What a Secure System Is & How to Implement It in Your Business
Secure systems can benefit both large and small businesses. By employing a variety of strategies to protect a company from cyberattacks, a secure system is the first and strongest line of defense against cybercriminals.
What is a secure system?
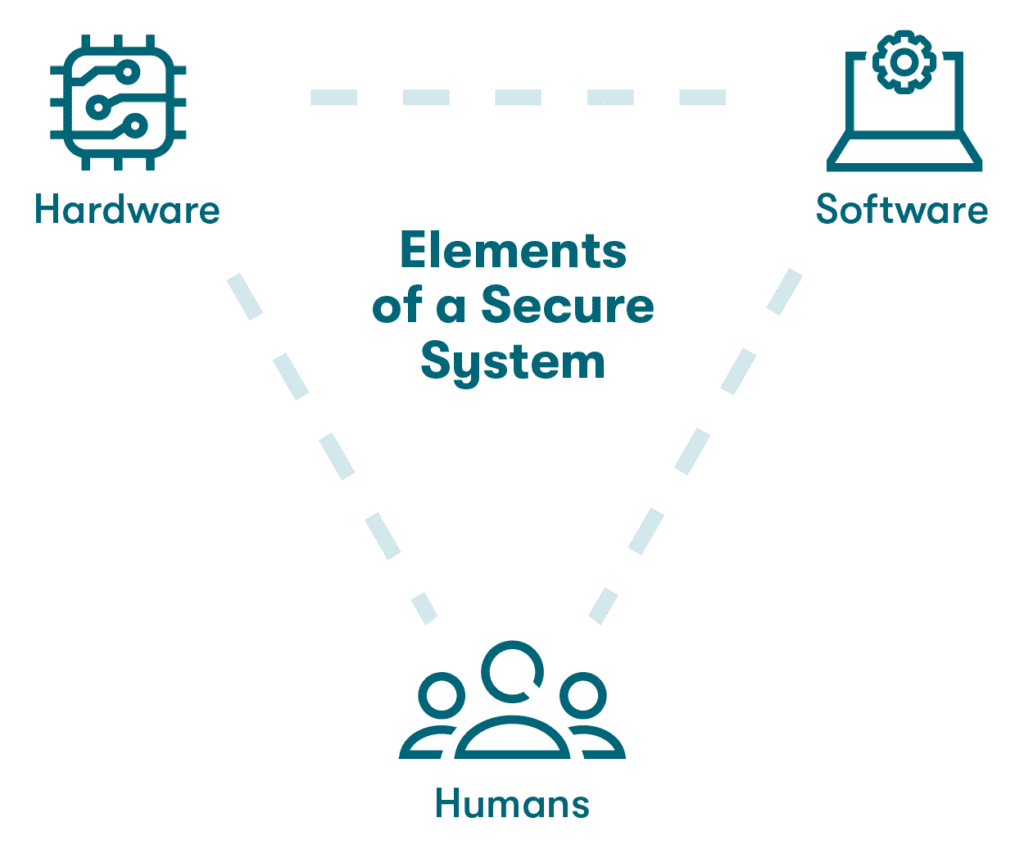
A secure system is the backbone of a company’s cybersecurity policy. A secure system is made up of three moving parts—hardware, software, and humans—that work together to keep company data safe from cyberattacks and data breaches. When a system is secure, the business becomes stronger and more resilient as a result. Let’s review the three elements of a secure system:
- Hardware
Employer-provided laptops or mobile devices tend to fit more easily into a company’s secure system than employee-provided ones. When employees use personal devices to access professional accounts, those devices need to become part of that secure system, too.
- Software
When it comes to secure systems, software is where most of the magic happens. Software works in concert with the hardware to protect the system from data breaches or cyberattacks. For example, anti-phishing or antivirus software protects against cybercriminals who are interested in company data. Protected accounts, such as Zoom, Gmail, or other widely used company accounts, are also examples of software that plays a role in a secure system. Other supporting software, such as SSO technology, 2-factor authentication, and password managers, protects against cyberattacks.
- Humans
No matter how far we’ve come in the digital age, humans are still essential to secure systems. They’re the final piece of the puzzle that ties the hardware and software together, bringing the system as a whole to life. They download the software and decide when, where, and how to use the hardware. They also create and execute strategies to keep the system safe. A company’s cybersecurity is only as good as its cybersecurity culture, which includes every employee in your cybersecurity plan.
83% of organizations say they’ve suffered more than one data breach.
Want to learn more about using a password manager for your business?
Check out Dashlane's password manager for small businesses or get started with a free business trial.
How to secure your company system
When evaluating your company’s cybersecurity, you may realize that there are areas for improvement. To strengthen your system, you’ll need to analyze the hardware, software, and humans that make that system run. Use these steps to figure out how to boost your system’s security.
- Examine your system
To improve your system, you need to know where your company’s cybersecurity currently stands. Take stock of the hardware that employees use (whether mandated or not), the software your company uses, and the organization’s security culture. Are your employees generally aware of how to spot phishing or spoofing attempts? Do they use VPNs when working remotely, or is it more of an internet free-for-all? Knowing these factors will help you identify weaknesses and possible entry points for cybercriminals.
- Develop an IT security plan
Using the information you’ve gathered from doing a thorough system assessment, it’s time to develop an IT security plan to boost the strength of your cybersecurity program. Use the findings from your initial evaluations to target areas for improvement and set realistic goals with realistic time frames. Measure progress over time with occasional reporting and updates.
Remember how humans are an essential part of the system? Well, a successful IT security plan requires that every employee gets involved in some way. This could be through cybersecurity training, signing a written version of the cybersecurity policy, or upper management expressing support for the plan. Because every person in an organization plays a role—from always using a VPN to reporting potential breaches—sharing accountability can help emphasize the importance of this plan.
On that note, don’t be afraid to utilize cybersecurity professionals. They’ll be able to identify and resolve any weak spots you may have missed and share insights on which tools are worth the cost.
- Use the right tools to secure your data
In addition to educating employees about the proper use of company hardware and software, you’ll need supporting tools to make your system as secure as possible. Often, these tools are the software component of the system and can include platforms such as:
What are the risks of an unsecured system?
At its best, a system works flawlessly to protect against cyberattacks and keep company data safe. At its worst, a system is unsecured, a data breach occurs, and there are serious implications for data and privacy. But what exactly are the risks of an unsecured system and lost or stolen data?
Financial loss
Data breaches can be difficult to recover from, especially in the cases of small- to medium-sized businesses. For example, researchers found that small businesses that made $100,000 incurred an average security incident cost of $24,000, which is nearly a quarter of those businesses’ annual earnings. Larger companies with billions of dollars in revenue can much more easily sustain costs associated with data breaches, which amounted to less than 0.1% of annual revenue in the study. Financial loss can be a serious threat to businesses that don’t realize the value of a secure IT system until it’s too late.
Time loss
The time it takes to clean up a data breach can be substantial. The company must identify the breach, run an investigation to determine what went wrong, recover lost data, and overhaul all employee passwords. Factoring in the time it takes to communicate with customers and regain trust as well, a data breach is more than just a loss to the company—it can waste months of employee time and productivity.
Reputational damage
A 2021 Centrify study found that 65% of data breach victims lost trust in a company as a result of a data breach. Once a data breach happens, the most difficult aspect of cleaning up the mess is regaining the trust of the employees and customers who lost data in the incident. This could take months to years, as customers may begin doing business with competitors as a result of the damaged reputation your business has suffered.
“Our strongest tools are our reputation and relationships. A breach could do more than take our security; it could remove the trust from our name that we’ve worked so hard to build.”
Principal, Vice President, JD+A
How password managers can support a business’s IT security
Ultimately, stolen passwords and data breaches will damage a business’s bottom line. But there are affordable tools that can help companies maintain their cybersecurity. Password managers can be a one-stop shop for businesses wanting to make their systems more secure. After all, 61% of data breaches across all sectors involve compromised credentials.
How does a password manager work?
Password managers are vaults that store and autofill an employee’s information when they need it, whether they’re signing up for a new account or logging into an old account. They also generate strong passwords and show which existing passwords are weak or reused. Password managers only require that users remember their “master password” to access all of their stored passwords, making them a powerful tool that supports efficiency and cybersecurity simultaneously.
What makes password managers incredibly secure is a process called encryption. Encryption is an extra step that password managers and other cybersecurity software, such as VPNs, take to ensure data remains safe. Encryption scrambles the password into a different set of letters, numbers, and symbols before storing it in the password vault. Dashlane employs a “zero-knowledge” architecture, which means that even password manager employees are unable to unscramble the vault’s encryption.
Password manager features
A great password manager will go above and beyond their core password vault to provide additional safety features. Dashlane offers features such as:
- Analytics and password health monitoring: This feature can be helpful for IT managers who want to track their progress toward secure IT system goals.
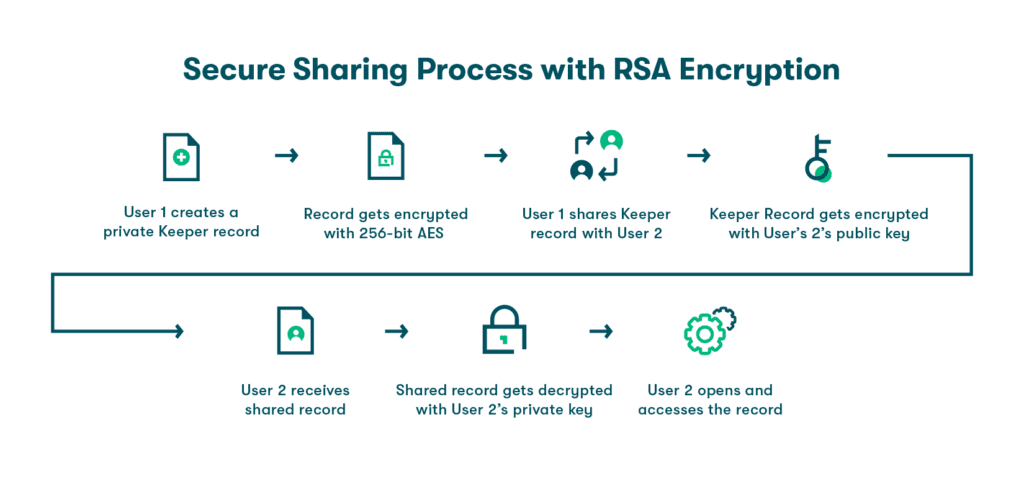
- Secure password sharing: This feature helps employees share passwords for shared accounts over a secure platform, as opposed to chat or email. On top of this, password managers like Dashlane can automatically update the passwords for shared accounts, so if one employee updates a password for a shared subscription, every other employee will automatically have access to the latest password.
- 2-factor authentication: This provides an extra layer of security by requiring that anyone trying to access an employee account verifies their identity.
- Single sign-on integration: This feature is a huge time-saver for employees, who only need to use one set of login credentials to access multiple platforms.
- 24/7 customer support and a password recovery process: Not every password manager offers this level of support for basic customers, so make sure to select a plan that includes this level of access.
Learn how to take your small business’s system and password security to the next level with Dashlane’s Password Playbook.
References
- U.S. Small Business Administration, “Strengthen Your Cybersecurity”
- Federal Trade Commission, “Cybersecurity for Small Business”
- Cybercrime Magazine, “60 Percent Of Small Companies Close Within 6 Months Of Being Hacked,” 2019
Sign up to receive news and updates about Dashlane
Thanks! You're subscribed. Be on the lookout for updates straight to your inbox.
