps, AI agents have broad access to data, can make decisions without human oversight, and operate across multiple systems simultaneously, making them both valuable and vulnerable—a losing combo.
The security industry has spent decades securing human identities. Now, we face a more complex challenge: Securing machines that act like humans but at machine speed and scale.
Most organizations don't have frameworks for authenticating AI agents, monitoring their behavior, or containing their access. Between shadow AI and the rush to MCP servers and immature AI flows, the risk is going to rise exponentially, with security teams badly equipped to protect organizations.
Critical security gaps to address:
- Zero-trust and zero-knowledge architectures extended to non-human identities
- Credential management for AI agents interacting with enterprise systems
- Agent monitoring to detect compromised or malicious AI agents
#3: The first major AI-powered breach hits with force
AI-powered cyberattacks are becoming the norm. Thus, I predict 2026 will feature the first significant security breach directly attributed to AI agents or AI-powered attack techniques.
Whether it's an autonomous AI system compromising enterprise infrastructure or AI agents leaking highly sensitive data at scale, this incident will force organizations to confront a new threat paradigm.
The breach will exploit the trust we've placed in AI systems themselves or demonstrate AI's ability to bypass defenses that stop human attackers.
What security teams can do:
- Be cautious of AI agents and AI system rollouts
- Reinforce solid security foundations and best practices, such as least privilege and short-term and reduced permissions
- Treat AI agents as privileged accounts requiring strict access controls and enforce the least privilege principle even more rigorously
- Implement authentication mechanisms specifically designed for non-human identities
- Develop incident response playbooks for AI-driven attack scenarios
#4: Browser-native security becomes the new enterprise perimeter
In 2026, I predict the collapse of the traditional network perimeter to accelerate, with browser-based security controls replacing it as the primary enforcement point. With work happening across SaaS apps, personal devices, and distributed teams, the browser will emerge as the consistent layer where security needs to be enforced.
Organizations are realizing that protecting credentials at the browser level is more effective than trying to secure every endpoint or network. Browser extensions and browser-native security capabilities offer real-time protection against phishing, credential theft, and unauthorized access, precisely where attacks happen.
Expect to see:
- Security teams prioritizing browser-based credential protection over traditional endpoint solutions
- Browsers adding more built-in security capabilities to protect against evolving threats
#5: Zero-knowledge architecture transitions from differentiator to requirement
What once distinguished security-conscious vendors will become table stakes. As data breaches expose the limitations of trust-based security models, I predict enterprises will start demanding zero-knowledge architecture, a security framework that ensures only users have knowledge and access to their data.
This is now possible with confidential computing and cloud secure enclave technologies.
Customer and regulator expectations are converging. Organizations can no longer justify having access to data they don't need to see. Zero-knowledge isn't just better security—it's better business, reducing liability and building customer trust.
Adoption drivers:
- Compliance frameworks explicitly requiring data minimization and zero-knowledge approaches
- Enterprises make zero-knowledge a vendor selection criterion
The fundamental takeaway for 2026 is clear: The era of perimeter-based security is over. The new battleground is identity, and the only way to survive the coming wave of AI-driven threats is to adopt the most secure, data-centric architectures available.
From the mainstream adoption of passkeys to the mandate for zero-knowledge, the security industry is moving toward a single, critical standard—a future where no one, not even your service provider, has access to data they don't need.
The organizations that embrace these five seismic shifts today will be the ones positioned not just to survive, but to define the secure enterprise of tomorrow.
Sign up to receive news and updates about Dashlane





