It’s not just hype—hackers are real, and so is the need for hacker protection. Trends like remote work, an ever-increasing list of accounts, and new AI tools provide new and fertile ground for cybercriminals to explore. Luckily, a few basic tools and best practices can make protection against hackers easier.
What is a computer hacker?
In general, a hacker is a computer expert who uses their skills to steal data or interfere with computer systems. Although the stereotype of the lone hacker in a hoodie persists, many hackers are part of organized teams, which makes their tactics more effective and hack protection more difficult.
- Bad actors and cybercriminals. Hackers are sometimes referred to as bad actors (not to be confused with the Hollywood variety), threat actors, or cybercriminals. Each of these terms describes individuals or organizations that are attempting to exploit computer system weaknesses for their own benefit.
- White hat hackers. Some hackers are on our side. White hat hackers use their skills and experience to identify security vulnerabilities, but for a different reason: companies hire them to attempt unauthorized access in a controlled fashion. The company then corrects the weaknesses that the white hat hacker finds to provide protection from hackers with more sinister intentions.
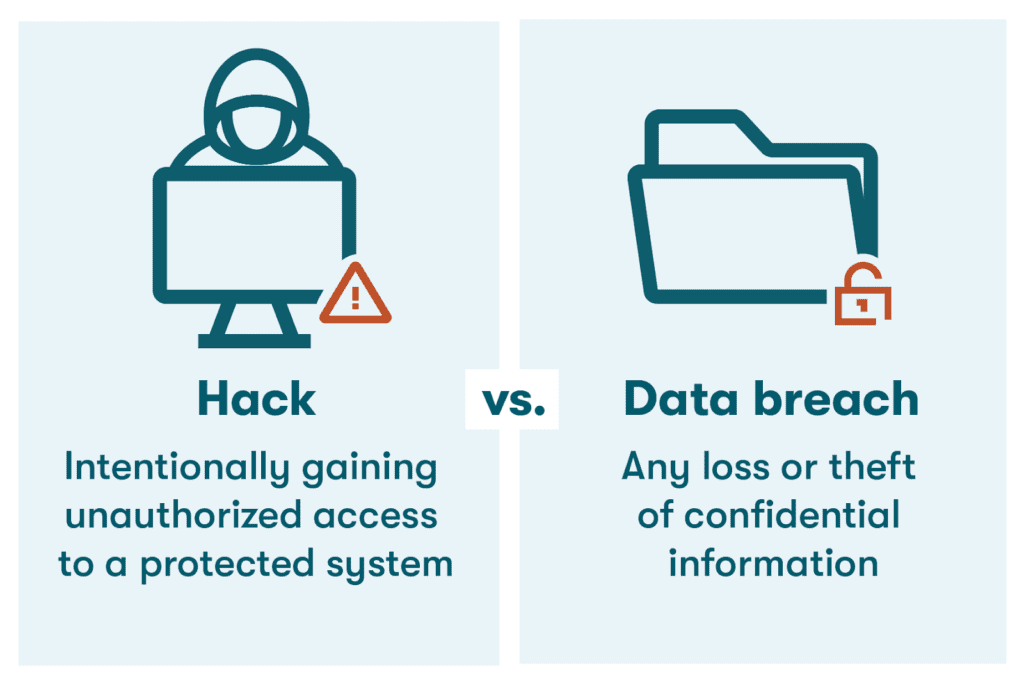
- Hacking vs. data breaches. Although the terms hacking and data breach are sometimes used interchangeably, they are two different but often related things. While a hack is an intentional act to gain unauthorized access to a protected system, a data breach is any loss or theft of confidential information. This can be the result of a hack, but it can also be due to negligence or human error.
Want to learn more about using Dashlane Password Manager at home or at work?
Check out our personal password manager plans or get started with a free business trial.
Different types of hacks to avoid
To learn how to protect yourself and your computer from hackers and viruses, you need to understand some common hacks you're likely to encounter at home or at work. These are just a few of the tactics you need to watch out for:
- Phishing: A phishing attack, usually in the form of an email or text message, uses social engineering methods to trick an unsuspecting recipient into sharing things like passwords and bank account numbers. Some phishing emails also include unsafe links or attachments. Poor spelling, bad grammar, and URLs that don’t match the company website are warning signs that help you identify phishing emails.
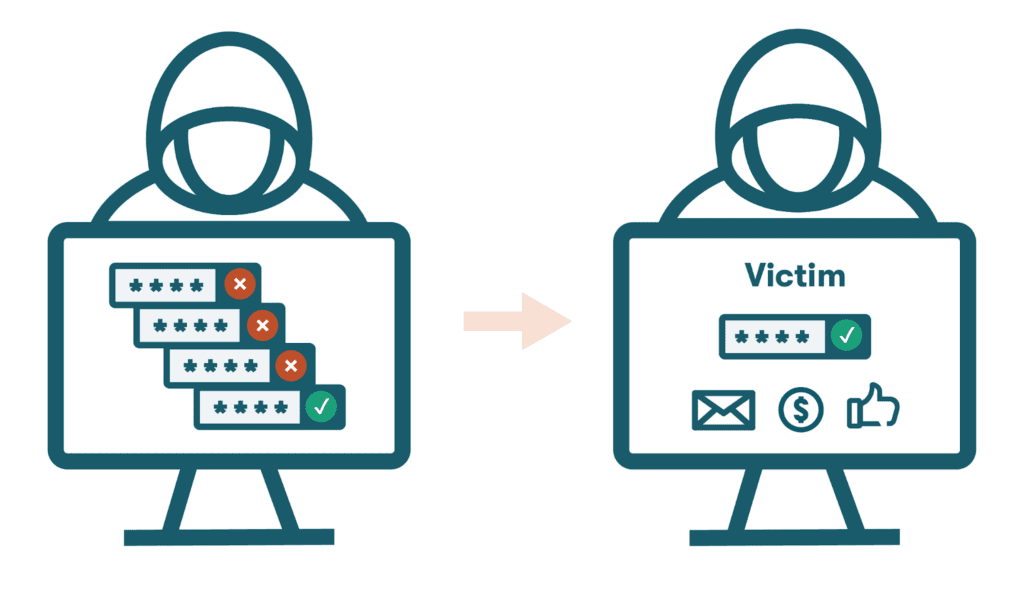
- Brute-force attacks: This sophisticated hacking tactic uses artificial intelligence (AI) and automation to create and input combinations of usernames and passwords (logins) over and over until an account is accessed. Reusing passwords can make the impact of a brute-force attack worse since one match might unlock many accounts. Long and complex passwords also help to reduce the chances that this hacking tactic will impact you.
- DDoS attacks: Distributed denial of service (DDoS) attacks also use automation, but the intent is to shut down a website rather than steal information. DDoS attacks are usually directed at businesses and attempt to overwhelm the website with traffic until it’s rendered non-functional. A coordinated DDoS attack with traffic originating from many different sources can be difficult to block.
- Port-out scams: This type of hack is used to transfer your phone number to another service provider without your knowledge, then use the phone number to access your other accounts through the 2-factor authentication (2FA) process. You can protect yourself from port-out scams by being careful who you share your phone number with and using authentication methods that don’t require your phone number, like apps and physical security keys.
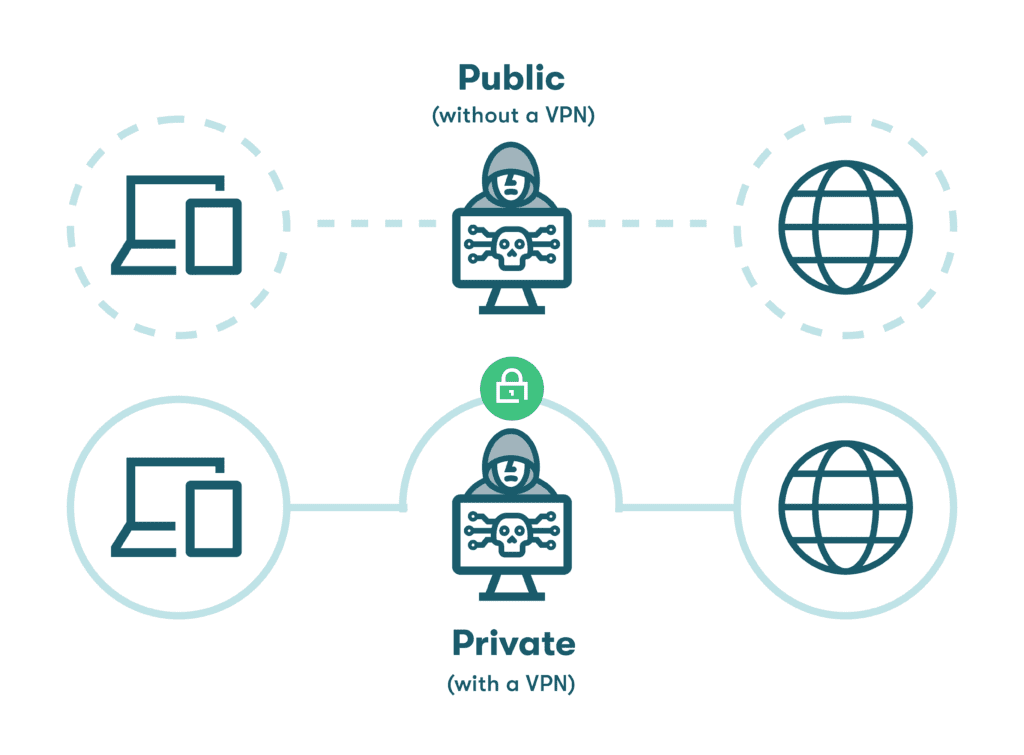
- Man-in-the-middle attacks: Using this tactic, the attacker positions themself between two parties to intercept data traveling between them. The hacker might also redirect people to fake websites to steal their information. MITM attacks are often attempted in areas with unsecured WiFi connections, like airports, cafés, and hotels. A VPN reduces the threat of MITM attacks by encrypting all data going into or out of a device and routing it through a secure portal.
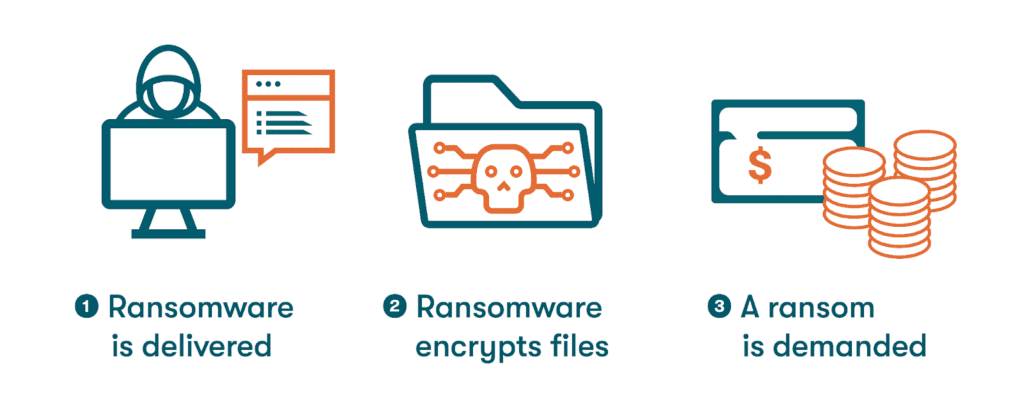
- Malware: Short for malicious software, malware includes several types of software that are intended to interfere with a computer’s function. Slow computer performance, unexplained pop-ups, and unusual browser or security settings changes are warning signs of a malware attack. The growing list of malware variants includes adware, viruses, and worms, as well as some especially effective varieties designed to steal data or render a device unusable, including:
8 tips for securing your online accounts against hackers
As you learn how to avoid hackers, you’ll begin to discover some reliable tools and practices that protect you from cyberattacks. These 8 tips will help you keep your devices and personal information private and secure:
- Use a firewall
Firewalls filter all incoming and outgoing traffic and prevent suspicious data from passing based on a set of predefined security rules. Firewalls can be hardware, software, or cloud-based and can be programmed to filter traffic based on known threats and the level of security required.
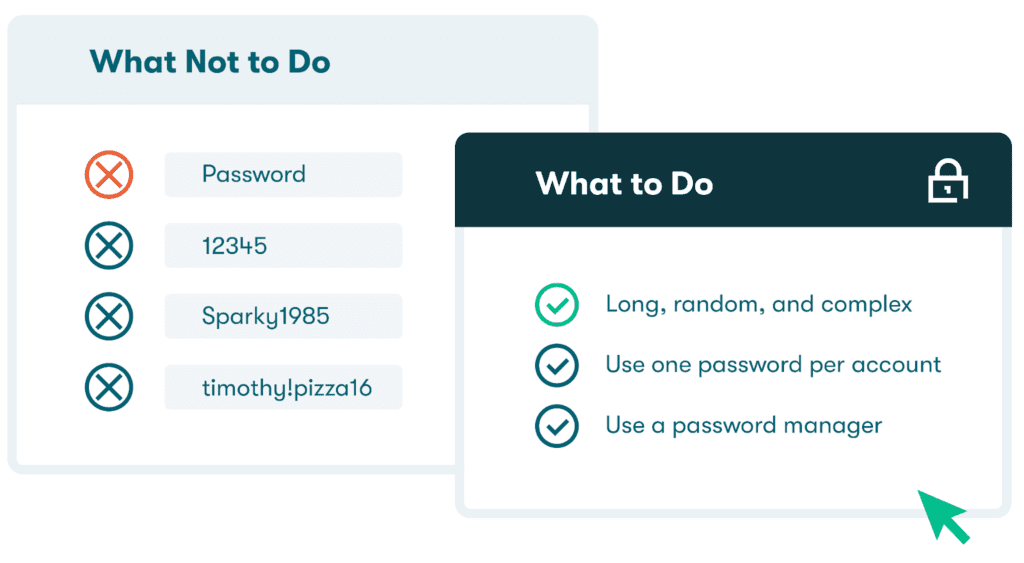
- Develop unique and secure passwords
Many common hacking tactics target weak and commonly used passwords since they can be guessed more easily, especially with the help of modern software tools. You can address this risk and learn how to prevent hacking by following some basic guidelines when you reset passwords or create new ones:
- Make passwords long and complex. Although there are no set rules for password length, it’s advisable to make them at least 12 characters long and avoid including any personal identifiers like your name, address, or phone number. You can make your passwords strong and unique by including a random mix of upper and lowercase letters, numbers, and special characters.
- Don’t reuse passwords: With so many accounts and passwords to manage, repeating old logins has become a common habit since we want to make our passwords easier to remember. Unfortunately, reusing passwords also diminishes password security, as multiple accounts can be impacted if a reused password is compromised.
- Encrypt passwords and other data
The practice of encryption, or hiding information in an unrecognizable format, dates back to ancient times. Encryption has also become a valuable website security and password protection tool in recent years as we consider how to prevent hackers from stealing information. Dashlane Password Manager utilizes AES-256 encryption, widely accepted as the strongest encryption type available, to protect passwords.
- Use secured internet connections
Public WiFi networks in airports, malls, cafés, and other unsecured locations are subject to man-in-the-middle attacks and other hacking tactics intended to intercept information. If you use a public WiFi network, you should use a VPN to secure the connection. A VPN will also mask your IP address so you can browse the internet privately.
- Install antivirus and anti-malware software
There are many effective antivirus software options available that continually scan your system for malware, then quarantine and remove any malicious files from your device. The best antivirus and anti-malware options keep up with the latest trends and tactics and provide cloud-based updates accordingly. The potential financial or privacy loss from spyware and ransomware attacks make antivirus software a wise investment.
- Don’t share passwords unsecurely with others
Sharing passwords unsecurely with friends, family, and coworkers is another common habit that plays into the hands of hackers. Shared passwords expose everyone in the group if any of them are impacted by a cybercrime. Since password sharing is common and often needed, you should always try to share passwords as securely as possible:
- Don’t use texts or Slack. Text messages and online communication platforms like Slack are popular information-sharing options. However, these methods don’t use encryption, and messages can be stored indefinitely, so they can be vulnerable to hacking and data breaches and should be avoided for password sharing.
- Use an encrypted sharing portal: The safest way to share passwords is by using the encrypted sharing portal of a password manager. Dashlane’s password-sharing tool can be used to share Secure Notes or logins with other Dashlane users.
- Regularly update your hardware and software
Software and hardware developers incorporate the latest security features into each new release. Hackers try to exploit out-of-date hardware or unpatched software and operating systems with known vulnerabilities. Completing system maintenance, keeping apps up-to-date, and applying recommended patches in a timely manner helps protect you from cybercrimes and strengthen your security position.
- Use a password manager and 2FA
A password manager provides hacker protection by encrypting passwords and account information, storing your logins in a secure vault, and keeping track of your weak, reused, and compromised passwords. Password generation features and autofill add convenience by eliminating the need to create and remember strong passwords for each new account. The best password managers also include 2-factor authentication (2FA), which requires a second identifier during login for an added layer of security.
How Dashlane keeps your online accounts secure
Dashlane helps you keep your passwords and other data safe from hackers. Standard features include 2FA, a detailed Password Health score, AES 256-bit encryption, and a secure password-sharing portal. Our Dark Web Monitoring continually scans the hidden recesses of the internet to ensure your logins and personal information remain uncompromised, while our patented zero-knowledge architecture ensures that no one (including Dashlane) can access your data. If Dashlane were ever hacked, the hackers would be unable to access your information without your Master Password.
Thankfully, white hat hackers like Rachel Tobac help us understand what the bad actors are up to and how to protect ourselves. Join us for an enlightening happy hour with a hacker.
References
- Sussex Chamber of Commerce, “What is a Bad Actor in Cyber Security?” February 2023.
- Dashlane, “Breaches & Alerts,” 2023.
- Dashlane, “How to Spot a Phishing Scam,” November 2019.
- Dashlane, “What the Hack is a Brute Force Attack?” February 2020.
- Microsoft, “Top 5 Most Famous DDoS Attacks,” February 2023.
- Dashlane, “What’s Your Number? How to Avoid Port-Out Scams,” August 2021.
- NIST, “Man-in-the-middle attack (MitM),” 2023.
- Dashlane, “Why Do You Need a VPN? Don’t Miss These 3 Key Benefits,” August 2020.
- Dashlane, “What the Hack Is Malware?” February 2020.
- Norton, “Spyware: What is spyware + how to protect yourself,” December 2021.
- Dashlane, “10 Most Common Passwords (Is Yours on the List?),” September 2022.
- Dashlane, “How Strong Is Your Password & Should You Change It?” August 2022.
- Dashlane, “How to Stop Reusing Passwords for Good,” January 2020.
- Thales, “A Brief History of Encryption (and Cryptography),” November 2022.
- Dashlane, “What Is Encryption?” March 2019.
- Security.org, “Do You Still Need Antivirus?” 2023.
- Dashlane, “Sharing Passwords Through Slack Is Risky,” November 2019.
- Dashlane, “Best Way to Store Passwords at Home or Work,” September 2022.
- Dashlane, “How Password Managers Work: A Beginner’s Guide,” December 2022.
- Dashlane, “2-factor authentication (2FA) in Dashlane,” 2023.
- Dashlane, “Happy Hour with a Hacker,” 2023.
- Dashlane, “How White Hat Hackers Help Dashlane Be More Secure,” October 2020.
- Dashlane, “How to Prevent Ransomware Attacks on Your Devices,” March 2023.
- Dashlane, “Why You Should Keep Your Apps Updated,” March 2022.
- Dashlane, “A Beginner’s Guide to Two-Factor Authentication,” August 2022.
- Dashlane, “7 Dangers of Sharing Passwords Without a Password Manager,” March 2023.
Sign up to receive news and updates about Dashlane
Thanks! You're subscribed. Be on the lookout for updates straight to your inbox.

